Feds could save $20 billion using cloud computing
Approximately $20 billion of the $80 billion the government spends on information technology is a potential target for migration to the cloud, according to the ...
Approximately $20 billion of the $80 billion the government spends on information technology is a potential target for migration to the cloud, according to the new Federal Cloud Computing Strategy. The document was released by federal Chief Information Officer Vivek Kundra February 8.
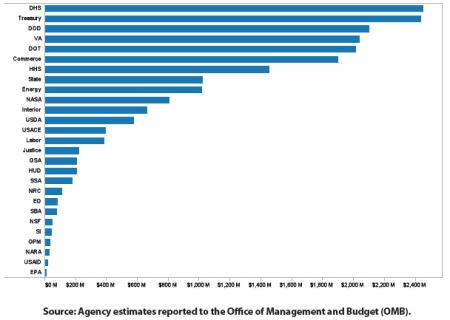
According to estimates, the departments of Homeland Security and Treasury have the most potential to save. Both agencies reported to the Office of Management and Budget they believe they could save over $2.4 billion each by using cloud computing. The Defense Department, Veterans Affairs, and Transportation believe they could save over $2 billion each (See graph below).
The strategy comes on the heels of a cloud-first policy instituted by the Obama administration as part of its 25-Point IT Plan.
“The cloud computing model can significantly help agencies grappling with the need to provide highly reliable, innovative services quickly despite resource constraints,” Kundra said.
According to the document, the Federal Cloud Computing Strategy was developed to:
- Articulate the benefits, considerations, and trade-offs of cloud computing;
- Provide a decision framework and case examples to support agencies in migrating towards cloud computing;
- Highlight cloud computing implementation resources; and,
- Identify federal government activities and roles and responsibilities for catalyzing cloud adoption.
The three-step framework laid out in the strategy gives agencies issues to think about when making the move to the cloud. It also offers an official definition of cloud computing as determined by the National Institute of Standards and Technology.
“Successful organizations carefully consider their broad IT portfolios and create roadmaps for cloud deployment and migration,” said Kundra.”These roadmaps prioritize services that have high expected value and high readiness to maximize benefits received and minimize delivery risk.”
The strategy also outlines the importance of security when determining whether something should be moved to the cloud. It points out six specific security considerations:
- Statutory compliance to laws, regulations, and agency requirements;
- Data characteristics to assess which fundamental protections an application’s data set requires;
- Privacy and confidentiality to protect against accidental and nefarious access to information;
- Integrity to ensure data is authorized, complete, and accurate;
- Data controls and access policies to determine where data can be stored and who can access physical locations; and,
- Governance to ensure that cloud computing service providers are sufficiently transparent, have adequate security and management controls, and provide the information necessary for the agency to appropriately and independently assess and monitor the efficacy of those controls.
The strategy also outlines security benefits of using the cloud including the ability to refocus resources on areas of higher concern, potential platform strength due to greater uniformity, improved resource availability and backup and recovery capabilities, and the ability to leverage alternate cloud services to improve the overall security of the agency.
Kundra said he expects all agencies to re-evaluate their technology sourcing strategies and determine where cloud computing may be possible as part of their budget process.
“Cloud computing can be implemented using a variety of deployment models – private, community, public, or a hybrid combination,” Kundra said.
As the number of cloud computing providers increases, Kundra said the General Services Administration will offer tools which agencies can use to compare the offerings from various companies.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.