

Dave McClure, a former Government Accountability Office and General Services Administration executive and now chief strategist for Coalfire, said the company...
A new study is shooting down longstanding concerns about the cloud security authorization process known as FedRAMP.
Coalfire, a third-party assessment organization (3PAO) under the Federal Risk Authorization and Management Program (FedRAMP), studied the six-year-old program and found costs, usage and time to get through the process are much better than the general perception.
Dave McClure, a former Government Accountability Office and General Services Administration executive and now chief strategist for Coalfire, said the goal of the study, which the company is releasing May 3, was to gather and analyze better data about the program and let the federal community draw more informed conclusions.
Coalfire undertook this examination on their own, meaning not at the behest of the government, lawmakers or cloud service providers.
“By doing that, I think we have presented a much more evidence-based document that people can draw their own conclusions whether the FedRAMP office is moving faster enough and quickly enough to the level of efficiency that everyone was looking for,” McClure said in an exclusive interview with Federal News Radio. “I think there was a lot of myth-busting accomplished by a lot of the research we did.”
For instance, Coalfire, which analyzed about 500 of its customer projects under their 3PAO services, found the average time to get authorized under FedRAMP has steadily declined. Under the governmentwide Joint Authorization Board (JAB), vendors can get approval in about six months, which is a 65 percent decrease since 2014. Cloud service providers striving for an approval from a single agency saw the average time it takes to drop by 59 percent to about six months.
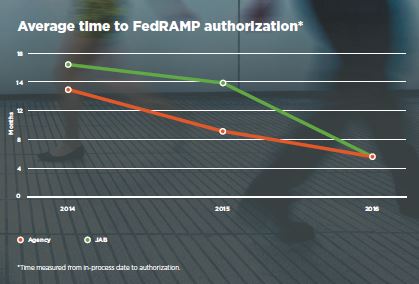
“That’s due to higher quality security plans, better agency support, improved CSP preparation, better standardization and things like FedRAMP Accelerated and the new readiness reviews,” he said.
Additionally, Coalfire determined the average cost to obtain a FedRAMP authorization. While some in the federal community have estimated it could cost as much as $1 million or more, the study found a range of $350,000 to $865,000.
“There is a lot of caveats around the citations done to cost. Number one, there are many phases to the FedRAMP advisory and assessment process, and not all companies go through all of these phases. That, in and of itself, can influence cost,” McClure said. “If we find, for example, a CSP is relatively mature in their security program, has gone through other regulatory assessment frameworks like ISO, SOC, HIPAA or HITRUST, they usually are a little better prepared to go through FedRAMP than, say, a company that is really starting from scratch, putting out products but has never gone through a stringent security review.”
The report includes defined ranges for each of the different phases with preparation support for the FedRAMP application potentially costing the most.

When the Obama administration launched FedRAMP in 2011, the Office of Management and Budget promised to hold agencies accountable for only using FedRAMP-compliant cloud services starting in June 2014.
While there have been no public details of just how much agencies are using FedRAMP-compliant vendors — OMB promised to review agency progress during its regular review sessions — this new study provides a glimpse into just how well agencies are doing.
Coalfire found six agencies — the departments of Defense, Health and Human Services, Commerce, Energy, Interior, Homeland Security and Energy — have used at least 20 CSPs approved under FedRAMP. Amazon Web Services, by far, is the most widely used CSP in government. IBM, Oracle and Salesforce are the other vendors, with more than 16 approved clouds that agencies are using.
“Overall the program really should get a positive mark. We’ve seen an 80 percent growth in the use of FedRAMP certifications. There are now 20 agencies that have used FedRAMP authorities to operate (ATOs) five or more times. The leveraging [of ATOs], while low, is picking up,” McClure said.
One of the original goals of FedRAMP was for agencies to share and use the reviews of vendors with other departments.
McClure said the concept of reciprocity remains a challenge.
“We do see it, and there are good examples to point to where a CIO and chief information security officer, in a matter of days, by reusing a certification, granted an ATO to a company,” he said. “On the other hand, we have examples, and again this is often anecdotally reported or heard, that a particular individual in agencies say they will not accept a package from anywhere. They want to do their own assessment, use their own contractor or their own staff to do it, and don’t believe that anything done by another agency matches to their data requirements, data categorization, risk profile and so forth.”
McClure said this is an area the study highlights as one of the areas agencies have the biggest need for education and training.
On the other hand, the study finds vendors who do the necessary upfront preparation have an easier or at least more direct path to authorization.
“We also found it interesting that we are seeing more involvement in companies than just the IT folks or the product owners of the software or infrastructure solutions,” he said. “We are seeing more CXO involvement. You are seeing more compliant office involvement, broader participation because the company’s success in getting through this is becoming more widely known and a critical success factor.”
McClure said Coalfire shared the report with GSA and FedRAMP director Matt Goodrich. He said, generally speaking, GSA was satisfied with the findings because it was a factual look at the current state of the program and where it needs to go in the future.
“Matt was interested in our computation in the number of agencies that don’t seem to be using FedRAMP. It’s primarily the small and mid-sized agencies,” McClure said. “Computing this is always maybe an exercise in math that requires you to know where exactly you are pulling information from. We simply looked at the most widely available data from Data.gov on the number of agencies and departments, and while there’s lots of progress, virtually every Cabinet department is using FedRAMP and has used it for multiple services. Large independent agencies are definitely using FedRAMP, but when you roll down to the mid-sized and small-size agencies, you don’t see this participation nearly as wide. This means there is an opportunity to penetrate that market, and that’s probably an area where assistance and education are needed in order to get them on board.”
McClure said the Coalfire is planning more reviews of the FedRAMP program to promote the importance of transparency of the costs and efficiencies of the program. He said efforts like this and others become even more important as House lawmakers want to take a closer look at FedRAMP and consider legislation.
Rep. Gerry Connolly (D-Va.) promised several times last year that he would “fix” FedRAMP if OMB and GSA didn’t. In February, he and Rep. Blake Farenthold (R-Texas), both members of the Congressional Cloud Caucus, also said they would take a closer look at the program to make sure it was meeting its goals.
McClure said adding more transparency and discussion around FedRAMP becomes even more important as the policy and legislative efforts around IT modernization increase and agencies are strongly encouraged to use cloud services.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED



