NIST hopes clarification on IoT vs. IT will help cybersecurity for both
The first round of public comments recently closed on NIST's draft IR 8228 “Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks."...
Internet of things devices and traditional IT systems have much in common, but their differences are not always understood by federal agencies. When this spills over into cybersecurity controls, the National Institute of Standards and Technology sees a need for more communication.
In September, NIST released its draft IR 8228 “Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks” outlining the distinction. The first round of public comments on the document recently closed but produced promising results, said co-author Katerina Megas.
She said IoT device deployments are pervasive throughout the federal government, so much so that her office does not have a concrete number on the usage. But she said many agencies do not have a grasp on their IoT inventory. Her primary concern is improving IoT cybersecurity with respect to existing NIST guidance.
“IoT has a very large overlap,” she said on Federal Monthly Insights — Security Month. “What we’re trying to do is we’re trying to hone in — OK, where are the gaps? Where are the deltas, and where do we maybe need something different to address the cybersecurity risks of IoT?”
Megas is the Commercial Adoption lead for the Trusted Identities Group, as well as program manager for the Cybersecurity for IoT program at NIST. She said 8228 addresses cybersecurity and privacy risks together, and that the document had input from private industry.
“Although the primary audience is federal agencies, we did work very closely with private industry because at NIST we like anything we do to be something that is useful beyond just federal agencies,” Megas said on Federal Drive with Tom Temin.
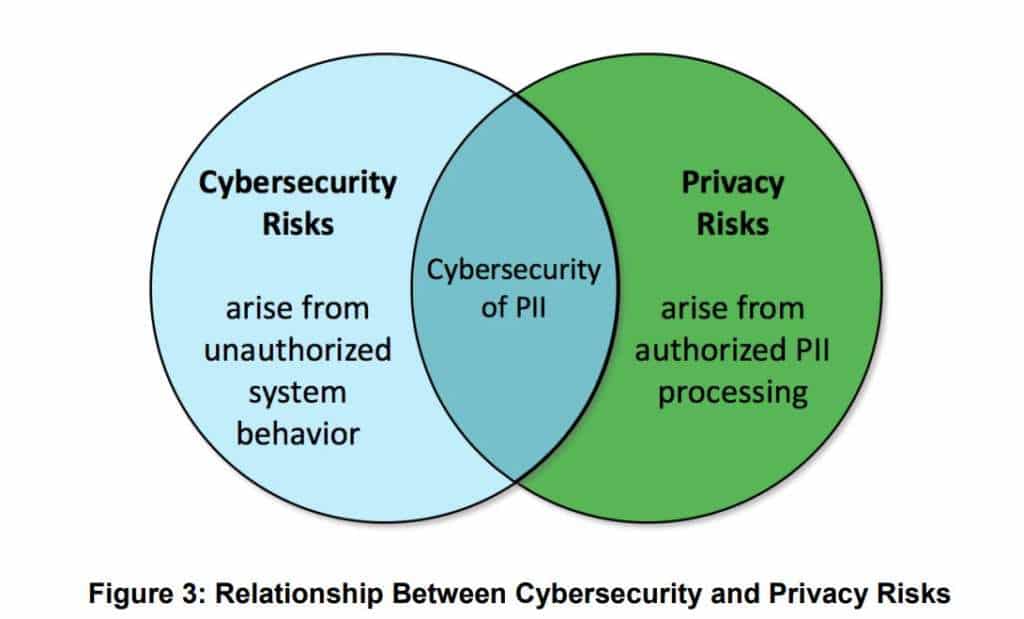
She emphasized that traditional IT systems and IoT are inherently different and 8228 highlights three major high-level risk considerations for managing cybersecurity and privacy risks:
- Many IoT devices interact with the physical world in ways conventional IT devices usually do not.
- Many IoT devices cannot be accessed, managed or monitored in the same ways conventional IT devices can.
- The availability, efficiency and effectiveness of cybersecurity and privacy capabilities are often different for IoT devices than conventional IT devices.
“If you have an IoT system that is attached to a human being, and is perhaps a connected pacemaker, for example, you may want to think about how you apply a patch to that differently than you may want to think about applying a patch to a traditional IT system,” Megas said.
She also noted that several IoT devices are black boxes which lack the same visibility for agency administrators to understand what software version is running or what their operating systems are. In addition, many IoT devices lack the same management features as traditional IT systems.
But Megas said 8228 is a set of considerations. NIST is aware the private industry already uses its cybersecurity framework and that federal agencies also have NIST 853 to guide them in their cybersecurity mitigation
“So it’s more about ‘Hey we recognize you’re already doing supply chain risk management, you already have security controls in place. But here’s where IoT may be different so you might need to go back and revisit some of those and change them up a little bit,” she said.
So far, feedback has been largely positive, she said. A particular bright spot to 8228 has been the document’s appendix, which she said ties closely to NIST 823. The appendix includes a list of security capabilities for organizations to examine whether they are supported with respect to their IoT devices.
Megas said that in the past, hearing from stakeholders at workshops and talks nationwide it was clear that many were accepting cyber risks because they had no good environmental controls.
“We received a lot of feedback from private industry that said, ‘Hey we would love you to take that appendix and convene a little bit more with industry, and maybe expand on it a little bit, maybe start looking at whether we can start articulating these as a baseline so that we can start saying that any IoT device should support this minimum set of security capabilities,” Megas said.
The next round of public comment will be followed by a “roadshow” of workshops and talks, she said.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Amelia Brust is a digital editor at Federal News Network.
Follow @abrustWFED





