
CISA’s still overcoming challenges 5 years after Cybersecurity Information Sharing Act became law
The Cybersecurity and Infrastructure Security Agency will offer its Automated Information Sharing (AIS) program and new vulnerability disclosure platform as shared...
This month is the fifth anniversary of the Cybersecurity Information Sharing Act. The law made it easier for companies to share cyber threat information without fear of liability or consequences.
The law gave the Homeland Security Department top and bottom cover to make two-way sharing more than just talk.
Despite the thirst for cyber threat information only growing and the increase in private sector providers, the Cybersecurity and Infrastructure Security Agency continues to put the pieces in place to meet the spirit and intent of the law.
Two of the most recent examples are a new contract for a vulnerability disclosure platform (VDP) and a recent inspector general report on the Automated Information Sharing (AIS) that reads like so many other auditor reports: progress made, more progress needed.
“CISA has increased the number of AIS participants as well as the volume of cyber threat indicators it had shared since the program’s inception in 2016. However, CISA has made limited progress improving the overall quality of information it shares with AIS participants to effectively reduce cyber threats and protect against attacks,” auditors wrote. “CISA’s lack of progress in improving the quality of information it shares can be attributed to a number of factors, such as limited numbers of AIS participants sharing cyber indicators with CISA, delays receiving cyber threat intelligence standards, and insufficient CISA office staff. To be more effective, CISA should hire the staff it needs to provide outreach, guidance and training.”
The AIS program has struggled to live up to its promise for much of the past four years. The IG report, once again, explained why, but provided some reasons to be excited.
For instance, the IG said CISA shared 673 classified threat indicators with non-federal entities in 2017, and nearly 2,000 in 2018, as well as more than 5.4 million unclassified indicators with federal and non-federal entities. It also granted 129 security clearances to private sector partners in 2017, and 155 in 2018. In total, CISA maintained 1,536 active security clearances in 2017, and 1,691 in 2018.
“CISA increased the number of non-Federal participants by more than 195 percent — from 74 in 2016 to 219 in 2018, including 13 international computer emergency response teams,” the report stated. “On the other hand, the number of federal participants remained fairly steady, with only a 10 percent increase— from 30 entities in 2016 to 33 in 2018.”
While the quantitative metrics have all been going in the right direction in 2017 and 2018, the qualitative metrics show AIS remains a work in progress.
The IG stated, “11 of 17 participants (five Federal and six private sector) said the indicators lacked contextual/background data for determining the appropriate course of action to mitigate threats against their networks. Additionally, some participants stated that some indicators received were false positives or unusable information.”
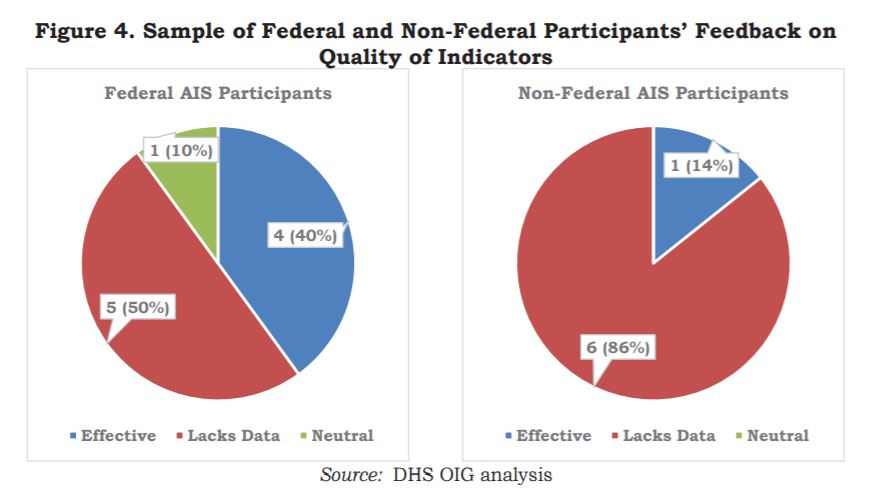
Auditors say a big reason why the threat data isn’t as valuable as it could be is the limited number of participants sharing with CISA.
“Although CISA increased the number of AIS program participants (information consumers) by 142% between 2016 and 2018, this did not equate to an increase in the number of information producers. According to program officials we spoke with, the number of program participants using the AIS capability to share cyber threat indicators is minimal,” the report stated. “For example, CISA has experienced only a slight increase in data producers sharing their cyber threat indicators and defensive measures using AIS during the past two years. Specifically, only 2 of 188 AIS participants (1%) shared cyber indicators with CISA in 2017, and only 9 of 252 participants (3%) shared indicators in 2018. Without more information producers, CISA cannot improve the quality of information it shares under the program and AIS participants remain restricted in their ability to effectively mitigate evolving security threats and vulnerabilities.”
CISA responded to the IG report with several initiatives, including relying on the Cybersecurity Quality Services Management Office (QSMO), in which AIS will be highlighted and promoted as a shared service.
AIS will not be the only shared service offered by the QSMO.
The General Services Administration awarded a five-year, $13 million contract on behalf of CISA to a women-owned small firm to build a vulnerability disclosure platform.
Under the contract, Endyna will create a centralized database that agencies can use to report, discover and take actions against cyber threat information. The QSMO will offer the platform as a shared service so agencies can meet the September Binding Operational Directive (BOD) calling for the use of a VDP platform.
CISA says the platform will promote good-faith security research, hopefully resulting in improved security and coordinated disclosure across federal civilian agencies.

In a fact sheet, CISA says the software-as-a-service platform will be the primary point of entry for vulnerability reporters to alert participating agencies of issues on the agency’s internet accessible systems. Agencies will be responsible for addressing the identified vulnerabilities.
All of this focus on cyber threat sharing isn’t lost on some lawmakers. The value of the data should be driving investment decisions, according to Sens. Rob Portman (R-Ohio) and Gary Peters (D-Mich.).
The lawmakers introduced the Risk-Informed Spending for Cybersecurity (RISC) Act that would require agencies to make investment decisions for cybersecurity tools based on a new risk-based budgeting model. The bill calls on the Office of Management and Budget to develop that methodology.
“Through the budget process, agencies make decisions about the tools they need to ensure they are addressing risks and closing capability gaps. Too often, insufficient information about threats and their associated risks inhibits their ability to make the best, most informed decisions,” Portman said in a statement. “It is crucial that federal agencies know the return on investment for each cybersecurity capability acquired and whether those capabilities address existing security vulnerabilities. This bipartisan legislation will help give federal agencies the information they need to make informed decisions about their cybersecurity budgets.”
Peters called the bill “common sense legislation” that will ensure agencies invest in cybersecurity defenses to guard against the variety of attacks they face.
The bill is partly based on OMB’s 2018 Cyber Risk Determination report that provided a governmentwide view of the process by which agencies address threats and set a baseline to improve upon.
Matt Cornelius, a former OMB senior technology and cybersecurity advisor and now the executive director of the Alliance for Digital Innovation, an industry association, said in a statement that the bill will help agencies develop a data driven, risk-based process for cyber investments.
“The bill would push agencies to leverage better intelligence, data and real time information to provide a more robust understanding their current cybersecurity performance and to improve the budget and appropriations process to ensure agencies have the resources they need to mitigate critical threats and vulnerabilities,” he said.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED





