
Insight by Okta
Zero Trust Cyber Exchange: Why context matters when it comes to zero trust maturity
When the network is no longer the boundary for managing secure access to an organization’s data, what is the perimeter? It’s context, said Sean Frazier, federal...
When the network is no longer the boundary for managing secure access to an organization’s data, what is the perimeter?
It’s context, said Sean Frazier, federal chief security officer at Okta. And that context — who, what, where, why and how a verified identity wants to gain access to an agency’s network, systems and data — is fundamental to zero trust, he said.
As context changes, whether that’s something about the user, something about the device or something about the location, then automated cloud-based identity access management can validate the context and allow or deny access in real time, Frazier said.
Applying multiple context facets for zero trust
“For example, the Okta Identity Cloud looks at the context of every request to gain access and determines if it’s a valid or bad request. If it’s bad, we shut it down right away,” he said. “What’s critical is that context-aware access determinations happen at wire speed so there’s no friction for an agency’s end users but lots of friction for bad actors.”
From Okta’s perspective, context-aware access provides an organization the ability to protect the modern perimeter, essentially anywhere from which a user chooses to interact with the organization digitally. While cloud adoption by agencies had slowly been moving the government away from the idea of deploying just network-centric security tactics, the COVID-19 pandemic brought the context need into sharp relief, Frazier said.
“Suddenly, in a matter of days, all versus some of federal users were everywhere and what, when and how context factors expanded exponentially,” he recalled.
Verifying more than who proves key to zero trust
In the cyber future envisioned for the government in the White House Zero Trust Strategy, context comes into play in multiple ways once an organization has established unified identity credentials for access management, Frazier said.
Okta contextual access management incorporates five contexts:
- App context: What applications is a user seeking to access? Is this typical? Does the use of this specific app expose the organization to new threat vectors?
- User context: Who is seeking access? Are they a member of a high-risk user group?
- Network context: Is this a new IP address? Is the user disguising their IP address?
- Device context: Is this a new device? What is its security posture?
- Location context: Has the user accessed agency systems from the location before? Is it physically impossible for the user to have traveled to the location in the time available since they last accessed the network?
Agencies can further refine their access policies based on the context information. As an example, an agency might allow seamless access to verified identities using managed devices but require verified identities using unmanaged devices logging in from new locations to provide multifactor authentication, Frazier said.
“Layering in context-aware access management represents a step up in zero trust maturity. In our model, this equates to Stage 2 maturity,” he said.
Okta’s 4 stages of zero trust maturity
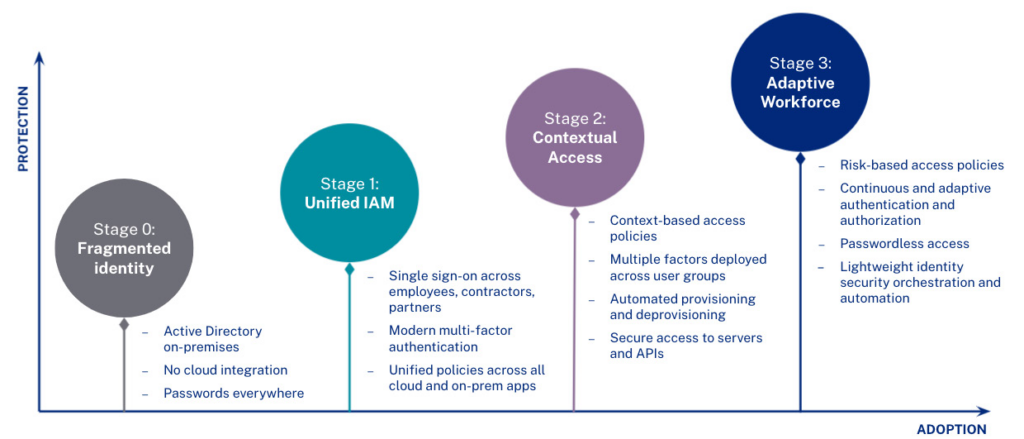
SOURCE: “Getting Started with Zero Trust Access Management,” Okta, August 2021
Ultimately, the use of context access management creates a faster and smoother security verification process for users, Frazier pointed out. “Contextual access management helps both the user and the security team because it will only ask for a second factor if someone attempts a risky authentication — not every time that user logs in.”
Like all verification practices in a zero trust architecture, context-aware access verification must be recurring so that an agency can identify and act on anomalous behavior in real time, he added.
“It’s exciting to help agencies on their zero trust journeys — providing the foundation for secure identity and context-aware access that will help the government protect its modern perimeter,” Frazier said.
To watch a session featuring Okta’s Sean Frazier during the 2022 Federal News Network Zero Trust Cyber Exchange or to watch other zero trust sessions, go to our on-demand event page.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories





