GAO finds agencies mostly managed telework network security with a few holes
GAO looked at agencies' system security plans, the results of security control assessments, remedial action plans and whether or not they followed NIST...
During the pandemic, agencies have generally managed to secure networks for remote access, but a sampling of a dozen organizations revealed some cyber vulnerabilities were overlooked.
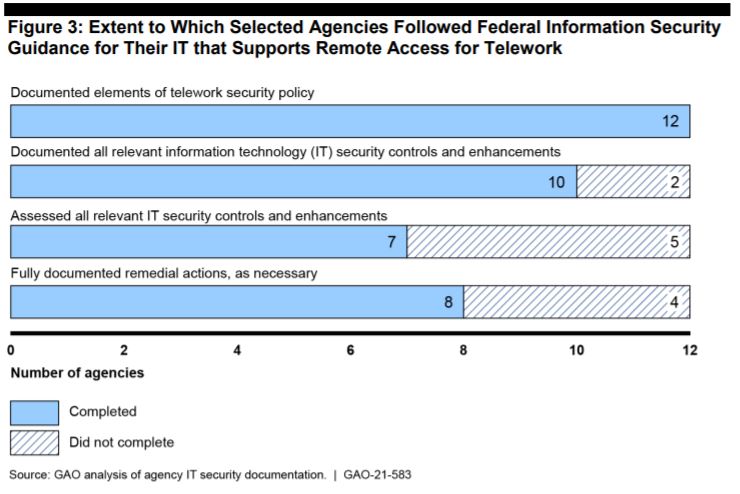
A recent Government Accountability Office report said the biggest needs for improvement were to assess all relevant IT security controls and enhancements, and fully document remedial actions as necessary. The agencies did better at documenting both their telework security policies, and relevant IT security controls and enhancements.
Within agencies’ documentation, GAO looked for system security plans, the results of security control assessments, remedial action plans and whether or not agencies followed cybersecurity guidance from the National Institute of Standards and Technology — particularly SP 800-53.
“If agencies do not sufficiently document relevant security controls, assess the controls, and fully document remedial actions for weaknesses identified in security controls, they are at increased risk that vulnerabilities in their systems View GAO that provide remote access could be exploited,” GAO wrote.
A month before the report’s release, Jennifer Franks, GAO’s director of Information Technology and Cybersecurity, said the agency would expand its reviews to take recent pushes to improve supply chain risk into account, citing the SolarWinds incident and Microsoft Exchange vulnerabilities as examples.
GAO studied actions taken by 12 agencies and ultimately recommendation actions to six: The Securities and Exchange Commission, the Social Security Administration, FBI, the Office of Personnel Management, and the departments of Transportation and Homeland Security. Agencies studied for the report all support national essential functions that must continue during emergencies, have at least 1,000 employees and at least 20% of their workforce is telework-eligible.
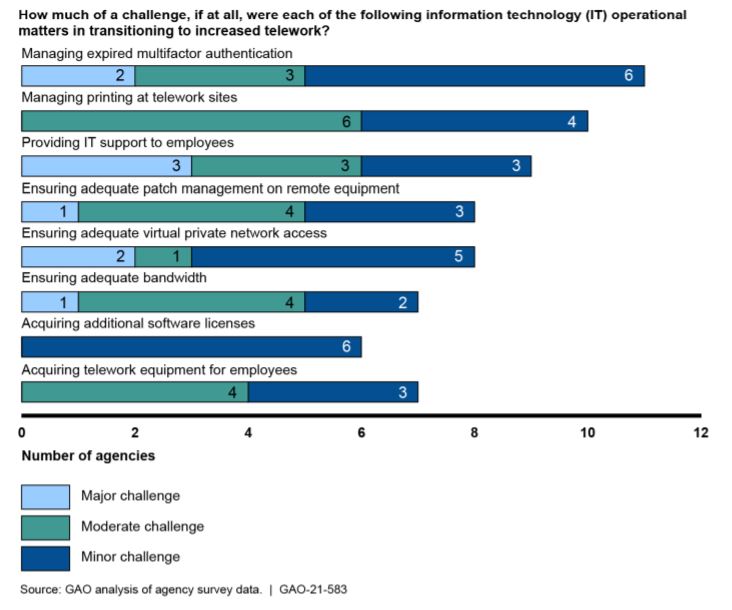
To keep workers connected, all of the agencies used virtual private networks while seven of them used direct application access. Five agencies used application portals and only one offered remote desktop access to teleworkers. Half of them allowed employees to use personal devices, and all enable employees with secure tokens, according to the report. Most of the agencies reported working around the challenges of these tokens’ short expiration times with creating more temporary credentials.
SEC, SSA and Transportation each received some combination of the following recommendations:
- Document relevant IT security controls and enhancements in the security plan for the system that provides remote access for telework;
- Assess all relevant IT security controls and enhancements for the system that provides remote access for telework;
- Assesses and sufficiently documents the assessment of relevant IT security controls and enhancements for the system that provides remote access for telework; and
- Consistently monitor progress toward the completion of remedial actions by including estimated completion dates in its plan of action and milestones for the system that provides remote access for telework.
“For example, as of May 2021, [SSA] had not documented about half of the relevant controls and enhancements in the plan. SSA IT security officials told us that the agency was reorganizing the components that make up the system that provided remote access to the agency’s employees, and that, due to the reorganization, they had not updated the system security plan since 2016,” GAO wrote. “SSA asserted, however, that the controls and enhancements were in place.
It warned SSA and SEC that until those agencies consistently document network cybersecurity controls, officials will not have the information they need to make “credible, risk-based decisions regarding their information systems.”
Other agencies studied but which did not prompt recommendations were the Food and Nutrition Service at the Agriculture Department; the Bureau of Indian Affairs, the National Park Service, the Federal Highway Administration, IRS, Federal Law Enforcement Training Centers and the U.S. Secret Service at DHS; and the Executive Office for Immigration Review at the Justice Department.
GAO conducted the study between April 2020 and September 2021, as part of a CARES Act provision that requires the watchdog agency to report on its ongoing monitoring and oversight efforts related to the COVID-19 pandemic.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Amelia Brust is a digital editor at Federal News Network.
Follow @abrustWFED






