Analysis
-
Everyone involved in federal software development knows the percentage: 80% of the federal IT budget goes to maintaining existing systems. Innovation in technology is forcing these legacy systems to be able to interact with other systems.
August 30, 2018 -
One solution does not fit all missions. Especially in the Intelligence Community. Jill Singer, Vice President of National Security, AT&T Public Sector, knows firsthand how IC agencies are embracing emerging technologies, while balancing their reliance on legacy operations.
This six-part series reveals the challenges unique to the IC’s missions and explores the pathways to modernization.August 29, 2018 -
Red Hat and other open source companies work closely with the National Institute of Standards and Technology (NIST) using the secure content automation (SCAP) protocol to automate security controls, the General Services Administration’s 18F organization on configuration lockdown.
August 28, 2018 -
Hosted by Dr. Richard Shurtz and Jim Russ. Sponsored by Stratford University. Today we meet the father of the European Internet.
August 27, 2018 -
What are the key strategic priorities for the FBI’s Science and Technology Branch (STB)? How does the FBI Science and Technology Branch share information? Join host Michael Keegan as he explores these questions and more with Chris Piehota, Executive Assistant Director, FBI’s Science and Technology Branch.
August 27, 2018 -
In this exclusive executive briefing, technology experts will discuss the opportunities and challenges with modernizing IT and living with legacy systems.
August 27, 2018 -
Dana Laake and her special guest Teri Cochrane will discuss “The Cochrane Method,” which integrates a multi-level nutritional approach to develop a bio-individualized plan for her clients.
August 20, 2018 -
“One of the critical characteristics, and this is universal, is the idea of finding young people that have a high degree of integrity,” said Chris Costa, director of the International Spy Museum and former special assistant for the president and senior director for counterterrorism at the National Security Council said during the discussion Building a Career in Today’s Intelligence Community.
August 17, 2018 -
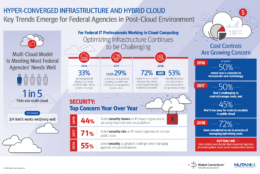
A new survey from Nutanix of federal agencies found 20 percent of all respondents are using a multi-cloud approach, and of them,75 percent say it’s working well or very well.
August 14, 2018 -
Many agencies lack the resources to properly analyze FEVS data. Learn how to identify high impact questions and dig deeper into results.
August 14, 2018 -
Hosted by Dr. Richard Shurtz and Jim Russ. Sponsored by Stratford University. Today we explore the possibility that someone may be spying on you through your robotic vacuum cleaner and we talk about vulnerabilities in our nation’s electoral system.
August 13, 2018 -
Linda Miller, the fraud risk management practice lead for Grant Thornton, said agencies continue to struggle to identify how big of a problem fraud is for their programs, partly because program managers don’t think it’s their responsibility.
August 13, 2018 -
How is the mission of the U.S. Customs and Border Protection's Office of Field Operations?What are CBP's key strategic priorities? How is CBP pursuing innovative security strategies? Join host Michael Keegan as he explores these questions and more with John Wagner, Deputy Executive Assistant Commissioner, Office of Field Operations, U.S. Customs and Border Protection.
August 13, 2018 -
In this exclusive executive briefing, federal systems and cybersecurity practitioners discuss ideas on how to implement secure network automation.
August 13, 2018 -
Dr. Kevin Passero and his special guest Izabella Wentz will discuss a helpful and actionable guide to reverse thyroid symptoms.
August 12, 2018