
OMB sets new CDM data standards deadline for agencies
Senate lawmakers want to add $40 million to the continuous diagnostics and mitigation (CDM) program in fiscal 2021 for a total of $325 million.
As with any discussion about cybersecurity, let’s start with the good news.
The Office of Management and Budget continues to live up to its promise to keep new requirements under the Federal Information Security Management Act (FISMA) at a minimum to ensure consistent measurement from year-to-year.
The latest memo from OMB Director Russ Vought outlining requirements for fiscal 2021 is exactly the same as the 2019-2020 memo except for a section about the continuous diagnostics and mitigation (CDM) program.
“At a minimum, Chief Financial Officer (CFO) Act agencies must update their CIO metrics quarterly and non-CFO Act agencies must update their CIO metrics on a semiannual basis,” Vought wrote. “Reflecting the administration’s shift from compliance to risk management, as well as the guidance and requirements outlined in OMB Memorandum M-19-03, Strengthening the Cybersecurity of Federal Agencies by Enhancing the High Value Asset Program, and Binding Operational Directive 18-02, Securing High Value Assets, CIO metrics are not limited to assessments and capabilities within National Institute of Standards and Technology (NIST) security baselines, and agency responses should reflect actual implementation levels. Although FISMA requires an annual IG assessment, OMB strongly encourages CIOs and IGs to discuss the status of information security programs throughout the year.”
While OMB is pushing agencies to continue to take a risk-based approach to cybersecurity, it set a new deadline under the CDM program—the one “major” change to this year’s FISMA guidance.
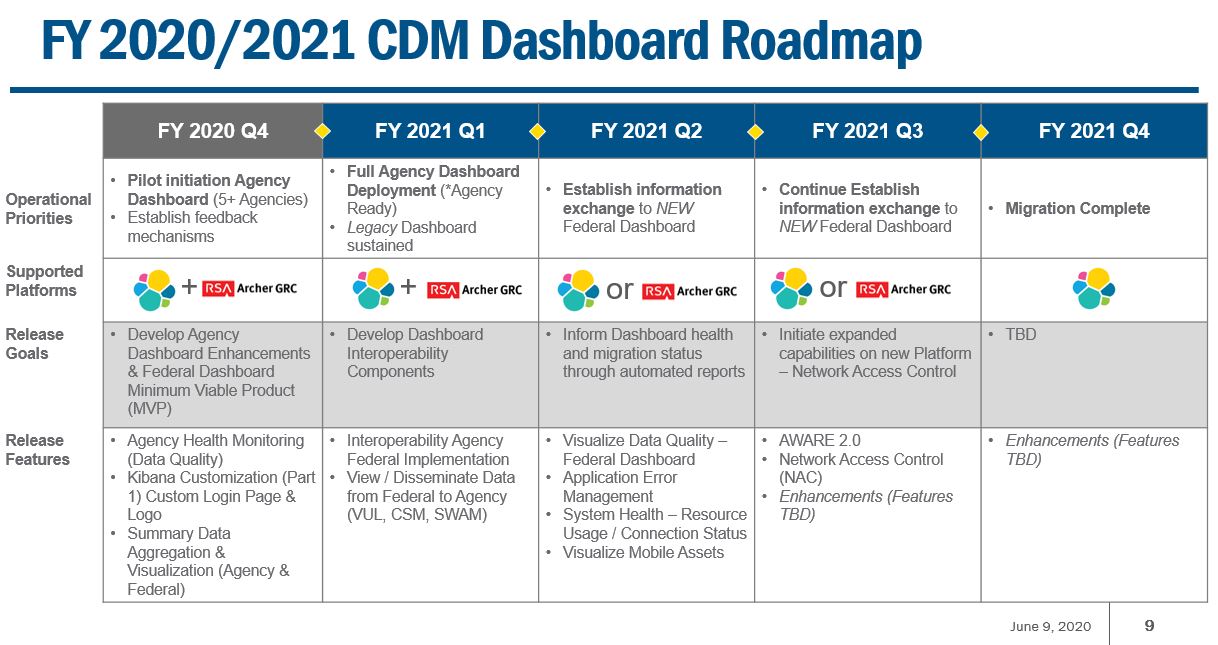
By the end of fiscal 2021, agencies must certify to OMB and the Cybersecurity and Infrastructure Security Agency (CISA) in the Department of Homeland Security that they have implemented the CDM Program Data Quality Management Plan (DQMP) and can be “fully able to exchange timely data to the federal dashboard.”
“CFO Act agencies unable to meet this target date must provide a written justification to both OMB and CISA,” the memo states. “Additionally, the CDM program management office and participating non-CFO Act agencies will work together to ensure that all participating non-CFO Act agencies establish information exchange between their respective dashboards and the federal dashboard by the end of the end of [fiscal 2021].”
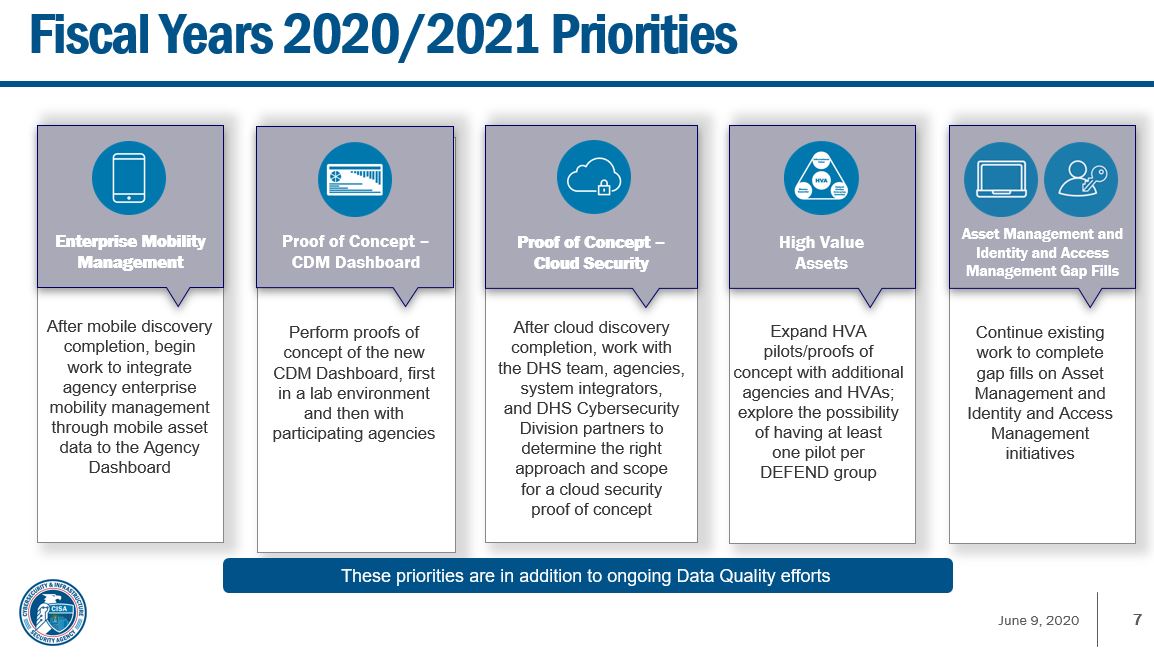
Kevin Cox, the CDM program manager at CISA, said during an event in June that the CDM data management team defined “enhanced data requirements, including completeness, accuracy, and timelines for CDM solutions.”
Cox said at the event CISA gave agencies and system integrators the data quality plan earlier this year that details the data management team’s findings and it includes a “CDM Data Certification Rubric which uses a combination of quantitative and qualitative criteria to certify summary data.”
As of June, Cox said 69 non-CFO Act agencies were participating in CDM and 52% of those had already started exchanging data with the federal dashboard, and another 23% were in deployment or pre-deployment. All CFO Act agencies already have implemented the dashboard.
OMB and CISA are rolling out the new agency and federal dashboard throughout 2021 under a $276 million contract with ECS awarded in May 2019. CISA is piloting the new dashboard with 15 agencies in 2020 and then will expand to the rest of the large agencies throughout 2021.
“CDM brings a couple of things to the table. It provides tools to collect the data necessary to have full situational awareness, telling agencies who and what are in their networks. The second is having that capability to collect and identify that data, and then being able to put it on your agency dashboard so you can operationalize the data and take appropriate actions. The third is it gives OMB and DHS oversight of program and the ability to do an enterprisewide risk assessment of the government,” said Grant Schneider, the former federal chief information security officer and now a senior director of cybersecurity services at Venable. “Those tools, taken together, have been providing value at the tactical level.”
Schneider said as agencies implement the data quality plan, OMB and CISA will add clarity to what types of data are shared with the federal dashboard.
“Some agencies have concerns about how their data will be shared and how it will be used, especially in an oversight or budget way,” he said. “The data quality plan will add some transparency about what the data elements look like and ideally it will lay out the use cases on how DHS and OMB will leverage the data.”
The consistency and standardization piece is huge for agencies, OMB and CISA as part of the broader cybersecurity effort.
Erik Floden, director of federal civilian government at Forescout Technologies, said the data quality plan can help make up for those agencies that continue to struggle with asset management.
“Some of the agencies are using capabilities that are not able to detect all of the assets on their networks. Those agencies’ data are, therefore, not baselined correctly because the data does not necessarily reflect their true IT environments,” Floden said. “The CDM Technical Capabilities Requirements Catalog stipulates that for the purposes of CDM reporting, all Internet Protocol (IP) addressable devices are in scope. Some agencies’ CDM architectures allow them to report complete data, but many are unable to do so. If agencies are not reporting complete data, this seriously impedes the ability of the agencies and CISA to make the risk-based decisions that they are supposed to.”
Schneider added OMB and CISA have been striving for consistency across the CDM program since it really began. He said the FISMA guidance re-emphasizes the need to measure progress and create trend lines over time.
“This is important for OMB and CISA to perform oversight of agencies’ cyber programs and the ability to perform the enterprise risk assessment across government,” he said.
The other reason for making the data standards part of the FISMA guidance is CISA realized standardizing across tools was too difficult, but data shouldn’t be.
Floden said the wide assortment of tools impacts the quality of the data sent to the dashboard.
“For example, many agencies deployed particular tools that helped them discover an average of 75% more devices connected to their networks than previously known. Other agencies tried to accomplish asset discovery and identification utilizing existing tools or other alternatives that, frankly, do not allow them to discover all of the devices connecting to their networks,” he said. “Agencies that are unable to identify such a large percentage of devices that are on their networks firstly face serious cyber risk, and, secondly, will necessarily lack confidence that their reporting reflects their true IT environments. CDM was designed to give federal agencies flexibility in how they meet CDM requirements, however, they may have been given too much license to select tools or stay with existing tools that, in aggregate across the federal enterprise, do not really meet the overall needs or objectives of CDM.”
The priorities for CDM like the data quality plan continue to gain support from Congress.
The Senate Appropriations Committee allocated $325 million for CDM next year, which is $44 million more than the administration requested and $43.6 million more than in 2020.
“Due to a significant increase in malicious cyber attacks against Federal agencies, including Department of Health and Human Services’ computer networks in fiscal year 2020, the committee recommends $40 million above the amount requested to strengthen the resiliency of federal networks to malicious cyber events,” the explanatory report states about the increase in procurement funding.
The Senate also increased the operational support budget by $4 million for 2021.
This is $40 million more than the House version of the bill as well.
“CISA can do more to assist agencies in using CDM tools. CISA is encouraged to ensure agencies have the training and information necessary to fully leverage their CDM capabilities, to include guidance on best practices, sample architectures, and downloadable security policy sets,” the House report states.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED
Related Stories

75 small, micro agencies to have access to advanced cyber services under new award





