Insight by Eclypsium
A CMMC Approach to Address Firmware Vulnerabilities and Ensure Device Integrity
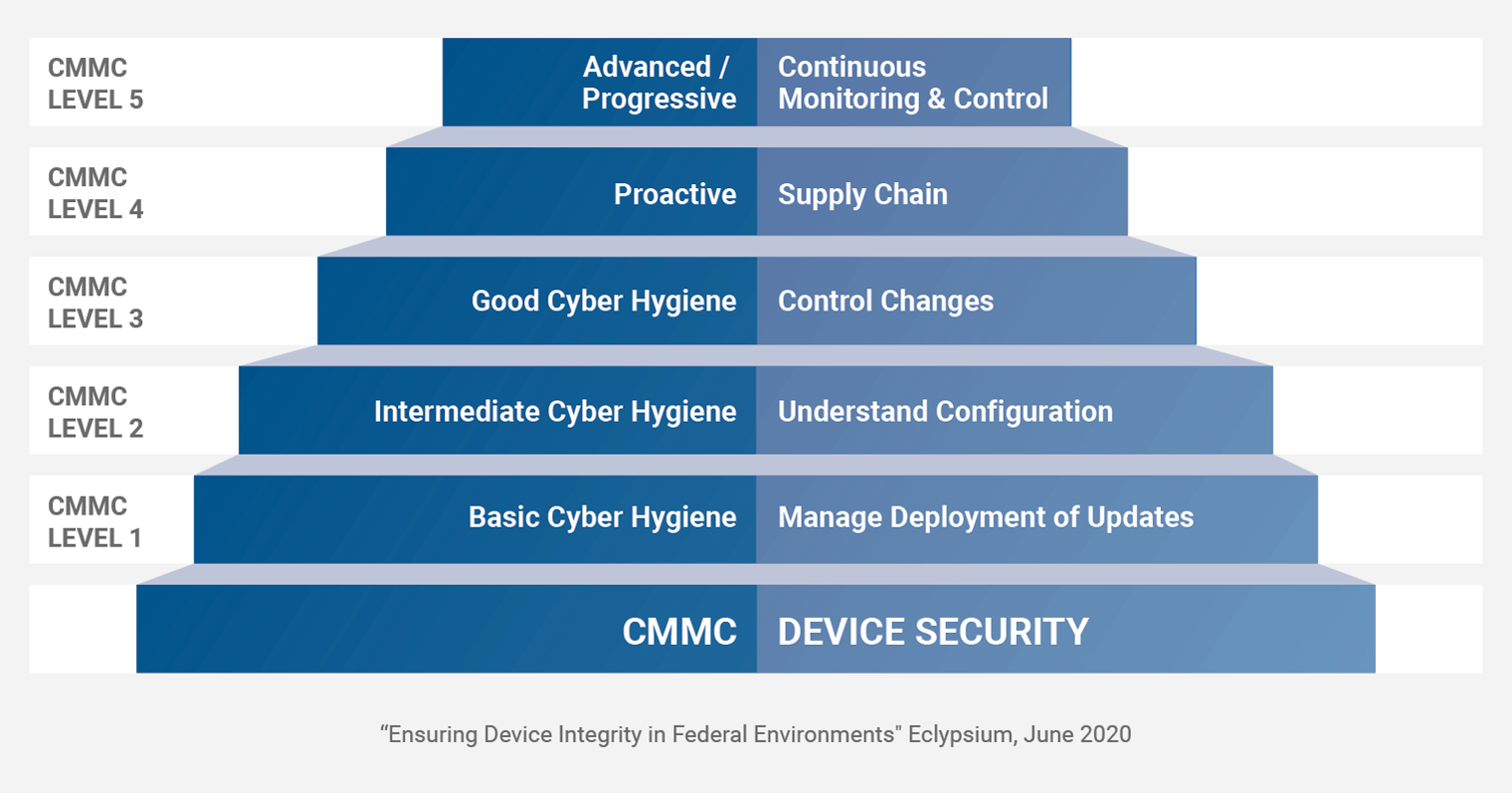
Now, a new whitepaper from Eclypsium models device security on the CMMC levels to help organizations progress from basic cyber hygiene to protecting from advanc...
This content is provided by Eclypsium.
Establishing security at the device level is an integral part of any cybersecurity strategy. FISMA and the NIST documents supporting it repeatedly underscore the importance of firmware and hardware security as part of a modern security program, as does the Defense Department’s Cybersecurity Maturity Model Certification (CMMC). Yet this area remains one of the most overlooked and poorly understood areas of risk within government agencies and federal contractors.
Now, a new whitepaper from Eclypsium models device security on the CMMC levels to help organizations progress from basic cyber hygiene to protecting from advanced persistent threats.
“Nation state adversaries were attacking firmware and hardware years ago, but today anyone can find implant code that works almost everywhere,” said John Loucaides, vice president of research and development at Eclypsium. “In today’s environment, organizations need to support flexible remote and distributed operations while protecting against attacks that go further than before. This is a completely different risk profile.”
Unfortunately, traditional vulnerability scanning and antivirus tools are often blind to weaknesses and threats that reside at the underlying hardware and firmware level of a device. Attacks at this fundamental level violate assumptions and give attackers full control over the device. Such attacks are becoming increasingly common in the wild, driven by advanced actors and by more widespread, opportunistic attack campaigns.
“What’s interesting is that the attacker profile has changed. It morphed from a nation state level attack to something where anybody can go on GitHub today and download the firmware-based rootkits and attacks that I’m talking about,” Loucaides said. “Twenty years ago or more, you could have done this, but it took you actual work to invest the time to understand, first of all, what’s happening at this layer, and then build those attacks. Now, you don’t have to do that, it’s actually quite a lot simpler. And that has been evidenced by the numbers. In the last three years, you’ve had more than a seven fold increase in recorded firmware vulnerabilities. And you can see some of the attack campaigns pivoting into firmware.”
For example, the Russian hacking group known as STRONTIUM, Fancy Bear or APT28, has attacked everything from email accounts to home routers to critical infrastructure. The group created and deployed “LoJax” malware, a UEFI rootkit discovered in the wild. Meanwhile, a Chinese group known as APT41 exploited vulnerabilities in Cisco, Citrix and Zoho devices to install backdoors all across the world. A recent alert from the DHS CISA and the FBI reported that the most commonly exploited vulnerabilities in 2020 involved the firmware of VPN appliances.
“That’s why it’s not enough to focus on cybersecurity at the operating system and application layers,” said Loucaides. “Security leaders need to look deeper, into the firmware and hardware of laptops, servers and networking devices to ensure their organizations are protected. And the CMMC offers a framework that can help with that challenge.”
The ‘maturity model’ at the heart of the CMMC is one of its most important traits and distinguishes it from many other standards,” said Loucaides. “The approach breaks cybersecurity practices into progressive levels ranging from basic cyber hygiene to more proactive measures designed to address advanced threats. The level of maturity organizations need for certification depends on the type and sensitivity of information being protected and the range of threats they face. And what we’ve done is map this out as it applies to device security.”
“The flow of the CMMC is that you’re going to start with understanding first, and then you’re going to control,” Loucaides said. “The CMMC is taking organizations from wherever they are and bringing them to the next level. And that’s exactly what we need to do in the firmware and hardware space.”
“The good news,” Loucaides added, “is that new cybersecurity tools, like those offered by Eclypsium, make it much easier for organizations to ensure that their hardware and firmware receive the same level of visibility and security as their software and networks.”
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories

What the UK gets about remote work that the US doesn’t