
DHS, FBI report details Russian election hack and defenses against future attacks
The Homeland Security Department and FBI published a Joint Analysis Report detailing the Russian cyber attacks of 2015-16, as well as best practices and mitigat...
While President Barack Obama chose to sanction the Russian individuals and organizations linked to the U.S. election cyber attacks, the Homeland Security Department and FBI are soliciting the help of the private sector in the wake of the network hacks.
DHS and the FBI on Thursday issued a Joint Analysis Report detailing “malicious cyber activity by [Russian civilian and military intelligence Services] RIS,” which the federal government is calling GRIZZLY STEPPE.
Senior administration officials shared during a call with reporters that the key objective of the report is “to better help network defenders in the United States and abroad to identify, detect and disrupt Russia’s global campaign of malicious cyber activities.”
One official who spoke about the report said DHS and the FBI would issue updates to the report as they became available, and encouraged organizations to provide feedback “to help fill in the bigger picture.”
“What we’re asking companies to do is to take this technical information and go back through their logs and see if they see indications of this malicious activity in the past,” the official said. “Even if the bad actors are no longer active in your system, it’s important for the government to know about and understand it. It helps to fill in the bigger picture, provide greater insight into the scope and scale of Russian activity and helps all the network defenders.”
The report has a list of Indicators of Compromise for network owners to review to see whether their systems were jeopardized.
“Some traffic that may appear legitimate is actually malicious, such as vulnerability scanning or browsing of legitimate public facing services (e.g., HTTP, HTTPS, FTP),” the report said. “Connections from these IPs may be performing vulnerability scans attempting to identify websites that are vulnerable to cross-site scripting (XSS) or Structured Query Language (SQL) injection attacks. If scanning identified vulnerable sites, attempts to exploit the vulnerabilities may be experienced.”
The official said DHS also added these indicators to its automatic information sharing network.
As of September, about 50 agencies, private companies and organizations were part of the Homeland Security Department’s automatic information sharing (AIS) network. About 40 private sector companies are mostly receiving cyber threat indicators from the DHS AIS. One company is both receiving and sharing information with the department.
Spearphishing
The JAR builds on an earlier statement in October that attributes the cyber attack to the Russian government.
“Previous JARs have not attributed malicious cyber activity to specific countries or threat actors,” the report stated. “However, public attribution of these activities to RIS is supported by technical indicators from the U.S. Intelligence Community, DHS, FBI, the private sector, and other entities.”
The report outlines ways in which RIS was able to target American citizens and businesses, as well as the Democratic National Committee (DNC).
“These cyber operations have included spearphishing campaigns targeting government organizations, critical infrastructure entities, think tanks, universities, political organizations, and corporations leading to the theft of information,” the report stated. “In foreign countries, RIS actors conducted damaging and/or disruptive cyber-attacks, including attacks on critical infrastructure networks. In some cases, RIS actors masqueraded as third parties, hiding behind false online personas designed to cause the victim to misattribute the source of the attack.”
According to the report, the government identified two groups who hacked the DNC. The groups are labeled in the report as Advanced Persistent Threat (APT) 29 and APT28.
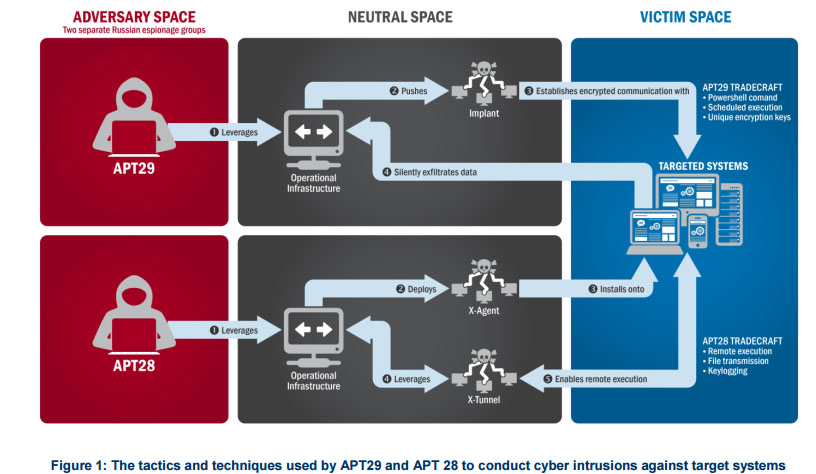
APT29 hacked the DNC in summer 2015, while APT28 did the same in spring 2016.
“APT29 has been observed crafting targeted spearphishing campaigns leveraging web links to a malicious dropper; once executed, the code delivers Remote Access Tools (RATs) and evades detection using a range of techniques,” the report said. “APT28 is known for leveraging domains that closely mimic those of targeted organizations and tricking potential victims into entering legitimate credentials. APT28 actors relied heavily on shortened URLs in their spearphishing email campaigns.”
The two groups gained access to information that was then used to create targeted spearphishing campaigns, along with host domains and malware, the report said.
In 2015, APT29 sent a link to more than 1,000 people in a spearphishing effort, using legitimate domains that tricked some victims into hosting malware and tainted emails.
“In the course of that campaign, APT29 successfully compromised a U.S. political party,” the report stated. “At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware. APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.”
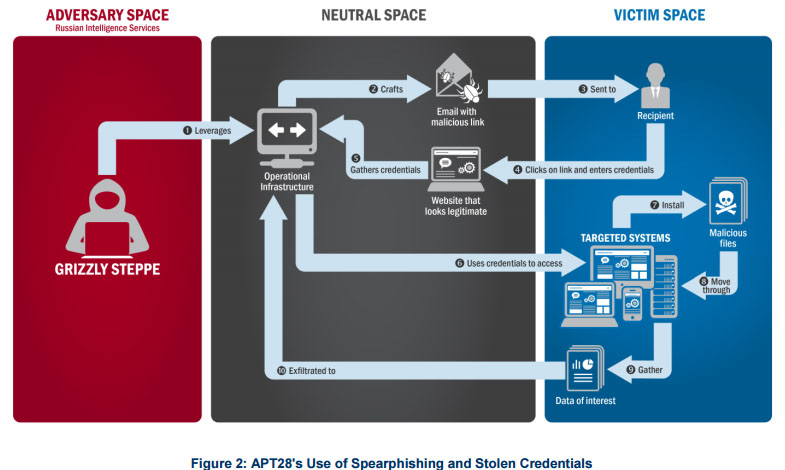
APT28 the following spring used spearphishing to trick victims into changing their passwords via a fake webmail domain, the report stated.
“Using the harvested credentials, APT28 was able to gain access and steal content, likely leading to the exfiltration of information from multiple senior party members,” the report said.
The Joint Analysis Report includes actions to take and recommendations to adopt to protect networks.
Back up all of your critical information, ensure there’s an incident response plan in place and train your staff on cybersecurity best practices, the report said.
DHS specifically stated in the report that up to 85 percent of targeted cyber attacks can be prevented by following a list of seven mitigation strategies.
That list includes whitelisting only the specific programs you want to run on your systems, understanding firewalls and ensuring up to date operating systems and patches.
The report also goes into more detailed strategies to fight off cyber attacks, including:
- Ensuring error messages are generic and do not expose too much information.
- Scrubbing and verifying all administrator accounts regularly.
- Auditing existing firewall rules and close all ports that are not explicitly needed for business.
- Properly securing password files by making hashed passwords more difficult to acquire.
- Securing logs, potentially in a centralized location, and protect them from modification.
Sweeping sanctions
The report is part of a broad range of retaliatory actions authorized Thursday by President Obama.
Obama also sanctioned nine groups and individuals related to the hacking, and gave 35 Russian government officials stationed at the Russian Embassy in Washington, D.C., three days to leave the country.
The President also amended the executive order “Blocking the Property of Certain Persons Engaging in Significant Malicious Cyber-Enabled Activities” to include the authorization of sanctions against those who “tamper with, alter, or cause a misappropriation of information with the purpose or effect of interfering with or undermining election processes or institutions.”
Russia has also been denied access to two Russian government-owned properties, one in Maryland and one in New York.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.





