

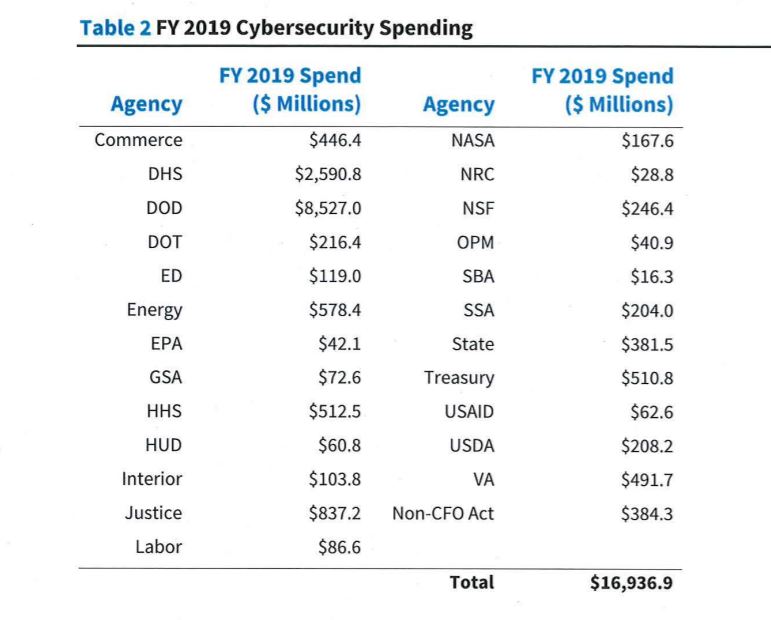
Grant Schneider, the federal chief information security officer, said the 2019 Federal Information Security Management Act (FISMA) report to Congress shows marked...
When it comes to federal cybersecurity, risk management has been one of those buzzwords over the last few years.
The challenge is how to measure whether an agency is truly managing risk or just talking about “managing risk.”
The latest Federal Information Security Management Act (FISMA) report to Congress shed some light on that issue.
The Office of Management and Budget says 72 agencies achieved an overall rating of “managing risk,” which is up from 62 agencies in 2018 and 33 agencies in 2017.
Grant Schneider, the federal chief information security officer, said agency progress in cyber risk management is one of the biggest surprises of the annual report.
“It really shows that agencies are paying attention and doing exactly what we want them to do in cybersecurity, which is taking that risk management approach to their infrastructure and protecting things that are most critical,” Schneider said in an interview with Federal News Network. “We definitely look at the adoption of tools, and the implementation of capabilities. We have a variety of cross-agency performance goals under the President’s Management Agenda that we set for agencies and we track their performance against. Those really become some of the quantitative indicators that go into that more qualitative assessment whether or not an agency is appropriately managing risk and really doing the due diligence and asking some of those critical questions internally.”
The Office of Management and Budget created the risk management assessment process under the May 2017 cybersecurity executive order. The goal of the assessment process is to “help agencies understand and decrease their cybersecurity risk.”
For agencies who are considered to be managing risk, which is one of three ratings, it means they have the “required cybersecurity policies, procedures and tools and actively manages their cybersecurity risks.”
The other two ratings are high risk and at-risk.
Tom Kellermann, the head of cybersecurity strategy at VMWare, said the progress around risk is an important marker, but agencies need to make sure they are looking at the right risks.
“Number one is the systemic risk of island hopping that can be leveraged by hackers. Where with some digital transformation efforts bad actors used to attack other agencies and citizens to steal information, now the heist has become a hostage situation and that is why you’ve seen increase in destruction of systems or information,” he said in an interview. “So the definition of risk must change from operational to reputational and/or systemic. Hackers are not just doing a heist, but they are doing a home invasion.”
An industry cyber expert, who requested anonymity because they didn’t get permission to talk to the press, said the report tends to count a lot of things like how many incidents or the number of agencies implementing the capabilities under EINSTEIN or the continuous diagnostics and mitigation (CDM) program, but it does not provide a perspective on how these activities come together to reduce risk.
“For example, are CDM and EINSTEIN drivers for the managing risk ratings and improvements in inspector general assessments year-over-year, or how do those capabilities lead to a decrease in phishing incidents?” the expert said. “The core here is telling a story that shows more causation and less correlation.”
OMB’s Schneider said he recognizes that just having CDM or EINSTEIN tools in place doesn’t reduce risk by itself.
“All of that data flows in and having those tools are necessary but not sufficient. Really what that means though is are agencies taking the data and information available to them and funneling that into the decision making process where they are investing time, where they are investing resources and where they are investing in other additional tools and how they are working to mitigate for attacks that we know that are out there and patch known vulnerabilities and so some of the blocking and tackling 101 that we want them to do on a regular basis,” he said.
Schneider pointed to the recent experience where agencies had to patch 49 high and critical vulnerabilities on Microsoft software as an example of how agencies are better at managing risks.
“We had gotten with agencies in advance of that announcement to get them prepared to implement that critical patch when it came out from Microsoft. That was something that happened very quickly and we spent a lot of time with DHS monitoring where agencies were at and making sure they were implementing the patch,” he said. “What we tried to get to with agencies is to have more proactive conversations like that. What are we doing to protect ourselves from something coming down the pike as opposed to the conversations asking if we’ve protected ourselves from that vulnerability that was identified last year or the year before. All of the incidents that I’ve ever been involved with has been through a known vulnerability that also had a known and available fix.”
Kellermann said those known and unknown vulnerabilities are leading to some huge problems for agencies.
He said network or island hopping is quickly becoming the biggest problem for not just agencies, but all organizations.
“Smaller agencies can become gateways to primary agencies because there are communications in place that are trusted between agencies. Island hopping is not just network-based attempts or watering hole attacks, which is a new form of reverse business email compromise. They take over your mail server and target senior executives with fileless malware embedded in emails,” he said. “It’s an easy way to hit a small agency and then go after a larger one.”
This also is why Kellermann is concerned not about the number of cyber attacks—which decreased by 8% in 2019 as compared to 2018—but the type of attacks.
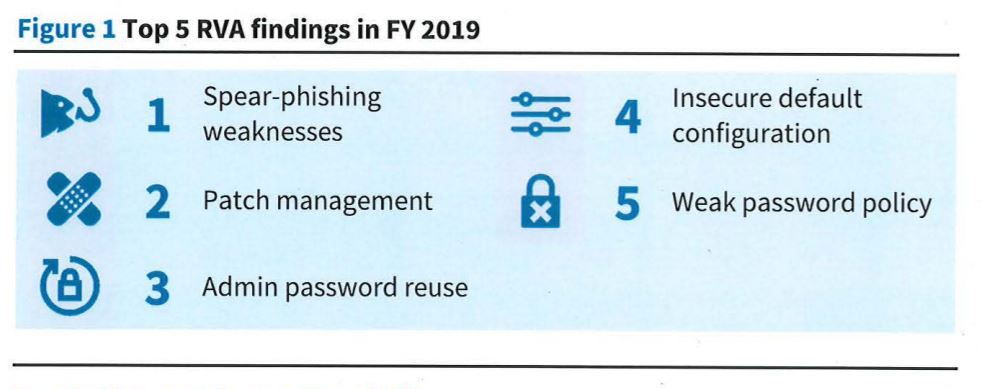
He said he would be worried about the number of attacks that are classified as attrition types more than doubling in 2019 and the continued high number of unknown types.
“Attrition attacks are to degrade or destroy systems, not just using brute force to get in,” Kellermann said. “That means they are getting in through other vectors and once they are in there, they destroy or degrade the system. The big takeaway for me is agencies need to rapidly migrate to a hybrid cloud approach because they can take more control of their data and systems.”
Schneider said the number of unknown incidents remains a big concern despite the 12% drop across the government.
He said OMB is working with DHS to get a monthly readout of incidents to better track problems over real-time.
“We are working with agencies through the Federal CISO Council to make sure we are doing enough digging into what are those others. If there are new categories that we need to add, we can adjust for that,” Schneider said. “Unknown for that number is really not something where we want to be and it’s a challenge we are working on this year and probably into the future as well.”
As for attrition type of attacks, Schneider said agencies are seeing ransomware and other types of disruptive and destructive attacks, like people who are trying to make a statement by defacing a website, increasing in a way that is harming mission effectiveness.
“The potential of a destructive attack could be a denial of service, which we saw some of during the COVID-19 response, are a very big concern because it stops agencies from meeting their mission,” he said. “We need to be searching for the tools that are available that would allow us to protect a user from making a mistake. At the same time, I would prefer if they wouldn’t click on links or make a mistake. But that being said, we know phishing emails have gotten better and better so the expectation is that we want our customers to be cautious, but that is a layer of defense, and cannot be the entire defense so if they do do something we can protect the entire enterprise as well.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED




