
‘Timely versus accurate’ DoD struggles shed light on cyber incident reporting challenges
DoD and its contractors are still struggling to share timely, accurate information about cyber incidents peppering their networks.
The Defense Department has fewer reported cyber incidents today than it did seven years ago, but DoD cybersecurity organizations and defense contractors are struggling to share timely, accurate information about those events, according to a new report from the Government Accountability Office.
GAO’s report sheds light on the challenges DoD faces in sharing information about network intrusions and other cyber events as cybersecurity remains a perennial top management challenge for the Pentagon. It also comes at a time when the Biden administration is developing new rules that will require critical infrastructure sectors to report cyber incidents to the government.
DoD reported more than 12,000 cyber incidents between 2015 and 2021, the report shows. However, the number of reported incidents dropped off starkly in recent years. In 2015 alone, DoD reported 3,880 cyber incidents in 2015. But in 2021, the department reported just 948 incidents.
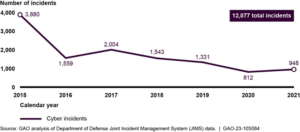
Jennifer Franks, director of GAO’s IT and cybersecurity team, said the finding correlates with how DoD and other agencies have improved their perimeter defenses and intrusion detection technologies over the past seven years.
“They have increased their perimeter detection mechanisms, they have increased their workforce, and the talent that it takes to provide forensic analyses for the incidents and provide those continuous monitoring services,” Franks said in an interview.
“But where they’re lacking really is in that information sharing,” she added.
The report shows DoD’s cybersecurity service providers — a group of 26 organizations across the military services and defense agencies tasked with defending DoD networks — often failed to enter complete information about cyber incidents into the Joint Incident Management System, also known as JIMS, the official system for recording all cyber incidents in DoD.
For instance, 91% of incidents reported in JIMS between 2015 and 2021 didn’t include the discovery date of the incident, while 68% of the reports didn’t include information on an incident’s delivery vector, “limiting DOD’s ability to identify trends in the prevalence of various threats affecting its networks,” GAO wrote.
Two of the CSSPs were responsible for 69% of the reports filed in JIMS, GAO found. But those two service providers, which the report did not identify, told GAO they didn’t enter information into JIMS the until after the incident was resolved.
And in 47% of the cases reported, there was no indication that DoD leaders were notified of the event.
GAO recommended DoD give someone the responsibility for ensuring defense components accurately and fully report cyber incidents to JIMS within prescribed time frames.
“Until DOD assigns responsibility for ensuring complete and updated incident reporting and proper leadership notification, the department will not have assurance that its leadership has an accurate picture of its posture,” the report states. “As a result, the department may miss opportunities to assess threats and weaknesses, gather intelligence, support commanders, and share information.”
Defense industrial base cyber struggles
The report also shows defense contractors struggling to accurately and swiftly report cyber incidents to the DoD Cyber Crime Center (DC3). The Pentagon developing new cyber rules for defense contractors under the Cybersecurity Maturity Model Certification program.
DC3 received more than 1,500 mandatory incident reports from defense contractors between 2015 and 2021, according to GAO.
But about one in five of those reports failed to show whether sensitive DoD information was implicated as part of the incident. And 55% of the reports didn’t indicate whether the incident resulted in a successful compromise of the network or not.
Defense contractors are required to report cyber incidents to DC3 within 72 hours. But GAO estimates 51% of the reports between 2015 and 2021 were submitted more than four days after discovery. One in five reports was submitted more than 20 days after the incident was discovered, GAO added.
DC3 officials told GAO that it’s often difficult to determine the specifics of a cyber incident within three days.
They also told GAO it’s typically more important to get “complete information,” rather than receiving reports as quickly as possible. But DC3 acknowledged that some cyber incidents need to be reported as soon as possible, such as those that could affect the contractor’s ability to provide critical services to the military
“You can have a debate, and we certainly heard it when we did this work, about the value of timely versus accurate,” Joe Kirschbaum, director of GAO’s defense capabilities and management team, said in an interview. “Is it better to have information that’s accurate, that’s complete, versus as quickly as possible, as timely? And the unfortunate answer is, ‘It depends.’ It depends on the incident.”
Cyber incident reporting mandates
GAO’s look into DoD’s cyber incident management challenges comes at a time when the Department of Homeland Security is writing new rules that will require all critical infrastructure sectors to report significant cyber incidents to the Cybersecurity and Infrastructure Security Agency.
“We’re talking about information sharing and or the lack of information sharing — all of those types of criteria need to be applied effectively across the federal government so that we all can be better prepared to detect and then respond to the cyber vulnerabilities that are impacting all of our agencies,” Franks said.
Chris Ballod, managing director in the cyber risk practice at Kroll, said it’s difficult to standardize requirements for reporting incidents.
“Many challenges arise during the assessment of an incident situation such as the time it takes to resolve technical complications sufficiently to investigate the specific forensic artifacts needed to complete the analysis of potential data at risk,” Ballod told Federal News Network. “Further complexity is added by potential civil liability and the patchwork of regulations and obligations that exist across different jurisdictions. Privilege often dictates what will get reported and when, which may conflict with what is deemed ideal from an incident reporting perspective.”
But in DoD’s case, GAO offered a number of recommendations to help improve the processes across DoD’s vast internal network and for the thousands of defense contractors who handle sensitive information.
The report recommends DoD issue new guidance to its components on cyber incident reporting, including “detailed procedures for identifying, reporting, and notifying leadership of critical cyber incidents.”
GAO also recommends U.S. Cyber Command examine whether certain defense industrial base-related cybersecurity incidents could be relevant to the missions of DoD components so it can identify “when and with whom such information should be shared.”
The report additionally urges Pentagon have the DoD chief information officer review “what actions need to be taken to encourage better mandatory cyber incident reporting from DIB companies.”
The issue ultimately comes down to DoD better aligning its incident reporting procedures and mechanisms, Kirschbaum said, with what officials need to accomplish their cybersecurity missions.
“In order to really do effective cybersecurity, for DoD to get cyber management under control, it’s a matter of getting the right information to the right people at the right time,” Kirschbaum said.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Follow @jdoubledayWFED
Related Stories
‘Timely versus accurate’ DoD struggles shed light on cyber incident reporting challenges

Cyber accreditation body says key CMMC document to face changes




