The Cybersecurity Maturity Model Certification rule is now final, yet we still see organizations seeking certification waiting to implement the requirements.
The Cybersecurity Maturity Model Certification (CMMC) rule is now final, yet we still see organizations seeking certification (OSCs) waiting to implement the requirements.
On average, it takes OSCs 12 to 24 months to fully implement CMMC requirements. So where should organizations begin in their preparation? The following steps and recommendations will serve as actional best practices to help organizations “catch up,” and expedite their CMMC process most efficiently. There are numerous ways to develop a CMMC program, but it should start with organizational buy-in. Everyone within the organization, from the CEO down, should understand the why behind CMMC and what it will take to make it happen. Why is this the most critical step? Because everyone will play some role in the program development process:
The CEO plays an essential part. If CMMC is not important to the CEO, it will not be important to the staff.
The chief financial officer manages the budget and provides the necessary funds to establish the program.
Personnel that process, store or transmit controlled unclassified information (CUI) must articulate to the information technology team where the data resides, how they receive it, and how they send it out.
Key stakeholders from across the company will be vital in developing the documentation. Examples include human resources for onboarding processes, marketing managers for how federal contract information (FCI) is posted or redacted, and contract managers and their processes for bringing on board a new contract.
After organizational buy-in has been secured, determine where the data resides within your environment, who has access to it and where it is stored. Once the data is identified, determine if it can be isolated and if its location can be determined. For example, moving said data to a subset of designated servers within a protected data center or in a cloud enclave. By isolating the CUI data to a small footprint, the organization will have an easier time managing it. Next, determine your CMMC environment’s boundary. What is in the boundary, and what is not? Figuring out the boundary will help scope the project when it comes time for certification. Once this plan is developed, the next step is determining how the CUI data flows in and out of the environment. Examples include email, safe file sharing, etc. The last step is to capture all of this in network diagrams and documentation.
Creating the appropriate documents is arguably the most time-consuming work that must be performed. Organizations typically choose an individual, put them in a corner, and tell them to knock it out by themselves — which is probably not the best idea. Instead, establish working groups with key stakeholders participating. The more they participate in drafting the documents, the more ownership they will take, and the more successful they will be in assessment interviews. The graph depicted below should provide an idea of how much time is spent creating these documents.
Now that the heavy lifting is done, OSCs should verify that the configurations for various devices within the environment match what is captured in the documentation. An example could be firewall configurations showing “deny all” inbound rules and “permit by exception” outbound rules. Other examples include screen timeout settings, automatic session termination period, log retention period, and unsuccessful login attempts, just to name a few. Check each device configuration to ensure everything matches. Now we are ready to conduct our self-assessment, which some can view as a practice assessment. Be as honest as possible and invite the key stakeholders to participate. The more experience they have participating in an assessment, the more comfortable they will be during the certification. Once complete, record the supplier performance risk system (SPRS) results in the procurement integrated enterprise environment (PIEE) portal. Finally, select your certified third party assessment organization (C3PAO). Remember, if performing the steps outlined above is too arduous for the organization, seek assistance from a registered practitioner organization (RPO) or a C3PAO. Authorized assessing and consulting organizations can be found in the marketplace on the Cyber AB’s website. Waiting lists for certification are already growing, so don’t delay.
To date, numerous OSCs have already taken advantage of the early adopter program, known as the Joint Surveillance Voluntary Assessment Program. For those organizations that have completed an assessment and achieved a 110 SPRS score, their assessment will be converted to a CMMC certificate.
So what can OSCs do now to ensure they are not losing future business with the Defense Department? Stop waiting and start doing.
For those already complete, the work is not done. Your certification is good for three years, but there is still a requirement to self-attest annually. Thus, maintaining compliance with the requirements is vital. Additionally, DoD is aligning the CMMC rule with NIST SP 800-171 revision 2, and we already know that NIST SP 800-171 revision 3 is around the next corner. At some point, the newer revision will be adopted into CMMC. We already know that waiting is not beneficial, so start reviewing revision 3 now and develop your strategy for how to implement the new requirements.
Robert Teague is director of CMMC services at Redspin.
How to expedite your CMMC process
The Cybersecurity Maturity Model Certification rule is now final, yet we still see organizations seeking certification waiting to implement the requirements.
The Cybersecurity Maturity Model Certification (CMMC) rule is now final, yet we still see organizations seeking certification (OSCs) waiting to implement the requirements.
On average, it takes OSCs 12 to 24 months to fully implement CMMC requirements. So where should organizations begin in their preparation? The following steps and recommendations will serve as actional best practices to help organizations “catch up,” and expedite their CMMC process most efficiently. There are numerous ways to develop a CMMC program, but it should start with organizational buy-in. Everyone within the organization, from the CEO down, should understand the why behind CMMC and what it will take to make it happen. Why is this the most critical step? Because everyone will play some role in the program development process:
After organizational buy-in has been secured, determine where the data resides within your environment, who has access to it and where it is stored. Once the data is identified, determine if it can be isolated and if its location can be determined. For example, moving said data to a subset of designated servers within a protected data center or in a cloud enclave. By isolating the CUI data to a small footprint, the organization will have an easier time managing it. Next, determine your CMMC environment’s boundary. What is in the boundary, and what is not? Figuring out the boundary will help scope the project when it comes time for certification. Once this plan is developed, the next step is determining how the CUI data flows in and out of the environment. Examples include email, safe file sharing, etc. The last step is to capture all of this in network diagrams and documentation.
Creating the appropriate documents is arguably the most time-consuming work that must be performed. Organizations typically choose an individual, put them in a corner, and tell them to knock it out by themselves — which is probably not the best idea. Instead, establish working groups with key stakeholders participating. The more they participate in drafting the documents, the more ownership they will take, and the more successful they will be in assessment interviews. The graph depicted below should provide an idea of how much time is spent creating these documents.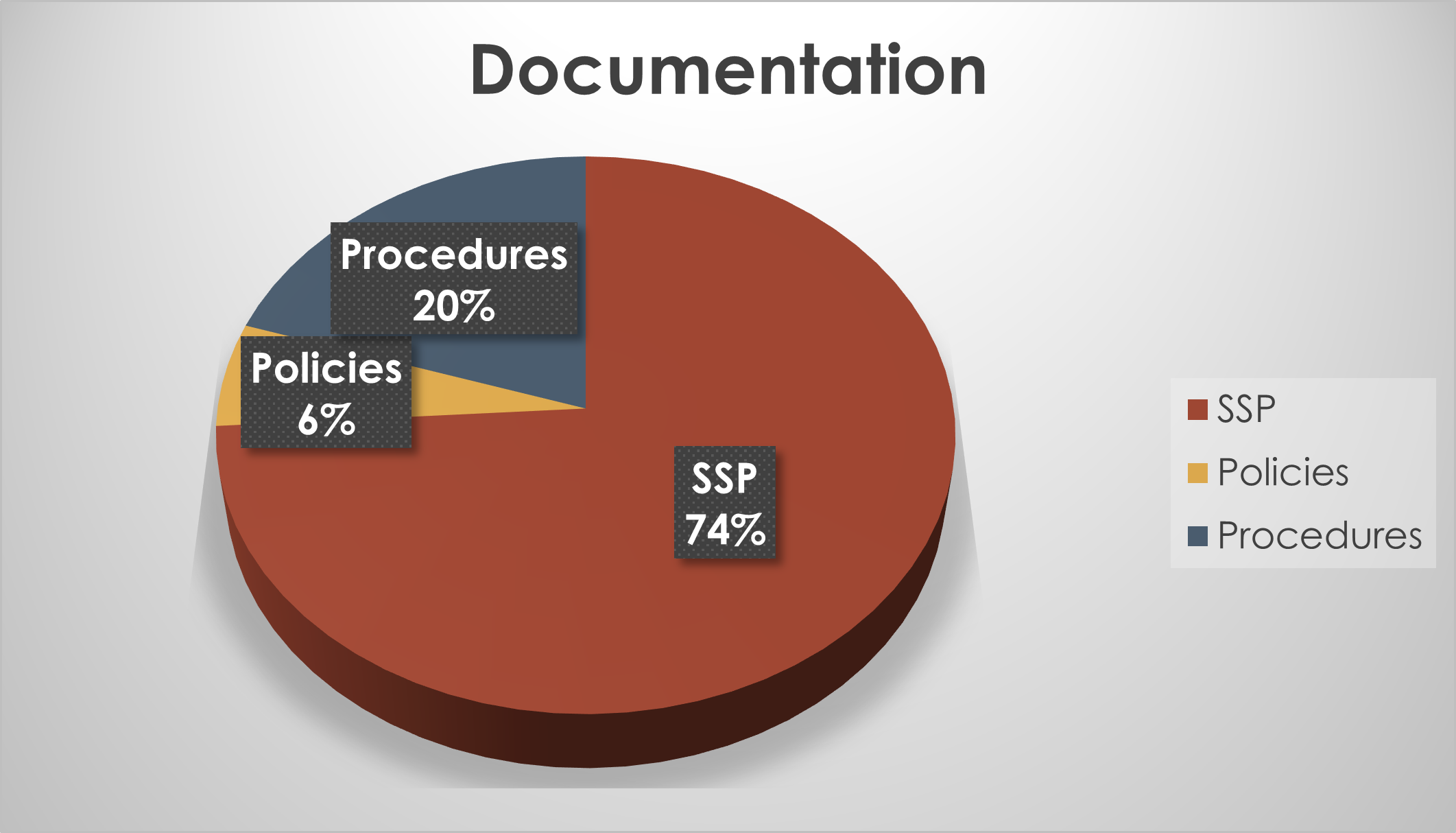
Join us Jan. 27 for our Industry Exchange Cyber 2025 event where industry leaders will share the latest cybersecurity strategies and technologies.
