Recent travel guidance for using government devices gives best practices in unsecure countries
Public comments on the Federal Mobility Group's draft International Travel Guidance for Government Mobile Devices are open now through Dec. 28.
New guidance for anyone traveling overseas with a government device is out from the interagency Federal Mobility Group. And its members want feedback before the end of the year.
International Travel Guidance for Government Mobile Devices aims to give individuals and agencies actionable steps to strengthen cybersecurity on their government-issued mobile device and when accessing federal networks while abroad, especially in areas that have far different laws around access and security than what people are used to in the U.S. Public comments on the guidance are open now through Dec. 28.
“Although the various COVID-19 variants are fluctuating, we anticipate that international travel for federal business will pick up,” Carnella Stephens, a cybersecurity analyst for the State Department, said Wednesday during an ACT-IAC panel with other members of the Group. “People traveling on official government business expect to be able to carry their mobile devices with them. There’s a need to recognize that because of their portability and always-on state, mobile devices are susceptible to compromise, theft, physical damage and loss.”
Stephens said the Federal Mobility Group’s guidance was an intergovernmental collaboration effort and it applies to government-furnished equipment, smartphones and tablets. The Group identified best practices for securing mobile devices before, during and upon completion of travel. Stephens said existing agency guidance and best practices were reviewed, including the National Security Agency and the departments of State, Homeland Security, Defense, Education and Energy.
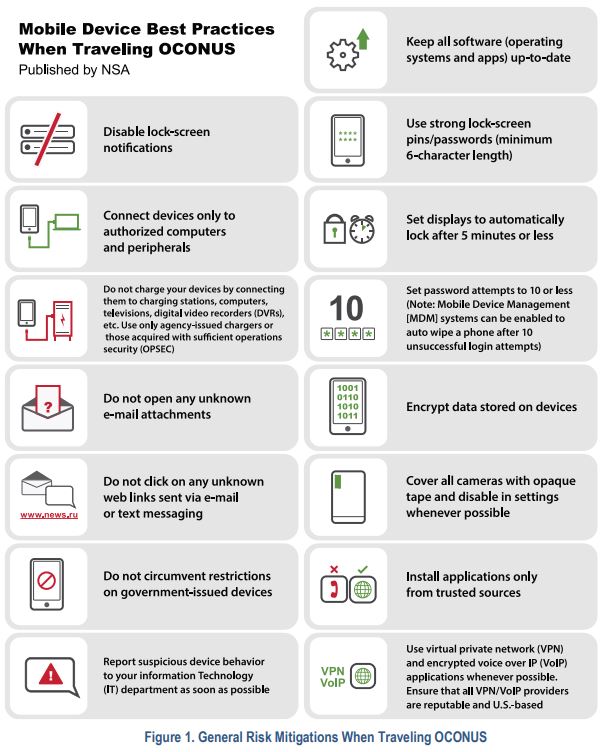
At Energy in particular, Amy Hamilton, senior advisor for National Cybersecurity Policy and Programs, said the mobile government furnished equipment policy was on hold until the recent uptick in international travel. At home in the U.S., she said people take the security of their devices for granted because of laws in place about what is or is not permitted, but that’s not always the case abroad.
“When you’re going overseas, and you’re traveling, you might not realize that this is a state run network that you perhaps don’t want your device to be connecting to, and making sure that users have that sense of awareness before they travel; depending on the locations for travel we have specific direct briefings for people to inform them of things that they can expect,” she said. “And in some countries, you can go into that country and upon entering the country, they’re asking you to pull up your mobile device and to see certain aspects of it.”
She also said users who wish to download local apps in the country they’re visiting still need security features in place to block those. She added that the educational side of device security guidance is still tremendously important, and it amazes her when people still need to be informed about regularly updating their apps or getting the latest patches.
Paranoia is a useful thing when traveling with your government devices, said Alex Lisle, chief technology officer of mobile security company Kryptowire. Always bring your own chargers and do not borrow someone else’s cables to plus in your phone or tablet when traveling.
“But also, where you’re plugging into, and just assuming that you’re getting power from a power brick might not necessarily be true. And you might think that that might be extreme, but the truth is, a lot of attacks are opportunistic,” he said.
Lisle said people tend to implicitly trust mobile carriers and leave their phones on all day, and those phones have cameras, microphones and location tracking. It makes them more risky than a laptop that is more likely to be shut down more frequently.
Based in part on work done by the Federal Mobility Group, the Cybersecurity Quality Services Management Office in the Cybersecurity and Infrastructure Security Agency has developed a mobile app vetting service to scan for known vulnerabilities and offer remediation before those apps are installed on a device. QSMO Branch Chief Jim Sheire said they can also use the service to scan installed apps and notify the traveler or the device issuing office of any issues or to flag prior to the traveler’s departure.
QSMO also offers the Travel Verified Information Protection service to scan mobile devices prior to and upon return from travel to untrusted environments. That gives a baseline of the device’s security configuration against which to look for any changes after the user returns.
“And that security posture of the mobile device, it facilitates that assessment by a security analyst to detect potential malicious activity or vulnerabilities, and importantly provides that post travel mitigation,” Sheire said.
While the president’s cybersecurity executive order has led people to place greater emphasis on securing the nation’s traditional enterprise, Hamilton said mobile devices need to be treated as an extension of that enterprise when it comes to controls like endpoint detection and response.
Lisle agreed and pointed to anyone attending a work meeting from their device.
“It’s a personal device. So it records things in those locations, things that you wouldn’t worry about necessarily on a laptop. I wouldn’t necessarily worry about where the GPS location is. On devices carried around by an employee 24 hours a day, that’s a different threat model,” he said. “It’s going to be an interesting time. I think there’s going to be a change in people’s perceptions as time moves on.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Amelia Brust is a digital editor at Federal News Network.
Follow @abrustWFED






