
NIST unveils ‘flexible’ second draft for agency cybersecurity
The National Institute of Standards and Technology released a second draft of Special Publication 800-160, a guidebook for agencies to build cybersecurity processes...
No two agencies are exactly alike, nor are cyber threats all the same — that’s why the National Institute of Standards and Technology’s latest version of system security guidance can be adjusted for fit.
Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems — NIST Special Publication 800-160 — is a guide for helping agencies and organizations assign value to their assets and choose the right set of tools that works best to secure their systems.
“This publication is designed to be extremely flexible in its application to meet the diverse needs of organizations,” the document states. “It is not intended to provide a specific recipe for execution — rather, it is a catalog or handbook for achieving the identified security outcomes of each systems engineering process, leaving it to the experience and expertise of the engineering organization to determine what is correct for their purpose. Organizations choosing to use this guidance for their systems security engineering efforts can select and employ some or all of the thirty ISO/IEC/IEEE 15288 processes and some or all of the security‐related activities and tasks defined for each process.”
The draft’s release comes one year after the Office of Personnel Management discovered a massive data breach.
The way security controls are applied today is through a categorization under the Federal Information Processing Standard, said NIST Fellow Dr. Ron Ross in an interview with Federal News Radio.
Data and the security system are determined to be low, moderate or high impact, and then a set of controls out of NIST’s SP 800-53 are selected and implemented.
“This 800-160 comes at it from a different perspective,” Ross said. “This says what are the stakeholder protection needs that are tied to critical mission space or business models, and that ends up spawning a set of security requirements. Then the question is what security controls can we select to satisfy those requirements.”
A holistic approach
The agency released the draft version in May 2014. It’s based on an IEEE and ISO joint standard.
Ross said the second version took so long because NIST answered all of the public comments, and had to factor in a major update to the standard that took place in 2015.
“So our previous draft only had 14 of the total number of processes,” Ross said. “Now we’ve built out all 30 processes. They’re technical from architecture, design, stakeholder requirements, system requirements, all the way through the non-technical processes, which would include things like risk management, configuration management, human resources. We cover every aspect wherever security touches an aspect of an enterprise, it’s addressed in 800-160, so it’s a holistic view.”
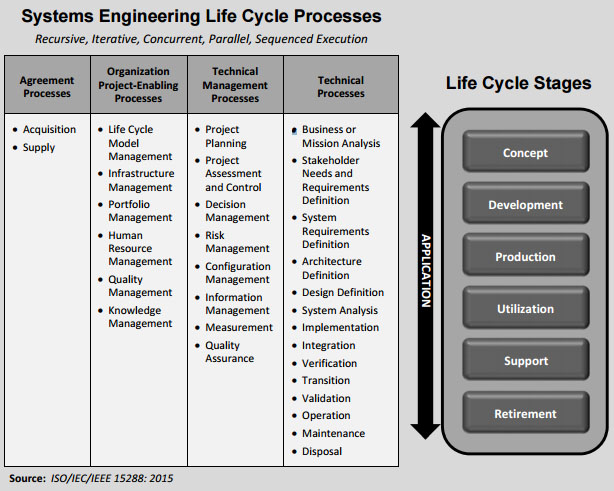
The 30 processes are sorted into four categories: Agreement, organization project-enabling, technical management and technical.
Each process is broken down into purpose, outcome, activities and tasks. For example, the purpose of human resource management sets the criteria for the qualification, assessment and ongoing training for skilled cyber personnel.
The outcome states the goal is to have a skilled cyber workforce that can be assigned to projects. Activities and tasks more specifically suggest actions to take to achieve that outcome.
The 30 processes don’t need to be applied all at once, Ross said, but the hope is to have agencies integrate all of them over time.
“The nice part about 800-160 is that you don’t have to do every process,” Ross said. “You can do whichever ones are comfortable, that you understand, and then you can build out on that. That flexibility is really necessary within federal agencies and the private sector.”
NIST also purposefully chose not to use the word “guidance,” instead choosing to use “considerations” in the title of the publication, Ross said.
“We didn’t want to overwhelm people with saying here’s 300 pages of guidance that you have to implement,” Ross said. “We would like people to start looking at the content, understanding the content.”
The aim of 800-160 is to “normalize” security activities both institutionally and through operations, Ross said.
Institutionalizing means integrating cybersecurity into every aspect of an organization and every decision-making process, Ross said.
“You don’t want to have security be a stovepipe, you want it to be fully integrated across the entire enterprise,” Ross said.
Operationalizing cybersecurity ensures the workforce understands the responsibilities and protections, and what each person is supposed to do.
“Our goal is to get us on the right path and give people information,” Ross said. “It’s all about transparency, so you can make better risk-based decisions at the end of the day.”
NIST is collecting comments on the second draft. Send comments to sec-cert@nist.gov no later than July 1, 2016.
Read all of Federal News Radio’s coverage of the OPM Cyber Breach.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories




