Disruption agenda: Adapting to the evolving threat of supply chain warfare
Recognizing supply chain attacks as a form of hybrid warfare, rethinking trust and taking ownership of the risk environment, and learning to effectively communicate...
Over the past decade, cyber-enabled supply chain attacks have emerged as a key feature of hybrid warfare. The rapid weaponization of the supply chain has changed the nature of those attacks, morphing the intended outcome from intelligence and intellectual property collection to destabilization. As access to cyber capabilities continues to flatten the adversarial landscape, the risk of cyber-enabled supply chain attacks will increase. They will destabilize nation-states through the erosion of trust and general chaos, hunting a combination of digital and physical targets. Moreover, attacks serve to distract while other activity is pursued. To stand against it, the government, critical infrastructure community, and private sector must rethink how partnerships are managed. Trust must be continuously proven and never absolute, and efforts to improve supply chain risk management practices must be expanded.
An ideal tool of hybrid warfare
Starting with Stuxnet in 2010, and manifesting most recently in the SolarWinds incident late last year, the explosion of cyber-enabled supply chain attacks is evidence that an era of hybrid warfare is upon us. Hybrid warfare is similar to asymmetric warfare in that it is non-conventional warfare that is often contactless and plays out in the gray space between conflict and peace. It employs gray-zone tactics — like incremental aggression, information warfare and covert operations — that are unlikely to trigger conventional responses. But unlike asymmetric warfare in which relatively weaker adversaries look to creatively exploit a stronger opponent’s weakness, hybrid warfare may be tactically, operationally and strategically dispatched by near peers, second-tier nation-states and non-state actors alike. As gray zone tactics increase in the next decade, cyber-enabled supply chain attacks will be chief among them.
It is also noteworthy that early cyber-enabled supply chain attacks were confined to the digital realm. But, as seen in the Stuxnet proto-attack, threat actors have increasingly sought to incur damage that is logical, physical and psychosocial in nature. This mixed-medium approach allows adversaries to tiptoe even closer to the line between tension and conflict.
Disruption as an intended outcome
Although early cyber-enabled supply chain attacks focused on access to government systems, information and intellectual property, adversaries noted the byproducts of these attacks were equally damaging. Resulting chaos and erosion of trust from attacks like NotPetya and SolarWinds had a desirable destabilizing effect. They also provided the ideal distraction from other more significant, clandestine or strategically important adversarial actions. As a result, disruption is mounting as the intended outcome of supply chain attacks rather than a mere byproduct.
As more cyber-enabled supply chain attacks are used as instruments of disruption, larger and more devastating attacks can be expected. Government can be overwhelmed responding to large scale exploitations, giving adversaries additional cover and time to react.
Rethinking trust
As victims — known, unknown and potential — scramble to guard against increasing cyber-enabled supply chain threats, trust that was once inherent is subtly eroding. Proprietary source code is increasingly viewed with suspicion, impacting development timelines and hampering innovation. There is no longer pure faith in software updates, potentially degrading basic cyber hygiene. On the acquisition front, new vendors and partners will (justifiably) be looked at with a higher degree of scrutiny, creating barriers to entry that didn’t previously exist and reducing the pool of talent and services available to the government. Hard-fought collaboration and information-sharing cultivated since 9/11 is now seen as a potential exposure, because increased connectedness means increased vulnerability. The erosion of trust and all of its consequences play into adversaries’ agenda of destabilization.
Under the Executive Order on Improving the Nation’s Cybersecurity, federal agencies are being directed to solve part of this problem with zero-trust architecture. While zero-trust architecture may be a panacea, it is a distant reality. In the interim, trust in partners providing critical data and capabilities must be balanced with cybersecurity. It requires allocating resources to shift from a position of inherent trust, in which partners are implicitly relied upon to secure environments, to validated trust, developed through demonstrated and transparent security practices. This will provide traceability and accountability essential to efficient supply chain risk management. Emerging requirements, such as the Cybersecurity Maturity Model Certification, are a step in the right direction, but they cannot be paper exercises. Those entities leveraging third-parties must take ownership of risk entering their environments, not transfer it. Only then can they have the requisite command and control of products, data and services received to effectively defend against threat actors combing for any vector to disrupt.
Exchanging information
The supply chain threat will not be thwarted by any single agency or entity acting alone. To date, U.S. legal requirements to create common collaborative environments for sharing threat assessments and other vital supply chain information have gone largely unmet. There are a range of contributing factors, to include the legal liability associated with threat assessments that have been made public. But the lack of information sharing limits visibility of systematic threats and results in senseless duplication of supply chain integrity efforts. Both the Executive Order on America’s Supply Chains and the Executive Order on Improving the Nation’s Cybersecurity highlight the importance of improving information sharing — not just across the government, but also with private sector partners, understanding public-private partnerships will remain a constant in supply chain delivery. Sharing timely, actionable information about threats with government and supply chain partners will advance the ability to provide a collaborative defense against emerging and blended threats. A whole of government response will be key to making meaningful information exchange happen, internally as well as with industry and international partners.
The future of supply chain warfare
Destabilization and democratization are trends that will continue. Moreover, disruptive supply chain attacks will be directed at new targets, like 5G and space technologies. Recognizing supply chain attacks as a form of hybrid warfare, rethinking trust and taking ownership of the risk environment, and learning to effectively communicate critical information to supply chain partners are crucial steps in defending against this looming threat. These actions, if taken with a sense of urgency in concert with an overarching whole-of-government approach, will enable a sorely needed collective and collaborative defense.
Daniel Lewis is a director at Guidehouse.
Megan Moloney is a managing consultant for National Security at Guidehouse.
Disruption agenda: Adapting to the evolving threat of supply chain warfare
Recognizing supply chain attacks as a form of hybrid warfare, rethinking trust and taking ownership of the risk environment, and learning to effectively communicate...
Over the past decade, cyber-enabled supply chain attacks have emerged as a key feature of hybrid warfare. The rapid weaponization of the supply chain has changed the nature of those attacks, morphing the intended outcome from intelligence and intellectual property collection to destabilization. As access to cyber capabilities continues to flatten the adversarial landscape, the risk of cyber-enabled supply chain attacks will increase. They will destabilize nation-states through the erosion of trust and general chaos, hunting a combination of digital and physical targets. Moreover, attacks serve to distract while other activity is pursued. To stand against it, the government, critical infrastructure community, and private sector must rethink how partnerships are managed. Trust must be continuously proven and never absolute, and efforts to improve supply chain risk management practices must be expanded.
An ideal tool of hybrid warfare
Starting with Stuxnet in 2010, and manifesting most recently in the SolarWinds incident late last year, the explosion of cyber-enabled supply chain attacks is evidence that an era of hybrid warfare is upon us. Hybrid warfare is similar to asymmetric warfare in that it is non-conventional warfare that is often contactless and plays out in the gray space between conflict and peace. It employs gray-zone tactics — like incremental aggression, information warfare and covert operations — that are unlikely to trigger conventional responses. But unlike asymmetric warfare in which relatively weaker adversaries look to creatively exploit a stronger opponent’s weakness, hybrid warfare may be tactically, operationally and strategically dispatched by near peers, second-tier nation-states and non-state actors alike. As gray zone tactics increase in the next decade, cyber-enabled supply chain attacks will be chief among them.
It is also noteworthy that early cyber-enabled supply chain attacks were confined to the digital realm. But, as seen in the Stuxnet proto-attack, threat actors have increasingly sought to incur damage that is logical, physical and psychosocial in nature. This mixed-medium approach allows adversaries to tiptoe even closer to the line between tension and conflict.
Disruption as an intended outcome
Although early cyber-enabled supply chain attacks focused on access to government systems, information and intellectual property, adversaries noted the byproducts of these attacks were equally damaging. Resulting chaos and erosion of trust from attacks like NotPetya and SolarWinds had a desirable destabilizing effect. They also provided the ideal distraction from other more significant, clandestine or strategically important adversarial actions. As a result, disruption is mounting as the intended outcome of supply chain attacks rather than a mere byproduct.
Join us Jan. 27 for our Industry Exchange Cyber 2025 event where industry leaders will share the latest cybersecurity strategies and technologies.
As more cyber-enabled supply chain attacks are used as instruments of disruption, larger and more devastating attacks can be expected. Government can be overwhelmed responding to large scale exploitations, giving adversaries additional cover and time to react.
Rethinking trust
As victims — known, unknown and potential — scramble to guard against increasing cyber-enabled supply chain threats, trust that was once inherent is subtly eroding. Proprietary source code is increasingly viewed with suspicion, impacting development timelines and hampering innovation. There is no longer pure faith in software updates, potentially degrading basic cyber hygiene. On the acquisition front, new vendors and partners will (justifiably) be looked at with a higher degree of scrutiny, creating barriers to entry that didn’t previously exist and reducing the pool of talent and services available to the government. Hard-fought collaboration and information-sharing cultivated since 9/11 is now seen as a potential exposure, because increased connectedness means increased vulnerability. The erosion of trust and all of its consequences play into adversaries’ agenda of destabilization.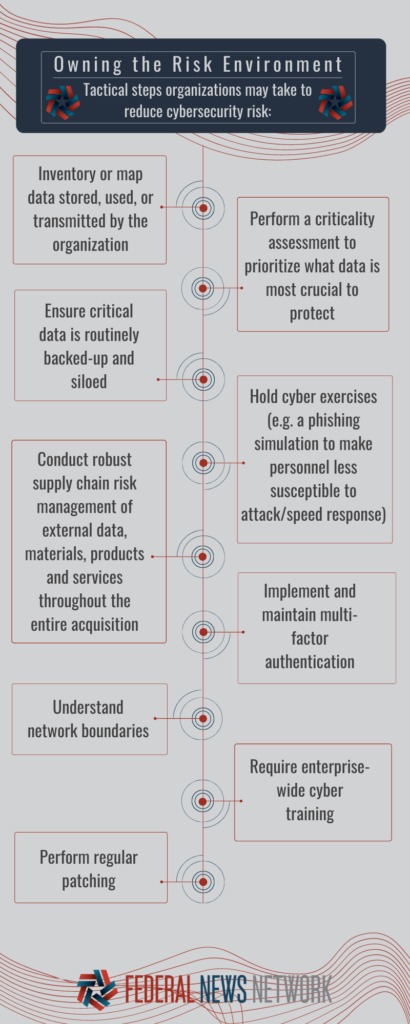
Under the Executive Order on Improving the Nation’s Cybersecurity, federal agencies are being directed to solve part of this problem with zero-trust architecture. While zero-trust architecture may be a panacea, it is a distant reality. In the interim, trust in partners providing critical data and capabilities must be balanced with cybersecurity. It requires allocating resources to shift from a position of inherent trust, in which partners are implicitly relied upon to secure environments, to validated trust, developed through demonstrated and transparent security practices. This will provide traceability and accountability essential to efficient supply chain risk management. Emerging requirements, such as the Cybersecurity Maturity Model Certification, are a step in the right direction, but they cannot be paper exercises. Those entities leveraging third-parties must take ownership of risk entering their environments, not transfer it. Only then can they have the requisite command and control of products, data and services received to effectively defend against threat actors combing for any vector to disrupt.
Exchanging information
The supply chain threat will not be thwarted by any single agency or entity acting alone. To date, U.S. legal requirements to create common collaborative environments for sharing threat assessments and other vital supply chain information have gone largely unmet. There are a range of contributing factors, to include the legal liability associated with threat assessments that have been made public. But the lack of information sharing limits visibility of systematic threats and results in senseless duplication of supply chain integrity efforts. Both the Executive Order on America’s Supply Chains and the Executive Order on Improving the Nation’s Cybersecurity highlight the importance of improving information sharing — not just across the government, but also with private sector partners, understanding public-private partnerships will remain a constant in supply chain delivery. Sharing timely, actionable information about threats with government and supply chain partners will advance the ability to provide a collaborative defense against emerging and blended threats. A whole of government response will be key to making meaningful information exchange happen, internally as well as with industry and international partners.
The future of supply chain warfare
Destabilization and democratization are trends that will continue. Moreover, disruptive supply chain attacks will be directed at new targets, like 5G and space technologies. Recognizing supply chain attacks as a form of hybrid warfare, rethinking trust and taking ownership of the risk environment, and learning to effectively communicate critical information to supply chain partners are crucial steps in defending against this looming threat. These actions, if taken with a sense of urgency in concert with an overarching whole-of-government approach, will enable a sorely needed collective and collaborative defense.
Daniel Lewis is a director at Guidehouse.
Megan Moloney is a managing consultant for National Security at Guidehouse.
Read more: Commentary
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories
The government procurement efficiency list
How to expedite your CMMC process
Best practices for developing soft skills in the federal workforce in 2025