Now that the heavy lifting is done, OSCs should verify that the configurations for various devices within the environment match what is captured in the documentation. An example could be firewall configurations showing “deny all” inbound rules and “permit by exception” outbound rules. Other examples include screen timeout settings, automatic session termination period, log retention period, and unsuccessful login attempts, just to name a few. Check each device configuration to ensure everything matches. Now we are ready to conduct our self-assessment, which some can view as a practice assessment. Be as honest as possible and invite the key stakeholders to participate. The more experience they have participating in an assessment, the more comfortable they will be during the certification. Once complete, record the supplier performance risk system (SPRS) results in the procurement integrated enterprise environment (PIEE) portal. Finally, select your certified third party assessment organization (C3PAO). Remember, if performing the steps outlined above is too arduous for the organization, seek assistance from a registered practitioner organization (RPO) or a C3PAO. Authorized assessing and consulting organizations can be found in the marketplace on the Cyber AB’s website. Waiting lists for certification are already growing, so don’t delay.
To date, numerous OSCs have already taken advantage of the early adopter program, known as the Joint Surveillance Voluntary Assessment Program. For those organizations that have completed an assessment and achieved a 110 SPRS score, their assessment will be converted to a CMMC certificate.
So what can OSCs do now to ensure they are not losing future business with the Defense Department? Stop waiting and start doing.
For those already complete, the work is not done. Your certification is good for three years, but there is still a requirement to self-attest annually. Thus, maintaining compliance with the requirements is vital. Additionally, DoD is aligning the CMMC rule with NIST SP 800-171 revision 2, and we already know that NIST SP 800-171 revision 3 is around the next corner. At some point, the newer revision will be adopted into CMMC. We already know that waiting is not beneficial, so start reviewing revision 3 now and develop your strategy for how to implement the new requirements.
Robert Teague is director of CMMC services at Redspin.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories
Best practices for developing soft skills in the federal workforce in 2025
Using your FEVS results to create an engaged workplace
The top five procurement themes for 2025