Survey: Doubt haunts federal employees following OPM data breaches
Federal employees and other security-clearance holders do not trust the Office of Personnel Management to protect victims of the hacks on its databases, an...
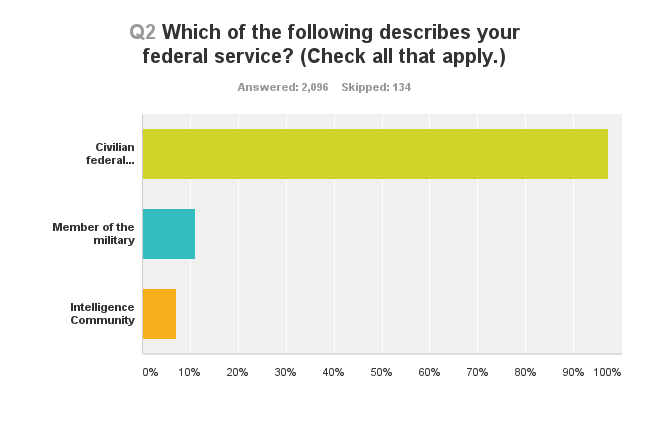
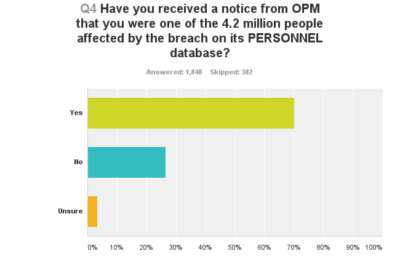
A total of 2,230 people responded to Federal News Radio’s online survey between July 16-21. All but 22 identified themselves as current or former federal employees or others who held federal security clearances. As such, some are likely among the 21.5 million victims of the hack on OPM’s security clearance system. Most of the respondents said they had received notice that their information was compromised in the smaller breach of OPM’s personnel system, which impacted 4.2 million people.
Less than 2 percent of respondents said they were very confident in OPM’s ability to provide the appropriate protections for victims of the breaches. More than three-quarters said they were not confident at all. The rest said they were somewhat confident.
“They couldn’t protect their data; I can’t see how they can provide any protection once the horses have left the barn,” commented Larry Brady, a security specialist at the Centers for Medicare and Medicaid Services in Windsor, Maryland.
“Two words: Clown shoes,” wrote a member of the intelligence community, who said they had held a security clearance since 1993. “This is a huge breach of trust with the workforce. I am considering leaving Federal Service over this.”
Respondents questioned the agency’s ability to identify victims. One wondered why they were the only person in their office who had not received a notice that their information had been compromised. Others doubted OPM had the technical expertise necessary to secure the data. One suggested that the CIA or FBI take over the responsibility of safeguarding individuals’ personal information.
Most respondents — 71 percent — said they blamed OPM’s entire IT team for the data breaches. More than half singled out the agency’s chief information officer, Donna Seymour, for blame. Yet they were more likely to point the finger at Congress than former OPM Director Katherine Archuleta.
“This problem started 20+ years ago. Archuleta and Seymour inherited the mess. Given the problems with firing entrenched bad apples it takes time to unwind things. They should not be blamed,” wrote a Homeland Security Department employee.
Archuleta has since been replaced by Beth Cobert, formerly the White House’s deputy director for management. Seymour remains at OPM.
Begrudging acceptance of identity protection services
Despite their misgivings, most survey respondents said they have taken advantage of the credit monitoring and identity theft protection services that OPM is providing to people affected by the breaches. Of those respondents who said they had not yet signed up for those services, nearly four out of five said they planned to do so or were at least thinking about it.
Yet many said they worried about sharing their personal data with the company that OPM had hired to provide those services.
“What do we do when the ‘credit monitoring service(s)’ get hacked? In my opinion they’re on hacker’s hit lists, too,” wrote Forest Service employee Mike Martischang.
The company, CSID, requires individuals to give it some personal information so that it can monitor financial statements and other sensitive records for signs of fraud. Yet cybersecurity experts said breach victims should think carefully before sharing that data, especially if it makes them uncomfortable.
“Some people — and I’m not saying whether it’s good or bad — some people are afraid that’s putting a heck of a lot of information in one place,” said Celia Paulson, an IT security specialist at the National Institute of Standards and Technology, during a Washington, D.C., event on cybersecurity awareness Tuesday hosted by GovLoop. “If that’s the case, you don’t have to. You can go to other places and do the same thing. You can do it yourself.”
When asked whether feds should enroll in the services, Paulson demurred, saying she could not give a recommendation from the government.
“But personally, I would not,” she added.
Kristina Dorville, the Homeland Security Department’s branch chief for cyber education and awareness, agreed.
“You’re paying for the convenience of someone doing it for you,” Dorville said. “You can say, every Saturday at 10 a.m., I’m going to go through and make sure my statements match up to what I know I purchased, which I know takes effort. There are also other services. I know CSID is being offered for free to federal employees, but if you’re concerned about the risk proposition, you could pay for a different service.”
A bipartisan group of lawmakers has raised questions about the value of credit monitoring and identity protection services to people whose information is already in hackers’ hands.
“According to experts, some credit monitoring services only monitor one of the three major credit bureaus, while criminals know to apply for credit at all three bureaus,” six members of the House Energy and Commerce Committee wrote in a letter requesting a study by the Government Accountability Office. “Experts have also questioned whether one to two years of credit monitoring offers sufficient protection since cyber criminals can use stolen personal information many years after monitoring services have expired.”
The lawmakers, led by Rep. Fred Upton (R-Mich.), the committee chairman, want the investigators to examine the array of services available to breach victims. They also want to know how the government determines whether such services are effective.
Doubts about OPM contractor CSID linger
Soon after being hired by OPM, CSID was struggling to keep up with the demand for its services. Customers reported hour-plus waits for telephone representatives. They complained about website problems as well. But when asked to rate the company’s service on a scale of one to five, 37 percent of survey respondents gave it a three.
CSID and its partner company Winvale have acknowledged the difficulties, but say they have resolved the issues. Callers were spending less that two minutes on hold as of Wednesday, said CSID President and Co-Founder Joe Ross. The website was functioning well, he said.
“Overall, the enrollment process has been quite smooth, especially considering the volume of individuals who have enrolled over a short period of time,” he said.
Regarding fears that CSID’s database could be hacked, he said the company uses a layered approach to safeguarding data. For example, CSID encrypts sensitive information such as Social Security and account numbers. That distinguishes it from OPM. The agency said it did not encrypt the Social Security numbers stolen from its personnel database. Obama administration officials said encryption would not have protected the information under the particular circumstances. The hackers gained entry to OPM’s system through legitimate credentials they stole from a third party.
Most survey respondents want lifetime credit monitoring
Despite the concerns about privacy and customer service, most survey respondents said they wanted more — not fewer — identity protection services. OPM has offered to pay for 18 months of services for victims of the breach on the personnel database. The agency said it will offer three years’ worth of services to those affected by the breach of the security-clearance database. More than 87 percent of survey respondents said that was not fair. Nearly 83 percent said all breach victims deserved to have those services for life.
Both the American Federation of Government Employees and the National Treasury Employees Union have sued OPM in the hopes that a court would force OPM to offer lifetime protective services. The Obama administration has not ruled it out. It is talking with the unions about the prospect of providing some sort of credit monitoring for all federal employees, said OPM spokesman Sam Schumach. But he said the policy was not finalized.
“You don’t want to lock yourself into something early and find out that it’s not right for the long term,” he said. “We are in a dialogue.”
Uncertainty about applying for a security clearance today
Applying for a security clearance is a time-intensive process. The most common application, Standard Form 86, includes more than 100 pages of questions. It asks applicants to reveal their past illegal drug use, their spouses’ Social Security numbers and sensitive information about acquaintances overseas.
Three out of 10 survey respondents said they would still go through the process to obtain or renew a security clearance, despite the data breaches. If their work required a clearance, they had no choice, they said. Yet just as many survey respondents said they would not apply for a clearance. About 40 percent said they were not sure.
“OPM obviously did not protect the background investigation data adequately even after they were aware of the security vulnerabilities that would enable outside agents to hack into the system,” wrote a Defense Department civilian employee who said they would still apply for a clearance. “Yet we do not have ability to refuse a background investigation as it is most likely a condition of [employment.] If I were starting off from college, I would have to seriously consider not applying for a Civil Service job and it may have even impacted on my decision to join the military.”
Yet Kelly Anderson, who works for the U.S. Agency for International Development, suggested that fears over the data breach were overblown.
“Assuming that your voluntary withdrawal from a single database will protect your identity at this point is naive. Why does something that has 100 percent chance of impacting your livelihood today (i.e., losing a job or job offer without a clearance) in order to avoid something else that has a minuscule chance of slightly inconveniencing you months or years ahead (i.e., the bad guys applied for a credit card using your social)?” she wrote.
Now that the breach has happened, she said, government leaders should focus on reducing federal employees’ fears and anxiety.
“They need to take leadership to show that they share their employees’ concerns, but at the same time, that this is the cost of doing business in 2015. It’s the trade-off we make for getting our paychecks to appear in our bank accounts as if by magic or our security clearances processed without paying postage,” she said.
Read all of Federal News Radio’s coverage of the OPM Cyber Breach.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories