Post-OPM hack efforts to close cyber gaps paid off in 2016
The Office of Management and Budget’s fiscal 2016 Federal Information Security Management Act (FISMA) report to Congress shows more agencies have stronger cyber...
Only now can agencies see the progress the government has made in securing its systems and data in the wake of the Office of Personnel Management’s massive data breach and the cyber sprint that followed.
If nothing else, the fiscal 2016 Federal Information Security Management Act (FISMA) report to Congress shows the focus over the last two years by the Obama administration is paying off.
Grant Schneider, the acting federal chief information security officer, said in a blog post that OMB saw governmentwide improvements around information security continuous monitoring capabilities, the use of multi-factor authentication for network access and the implementation of anti-phishing and malware defense capabilities.
“OMB reviews data from the 23 civilian CFO Act agencies on a quarterly basis as part of the President’s Management Council Cybersecurity Assessment, which reviews agency programs against government-wide cybersecurity performance goals. In the first quarter of fiscal 2016, only five of these agencies had information security programs that met or exceeded government-wide performance goals. By the end of FY 2016, 13 agencies had met these goals and all others were making significant progress toward this end as a direct result of the oversight mechanisms described above,” the report stated.
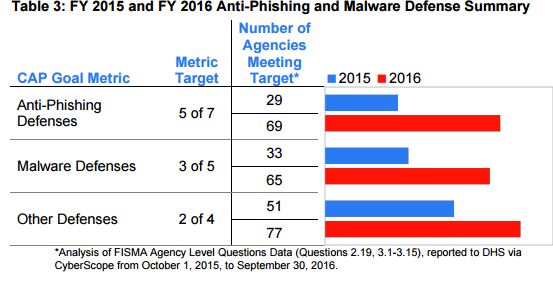
The oversight mechanisms included the CyberStat sessions, which increased to 24 reviews in 2016 from 14 in 2015, and OMB’s meetings with agency CISOs or other cybersecurity officials to review FISMA metrics and address any challenges.
In addition to tools and reviews, OMB said agencies made major improvements in the cybersecurity workforce.
“Agencies are already making considerable progress toward addressing workforce shortages, as they hired over 7,500 cybersecurity and IT employees in 2016; by comparison, federal agencies hired 5,100 cybersecurity and IT employees in 2015,” the report stated.
Part of this increase comes from the push from OMB, which released the first-ever cyber workforce strategy in July. Additionally, Congress added provisions in the Cybersecurity Act of 2015 requiring agencies to assess the skills of their workforces. Initial reports to the House Homeland Security Committee, however, show agencies are struggling to train their cyber workforces.
The need for more and better cyber workers as well as better defenses was never more evident than in 2016.
In the FISMA report, the Homeland Security Department’s U.S. Computer Emergency Readiness Team (US-CERT) says under the new approach to reporting governmentwide incident metrics agencies faced almost 31,000 attacks last year.
“I applaud OMB for taking the bold step of publicizing major incidents for the first time. Congress must do their duty now and dig deep on these incidents,” said Trevor Rudolph, the former chief of OMB’s Cyber and National Security Unit and now chief of business operations and cybersecurity at Whitehawk, a consulting firm. “The new DHS incident notifications guidelines are an improvement on previous guidelines. These guidelines should help in determining the true impact of each incident vs. determining a raw total of all incidents that occur in a year (which is what we used to report). I encourage DHS to ensure they have a method for tracking and analyzing the impacts of federal incidents so we can determine if certain trends require a strategic shift in the way we’re defending Federal networks. We must use this data to respond to threats as one federal government.”
Email or phishing attacks remained the most popular way for hackers to try to get into agency networks with 3,160 incidents.
“In FY 2016, US-CERT’s revised Incident Notification Guidelines required agencies to use an incident reporting methodology that classifies incidents by the method of attack, known as attack vector, and to specify the impact to the agency. This is a shift from the previous reporting methodology, where agencies reported on types of incidents that had no potential impact on operations,” Schneider said. “While the shift to attack vector means that the FY 2016 incident data is not comparable to prior years’ incident data, the new approach allows OMB, DHS and agencies to focus on incidents that may impact operations. Similarly, the report also details 16 of the 30,899 incidents that agency heads determined were major information security incidents, a designation that triggers mandatory steps for agencies including reporting certain information to Congress.”
Employees improperly using IT equipment and the loss or theft of technology devices remain the top incidents across the government, totaling more than 9,800 of those that can be identified.
“This effort helps remove incidents that did not have an impact on an agency such as the non-cyber or scan, probes and attempted access and duplicate incident entries reported by automated systems, such as EINSTEIN, and separately reported by agency employees,” the report stated.
Of those 16 major incidents, the Federal Deposit Insurance Corporation reported 10 of them, including one that impacted 44,000 customers. The FDIC hired Booz Allen Hamilton to perform an end-to-end analysis of its cybersecurity and then made fixes based on what the review found.
Rudolph said he would like Congress and DHS to look further into whether agencies are reporting the right kinds of incidents, has the agency response to these incidents been effective and does the relevant agency have the right leadership (from secretary to CISO) and resources in place to respond to these incidents and prevent future ones?
OMB says the departments of Commerce, Health and Human Services, Housing and Urban Development and Treasury accounted for the other six major breaches.
The FISMA report also for the first time in a long time detailed the cyber spending per civilian agency.
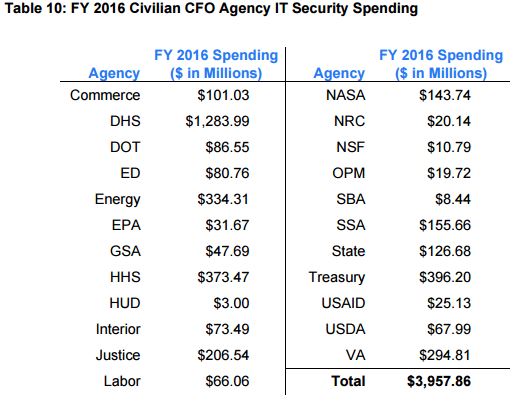
In all civilian agencies spent $3.96 billion on cybersecurity in 2016 with DHS accounting for $1.28 billion. The other top spending agencies included Treasury ($396 million), HHS ($373 million), Energy ($334 million) and Justice ($206 million).
“In fiscal 2016, OMB updated the way it captures information security spending by agencies. Utilizing the existing Capital Planning and Investment Control budget collection process, OMB cyber reoriented its budget categories to relate to existing FISMA metric categories,” the report stated. “The goal is to better map cybersecurity spending to agency performance on specific capabilities, to determine where gaps exist, and where agencies may need additional funding.”
The Defense Department accounted for roughly $8.4 billion in cybersecurity spending in 2016.
The Obama administration requested a 35 percent increase to $19 billion across the government in fiscal 2017 — about $6.6 billion more than agencies received in 2016.
President Donald Trump has said several times that cybersecurity would be a priority for his administration. Trump was expected to sign a new cyber executive order in February, but decided to pull it back for a further review. That new order now is expected to come in the middle of March.
“I encourage the Trump administration to use OMB as a tool to drive improved federalwide performance. We will only see the progress we want if the agency that wields both management and budget sticks (and carrots) is leading the way,” Rudolph said.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED
Related Stories

Cyber experts consider agency leaders’ responsibility ahead of Trump’s cyber EO





