

The Cybersecurity and Infrastructure Security Agency’s continuous diagnostics and mitigation (CDM) program is planning to expand the capabilities of the agency...
The continuous diagnostics and mitigation (CDM) program turned 10 years old last month. And what a long strange trip it has been.
As agencies move toward zero trust and continue to face an ever changing cyber threat, it’s clear CDM has hit its stride.
Now the Cybersecurity and Infrastructure Security Agency is positioning the program to bring a level of visibility and proactive response the original framers of CDM only dreamed of back in 2012.
“CDM was built on continuous monitoring that had been mandated under the Federal Information Security Management Act (FISMA) of 2002. Continuous monitoring was a thing. People talked about it. They did it. But they did it in lots of different ways across the civilian agencies. They did it with very little automation. There was certainly no central visibility. Agencies did it in different ways within their components or their elements,” said Betsy Kulick, the deputy program manager for CDM, at the recent FCW CDM Summit. “Most people relied on manual inventories at the end of the year and spreadsheets that offered a picture in time. There was not much beyond that in terms of accuracy, to say nothing of telling you how well protected at that particular endpoint or device. So there were people at the State Department, wise people at the Office of Management and Budget as well as in Congress that thought that automating it would be the smart way to move and that the state of the industry was such the tools existed that would allow us to do that. We were funded in 2012 to begin to try to standardize mainly continuous monitoring as the first effort in terms of device management, but ultimately, to go through the whole NIST (National Institute of Standards and Technology) Special Publication 800-53 controls to automate that, to the extent possible to provide a far more secure way of securing the federal civilian networks. It was an ambitious program, we knew we’d been working at this for 10 years.”
And 10 years later, the CDM program, warts and all, is widely considered a success.
The Department of Homeland Security launched the program in 2012 making awards to 17 companies with a $6 billion value.
The idea was borrowed by the State Department, which set up a system of continuous monitoring and alerting of hardware and software vulnerabilities.
DHS updated the program in 2017 to its current approach that focused on using system integrators to help groups of agencies with similar needs or in similar places implement approved products to fill in specific cyber gaps.
Since 2017, agencies have been receiving at no charge a series of tools and capabilities to get more visibility into their networks through asset, identity, data security and network protection management tools. CISA also provides a dashboard at both the agency level and one that provides data to create a governmentwide picture for CISA .It also helps small and micro agencies with a shared services platform.
The decade of CDM has been far from smooth. Industry protested task orders. Agencies expressed frustration on several occasions about delays in getting key toolsets. DHS ran into bureaucratic, regulatory and legislative obstacles that needed to be cleared. And then there is the ever-present culture change aspect of trusting CISA to help, but not judge individual agency cybersecurity efforts.
But despite a dozen years of challenges, CDM has consistently found support from multiple administration and from Congress.
Congress has been unusually supportive of CDM and really CISA more broadly when it comes to federal cyber networks. Since 2012, DHS has received more than $2.36 billion specifically for CDM, which also included a sizable chunk of the $650 million CISA received from the American Rescue Plan Act. CISA hopes to receive another $4 billion through 2033 to continue to run and evolve the program.
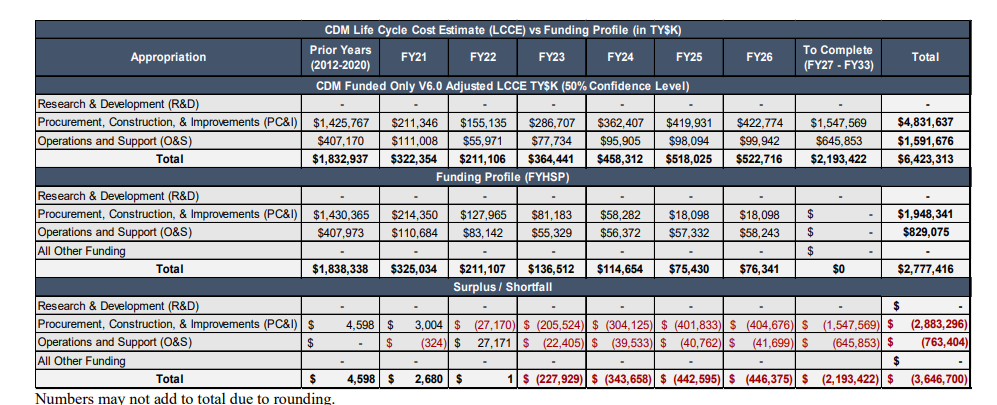
So what did all that money get?
CISA says the foundation for better more proactive cyber defense is coming into place.
Richard Grabowski, the deputy CDM program manager, said agencies are seeing real value from some of the work that CISA has led over the last year plus.
“Everything that we’ve been doing over the last 16 months and in the near term are going about building that collaborative defensive posture. So you see what we see, we can make very helpful recommendations that you can triage and take back at machine data speed,” Grabowski said. “We’ve made investments in the Elastic search tool, in technologies for end-point detection and response (EDR), helping you get in front of mitigation, coverage making sure that every and all shadow IT has some amount of spotlight on it, and then bringing into other asset classes like mobile.”
The CDM toolset has come in handy during every cyber threat and incident agencies have faced over the last five years. Whether it was the WannaCry ransomware attack or Log4J or any number of threats, agencies and CISA can turn to the dashboard from Elastic to discover more complete data more immediately.
Judy Baltensperger, the project manager for the CDM dashboard at CISA, said the dashboard has come in especially handy to help address requirements in recent binding operational and emergency directives that CISA put out to the agencies over the last two years such as after the SolarWinds and the Log4J cyber incidents.
“We were able to share with them what CDM data is actually available, and what kind of automated reporting can we feasibly do. I don’t think people realize how expansive the dashboard is,” she said. “We have about 89 dashboards deployed, 78 of them reporting data. We do have a large amount of coverage across the network now, and we were now at the point where that synergy came together.”
Baltensperger added the dashboard has impacted agencies’ ability to meet specific compliance requirements and address long-standing cyber hygiene challenges such as patching and asset management.
There are several new capabilities coming to agencies from CDM to improve this proactive and collaborative defense posture.
Baltensperger said one of them is something called cross cluster search that will give CISA an even deeper look at health of agency networks, which came in handy during a recent cyber threat, something called open SSL3, considered a high risk vulnerability.
“What that gives us here, this is a federal level is object level data visibility into the dashboards. So as of this moment, we have about 20 dashboards out of the 78 that we have this object level data visibility,” she said. “Starting several days ago, last Friday (Oct. 28), we were able to then with that object level data, deep dive down to what was being scanned. Within the ecosystem, we have more visibility than we have ever had in the past. That’s expanding with our implementation and enablement of cross cluster search. But that needs to improve. But that’s a significant improvement.”
Baltensperger added CISA expects to expand this cross-cluster capability to more agencies in 2023 because it provides a level of automation of information collection that will accelerate when agencies know if they have a vulnerability so they can remediate it and reduce their risks.
Additionally, CISA will upgrade all agency dashboards to version 6 and a new service under the dashboard to help agencies identify when they are using end of life products or are getting close to end of life so they can replace them and reduce cyber risks.
Finally, Baltensperger said another capability that is gaining momentum is around dashboard-as-a-service.
“If an agency does not have their own hosting environment and they would like to pass that on to us, our team can do that for a significant cost savings of about $80,000 to $100,000 per dashboard. What we can do is on our side is provide you access to that dashboard. So that means the product gets paid for, all the infrastructure gets paid for, the storage gets paid for because we are managing a similar type product and we’re able to repurpose our labor,” she said. “We’ve gotten much more efficient with the number of people that it takes to operate and maintain and upgrade that particular solution because we basically built a shared service off on the side, and we can offer it to all the agencies.”
Currently, five CFO Act agencies are using the dashboard-as-a-service and another seven or eight plan to join in 2023.
“What that means is their dashboard is moving out of their system boundary and we are hosting it on their behalf. Now the data still belongs to them. They’re still responsible for the data. But all of the burden of operating, maintaining patching, keeping up with the operating system patches, figuring out if you are susceptible to OpenSSL, all of that work is coming over to our team, and we’re already doing it for ourselves,” she said. “What we’re doing is just extending it to the agencies. But it means that we’re funding the infrastructure. And because we’re funding the infrastructure out in the cloud in a shared service manner, we’re able to realize cost savings.”
Shared services, cost savings and most importantly, better cybersecurity, those were the initial goals and vision for CDM. No one would claim this was an easy path and CDM is far from perfect, but it’s clear agencies are better off because DHS, the State Department, OMB and a host of visionaries took a collective leap into the cyber unknown.
It’s not often the government celebrates program successes, especially cybersecurity initiatives. But CISA, OMB and every agency should take a moment, offer a smile or two and delight in what they have accomplished through CDM over the last decade.
And I hope CISA at least had some cake to mark the anniversary and all that is good about the continuous diagnostics and mitigation program.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED


