
Agencies faced 14 percent more cyber incidents last year, but security is improving
OMB’s 2017 FISMA report to Congress highlighted several areas where agencies have improved the security of their data and networks.
Sen. Heidi Heitkamp (D-N.D.) wants the Homeland Security Department to be a center of excellence (CoE) for cybersecurity for the entire country.
She told Chris Krebs, during his confirmation hearing to be the Under Secretary of Homeland Security last week, that DHS should be the lead on all things cyber that impact the nation’s defense and national security. If confirmed, Krebs will be the head of the National Protection and Programs Directorate.
“We need a broader, governmentwide, nationwide plan for what we will do in cyber so we are not stepping on each other, so we are not taking missteps that are incredibly costly, and we can’t ignore the small stuff. The resiliency of the foundation, which I will tell you, is fairly porous,” Heitkamp said during the Senate Homeland Security and Governmental Affairs Committee hearing. “We expect you to throw some sharp elbows. There’s been a lot of turf on this and there can’t be. We need a center of excellence and that’s your job in my opinion, to create a center of excellence to be that entity that evaluates products out there that can be, in fact, protective and shield to develop products to better educate the public on how to protect themselves.”
What Heitkamp is asking Krebs to do is take a similar approach to what DHS has taken with federal networks over the last decade.
DHS, for all intents and purposes, has become that CoE for civilian agency cybersecurity, and the latest report on the Federal Information Security Management Act (FISMA) to Congress demonstrates that in may regards.
Let’s be clear early on, DHS is not perfect. It still has plenty of shortcomings and challenges it must face, but the services and help it provides — think of the continuous diagnostics and mitigation program or the EINSTEIN tools — to civilian agencies is undeniably more valuable every year.
The 2017 FISMA report to Congress, which the Office of Management and Budget released in March, highlights several of these areas where agencies are improving their cybersecurity.
“OMB and DHS’s long-running efforts to instill disciplined cyber practices across government helped safeguard agency IT systems in 2017,” the report states. “As a clear example, DHS’s efforts ensured that Federal agencies had already patched their systems to protect against the vulnerability that led to the WannaCry, Petya, and NotPetya ransomware before those attacks swept across the globe. Agencies also expanded their use of continuous monitoring tools and of multi-factor authentication Personal Identity Verification (PIV) cards throughout the year.”
An OMB senior adviser, who requested anonymity, said DHS and agencies now have greater situational awareness about the threats, vulnerabilities and posture of their systems than ever before.
“We focused on the attack vector. Do agencies know where these incidents originate and where the attacks are coming from?” the official said. “With CDM, EINSTEIN and other tools, agencies have an improved understanding of where the [risks] are, and how to mitigate them.”
And having better situational awareness is only getting more important as the number of incidents continues to increase.
Latest Defense News
OMB said agencies reported 35,277 incidents in 2017, a 14 percent increase over 2016 (30,899), and only five reached the threshold of being “major incidents,” which requires immediate reporting and steps.
The OMB official said this is the first year in which OMB and DHS are looking at standard data from agencies. In 2014, OMB and DHS created a standard approach to reporting cyber incidents.
The official said the data shows agencies and DHS are getting the right information, and are able to identify trends across the government.
“There is a delta in incident reporting from 2015 where there were 25,000 more incidents. We weren’t using the information in a meaningful way, so we wanted to verify the incidents to root out false positives,” the official said. “Now the data shows you trends, like email is one of top attack vectors, so we can decide what security controls we can put in place, which is where the Domain-based Message Authentication, Reporting & Conformance (DMARC) protocol binding operational directive came from.”
In October, DHS issued a BOD requiring agencies to implement DMARC to improve the security of emails coming into agency networks.
OMB reported that the number of attacks via email or phishing more than doubled in 2017.
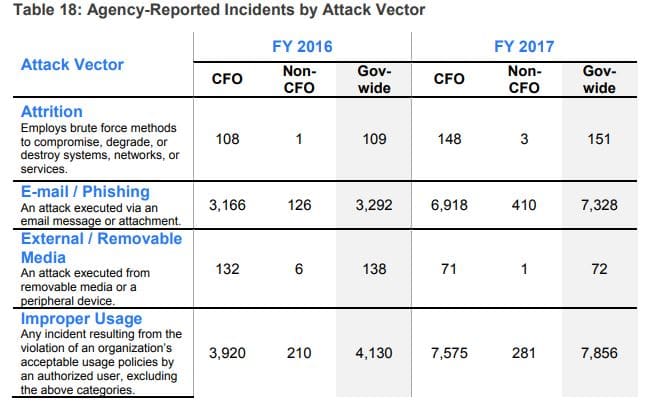
“There is greater awareness at the CIO level, even among small or federated agencies, because CIOs are seeing all the information, the inspectors general are seeing the same information so there is much greater accountability for results,” the OMB senior adviser said. “We are driving accountability throughout the budget and saying those who haven’t performed shouldn’t necessary get more money, and let’s drive reforms and deal with risks. We have a mechanism for better fidelity and training information where to take action to deal with cyber shortcoming.”
In regards to driving accountability, the OMB adviser said while spending on cybersecurity increased by 14 percent in 2017 over 2016, agencies and the administration have a better idea of why spending needed to go up.
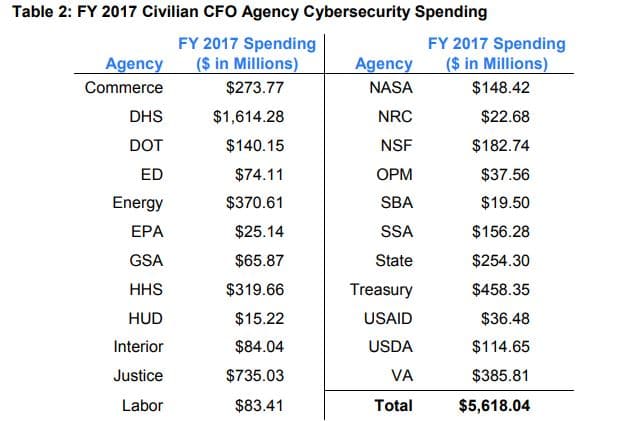
“We are not throwing good money after bad,” the OMB official said. “If you look at the metrics, the cross-agency goals, you can see we are not throwing money at agencies that need it the most. We’ve tied FISMA implementation to the budget. If an agency is underperforming in specific areas, we want to know where do we need to invest to mitigate a threat or add a capability? We also want to augment those programs that are leading the charge like CDM, so we can raise the bar for everyone.”
While the FISMA report shows a lot of progress, agencies continue to struggle in some basic areas. For instance, the governmentwide maturity around cybersecurity continues to struggle, particularly around detecting threats and vulnerabilities.
Agency IGs report hardware and software asset management continue to lag behind OMB goals.
The report also leaves some to question the long-term value of EINSTEIN in terms of return on investment.
DHS has spent more than $820 million on EINSTEIN over the last few years and it only detected 2,200 incidents across all three versions of the program, and E3A blocked just over 600 incidents.
“As of Sept. 29, 2017, DHS reports that, of 119 federal civilian agencies, 31 report implementing all three NCPS [EINSTEIN] capabilities, 17 of which are CFO Act agencies,” the FISMA report states.
The OMB adviser said the report shows that agencies, DHS and OMB are communicating better, which is leading to a better cyber posture governmentwide.
“The report shows people are understanding threats in a way that has context around it, and we are putting resources where they are needed the most,” the official said. “We also have shifted focus to capabilities to drive the threat down and move out of the compliance mode. All you have to do is look at the responses, agencies care about this on a daily basis, not because of a cyber executive order, but because we gave them meaningful reasons, increased engagement and are sharing the risk through a reasonable approach that holds them accountable.”
Read more of the Reporter’s Notebook.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED





