

The Cybersecurity and Infrastructure Security Agency detailed the concept of trust zones under the final TIC 3.0 implementation guidance released last week.
Agencies now have three of the six documents needed to begin to move away from the old way of securing their networks—thus lifting the security albatross off their proverbial necks.
The Cybersecurity and Infrastructure Security Agency released on Friday the program guidebook, the reference architecture and the security capabilities catalog under the Trusted Internet Connections (TIC) 3.0 policy.
Taken altogether, these documents detail a modernized TIC program, define the program’s concepts and outline security capabilities that agencies should consider as they implement TIC 3.0.
CISA received more than 500 comments from agencies and industry on the draft documents it released in December. The Office of Management and Budget set the stage for agencies with the release of its final TIC 3.0 policy in September, finally updating the 12-year-old regulation.
The TIC 3.0 policy helps make it easier for agencies to move applications to cloud services by giving them a less prescriptive and more flexible approach to securing data and using the off-premise services.
“CISA anticipates the final core TIC 3.0 guidance will better address stakeholder needs and concerns. The guidance is expected to evolve to reflect technological advancements, changes in threats and the lessons learned from TIC pilots to help ensure its usefulness to federal agencies,” the agency stated in its response to the comments it received on the draft documents. “CISA is also committed to supporting agencies and continuously receiving feedback to aid in the development of future iterations of TIC guidance.”
CISA says it will release the final versions of the use case handbook, the overlay handbook and two uses cases for traditional TIC and branch offices later this summer. CISA gave agencies the third initial use case in April to help them address the surge in teleworkers.
From the comments, CISA identified five common themes, including alignment across cyber programs, support from DHS and more details and context for the terminology used in the documents.
“Several additional use cases have been proposed to CISA. CISA will coordinate with OMB, the General Services Administration and the Federal Chief Information Security Officer’s Council to prioritize and determine use cases to support after releasing the Traditional TIC Use Case and the Branch Office Use Case,” the agency stated. “The updated TIC guidance employs new architectural and security concepts to be more supportive of the latest technology and broad range of agency enterprises that will be adopting TIC 3.0. Agencies have accepted the new approach to TIC implementation, and the TIC program has received positive feedback on its increased flexibility and responsiveness to agency needs. Additionally, the number of security capabilities has increased to reflect the growing number of cybersecurity threats and adoption of cloud-based services.”
Another major update based on comments is around trust zones. CISA says it provided more information on the prerequisites, boundaries and criteria of trust zones. It also offered more clarity on trust inheritance in traffic between zones and policy enforcement points (PEPs).
“Within a trust zone, further segmentation is permissible, including segmentation to the network, application, or browser level. This can occur when there are both shared protections that are common across all entities within the trust zone and distinct capabilities that are applicable only to a subset of endpoints within that zone,” the reference architecture stated. “Agencies may use relevant factors for grouping endpoints, which could include client purpose, services, user roles, need-to-know, geography or other criteria.”
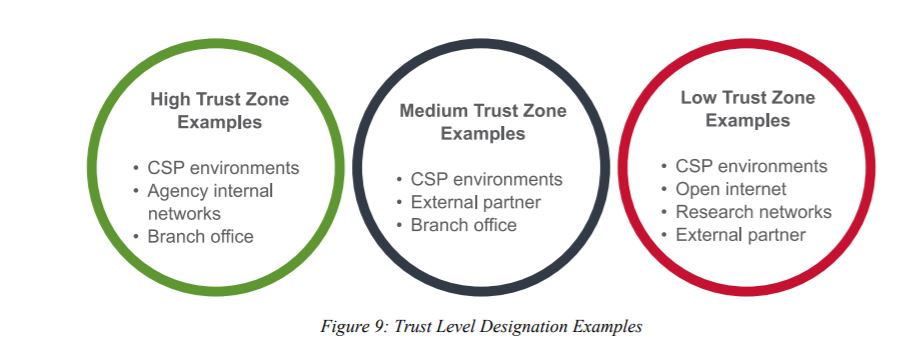
CISA also detailed three trust zones—high, medium and low—and sample considerations around controls, transparency and verification requirements.
“[A]n agency could determine that all cloud service providers (CSPs) should be designated as medium trust,” the document stated. “On the other hand, an agency could also categorize one CSP as medium trust and another as low trust based on unique circumstances, like stronger contractual terms that provide greater visibility into one of the CSPs.”
Additionally, CISA made major changes to the security capabilities catalog, formerly known as the Security Capabilities Handbook, specifically around building on the trust zones discussion in the reference architecture.
CISA says six criteria guide an agency’s risk-based decisions on which capabilities are best suited for the system. These include:
“TIC use cases will reference capabilities from this catalog and will provide guidance on how to deploy these capabilities within the context of a unique use case,” the catalog stated. “TIC overlays will provide mappings from these capabilities to vendor-specific tools and services. Over time, this catalog will be updated and will be informed by TIC pilot activities, TIC use cases, emerging technologies and threat insight.”
The still pending documents will include further updates to the use cases specifically focused on the relationships and data flows between trust zones and capability deployment. CISA also will try to clarify how “real world” networks align with use cases such as the scoping around cloud service providers (CSPs), PEPs and trust levels.
Just getting this first set of documents out helps agencies and vendors alike begin the transition to TIC 3.0, but it’s still the beginning of the process. The question always remains, how fast can CISA and agencies move and still remain secure?
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED

