

Current and former federal technology officials say the recent inspector general report on GSA’s Login.gov reinforced why working with the Technology Transfor...
CLARIFICATION: Sonny Hashmi, the Federal Acquisition Service Commissioner, did not take part in the March 20 meeting with the TMF Board as previously reported. GSA also says it alerted the TMF Board in February 2022 and has been regularly briefing them on its progress. The story has been updated to reflect these changes.
The General Services Administration is facing a crisis of confidence.
The third scathing inspector general report since 2016 once again reinforced how headquarters can’t make the Technology Transformation Service play by the government’s rules, in turn leading agency chief information officers and other technology executives to question whether GSA, as a whole, can be trusted.
Interviews with five current federal technology executives, three former technology leaders and industry experts say the trust between TTS, and in some ways GSA, has, unfortunately, once again been broken.
“TTS sells you snake oil and then leaves,” said one agency CIO, who like others for this story, requested anonymity in order to speak candidly about their work with GSA and TTS. “My team must clean up TTS’ mess, and programs are more upset because they didn’t get what they thought they were promised.”
Other technology executives echoed these comments, saying they either don’t trust TTS to come into their agency, or if they do, only in certain circumstances when they can wrap oversight and accountability from their own staff around them.
“If you talk to any CIO, they will tell you they will not welcome having TTS interject themselves into their enterprise. It’s an attitude. It’s like ‘we are here; we are the cool kids and you have screwed things up for years, so now we will fix it.’ But they don’t understand the long-term challenges and needs of the agency,” said another CIO.
Another federal technology executive added, “They come in to solve one problem, and they create two different problems. They are not systems experts. The culture of the organization doesn’t focus on fixing the business processes and the technology. They are very much go in and take a quick hit.”
While many technology executives said they weren’t surprised by the IG’s findings that TTS misled agencies for four years about how Login.gov met certain identity proofing requirements under the National Institute of Standards and Technology Special Publication 800-63-3, the IG report signals TTS remains a horse that cannot be broken, despite multiple attempts across multiple administrations.
“TTS was encouraged to be risk-takers and innovative, but they never realized that they are still federal employees, and there are rules and there is a bureaucracy, which isn’t always bad. It’s a way to make sure you are coloring in the lines,” said a former federal executive familiar with GSA. “I think most people like the idea of TTS, bringing in innovative acquisition approaches and encouraging folks to come in and out of government. But maybe there needs to be an education course for all new employees about the rules of the road in government. Or maybe they need to be a hybrid organization that lets people that come in and out, but also has permanent staff to make sure rules are being followed.”
In fact, sources say during the final days of the Trump administration, GSA leadership seriously considered moving the TTS director, a deputy commissioner of the Federal Acquisition Service, down a notch to an assistant commissioner role, in part because of the organization’s refusal to follow federal acquisition and management principles.
“GSA did think about how to restructure TTS management. It’s unusual to have two deputy commissioners, and organizationally, it would be better to have TTS at [the] same level as other assistant commissioners in FAS,” said one former federal official, familiar with GSA’s considerations. “GSA was in touch with transition officials and floated that management change, and the Biden transition declined to agree with us. It was a way of setting expectations that they are part of the team and were held to the same expectations and all rules around financial, legal and acquisition.”
The concern about TTS from the beginning was, in making the leader a deputy commissioner, it gave them a higher profile with internal and external folks, especially given the size and impact of the organization, which pales in comparison to several of GSA’s other business lines, like technology and professional services.
This latest incident brings back bad memories of GSA’s troubles in the 2000s. And as the old adage says, “those who don’t learn from history are doomed to repeat it.”
It now seems like GSA’s crisis of confidence across many agencies has returned it to the days of its “parking” money scandal in the early 2000s. During that episode, GSA offered the Defense Department and other agencies the ability to improperly extend expiring funds by “parking” the money in assistant acquisition accounts.
Former federal executives said it took GSA several years to rebuild the trust from that incident, and after four years of deceit around the Login.gov platform that not only involves TTS, but the agency’s well-respected CIO, Dave Shive, it’s going to take more than a few promises and well-worn talking points to rebuild the trust.
“GSA got very serious about repairing that trust in the 2000s. Assisted Acquisition Services was a huge business line for them. It went from $7 billion down to $3 billion a year. Now it’s up to more than $15 billion. But it grew in way that is more structured, there is more training and more control around it,” said a former federal executive familiar with GSA and TTS. “It will take a lot of repairs to fix trust issues at TTS and to get TTS to work for agencies again. If GSA is serious about keeping this organization and getting people to understand their value and reestablish some trust, this will take some effort. It is not just briefing people and replacing people, but a long-term effort.”
For GSA, those long-term efforts started on March 20, by meeting with the Technology Modernization Fund Board, and continues Wednesday during a hearing before the House Oversight and Accountability Committee’s Subcommittee on Government Operations and the Federal Workforce.
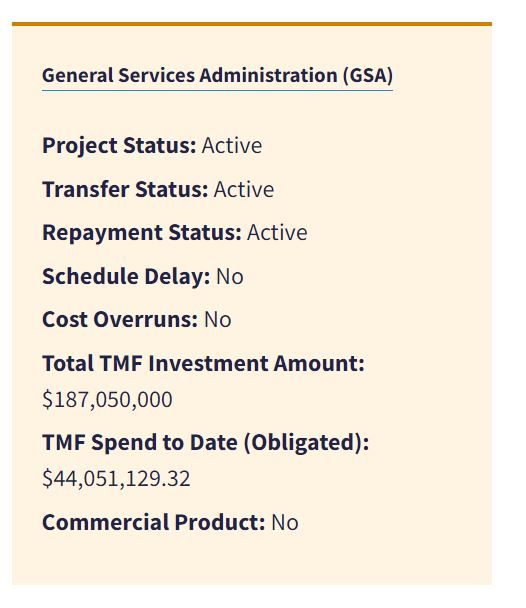
Government sources say GSA started its apology tour when Sonny Hashmi, the commissioner of the Federal Acquisition Service, where TTS resides, and TTS Director Ann Lewis appeared before the TMF Board, which awarded Login.gov $187 million in September 2021, by far the largest amount in the five years since Congress established the IT modernization “loan” program.
Sources say GSA officials explained to the board where Login.gov is today and ensured the board knew about the leadership changes for both TTS and Login.
“There was clearly concern from high levels of government at the meeting,” one government official said. “But there were no specifics or decisions about whether to stop funding Login. I think there was recognition that it’s a new crew running Login, and they are committed to fixing the problems. It’s clear they are certainly willing to build trust back up.”
There is another TMF Board meeting scheduled in the coming weeks where Login.gov may come up again.
GSA says it informed the TMF Board in February 2022 of the previous mischaracterizations of Login.gov.
“Since receiving initial funds from the TMF, Login.gov has briefed the board on at least a quarterly basis, providing detailed updates and sharing regular progress on how funds are being used to achieve agreed-upon milestones – related to preventing fraud, launching in-person proofing, providing better customer service, etc. – in improving Login.gov,” a GSA official said.
Sources also say the CIO and Chief Information Security Officer (CISO) councils are scheduled to meet as well in April, and Login’s problems are expected to be on the agenda.
“Trust in TTS, in Login and in GSA has been frayed. What else about their services — whether building security or procurement that we use — have they been less than transparent about?” said another federal technology official. “I think a lot of us will demand more evidence and transparency about how they are doing business.”
Clare Martorana, the federal CIO and chairwoman of the TMF Board, said rebuilding the trust in TTS and Login will be important. But she said she has full confidence in the platform.
“It is recoverable. Our expectations are that every single project and program that we run operates with integrity and accountability and transparency. I think that the GSA leadership team has really proven that, but it is a ding, and it does cause pause,” Martorana said in an interview with Federal News Network. “We as a board are fully interrogating the process that we went through for the investment, making sure that we are going back and looking at the milestones that we were managing to in all of our delivery, to make sure that we’re doing our job, because we are the stewards of the taxpayer dollar, as well as the agencies that get TMF funding. We take this all very seriously, and are having really rigorous conversations, both amongst the board itself, with our TMF program management office colleagues, and with our Login colleagues, because this is something that we’re going to have to build back from as a shared service provider. I have all the confidence in the world that we will be able to recover from this and that our investment has been meaningful for the American people.”
The board has allocated $44 million of the $187 million to Login.gov, according to the TMF website.
Hashmi said in an email to Federal News Network that GSA has used the funding to launch an in-person proofing pilot to support identity verification for some users at 18,000 Postal Service locations.
“Earning and maintaining the trust of our customers, stakeholders, and the public is our highest priority, and that commitment is embedded throughout our Technology Transformation Services programs and initiatives,” Hashmi said. “That is reflected in our management response to the IG report on Login.gov, which outlines how, over the last year, we have taken significant actions to strengthen oversight and implement additional management controls to ensure accountability at Login.gov and throughout TTS. Moving forward, I am committed to fully implementing all of the IG’s recommendations and taking further steps to enable TTS to more effectively deliver accessible, secure and privacy-protecting solutions to our customers and the American public.”
Sources say the TMF Board was hesitant to fund Login.gov from its initial proposal.
Multiple sources say the board felt pressure to approve the investment, despite obvious shortcomings in its proposal.
“The level of detail we saw in every other TMF proposal wasn’t there, and the confidence in the TTS team and GSA was a factor in the doubts raised by the board,” said one source. “Even if one person formally shot it down, there were others on the fence or had hesitation that they didn’t have the right team in place to be successful. There was concern that they couldn’t execute on their plan.”
Another source said there was some who wanted to split the award to Login into smaller amounts, with milestones along the way to earn more funding.
“It was just too big of an award,” the second source said. “But there was an immense surge of money coming in, new people on the TMF Board and this was one of 50-70 proposals that the board looked at over a couple of months. There was a lot of interest to get Login funding.”
The first source said there definitely was fear of a “backlash” if the board voted down the project.
“The board approved it, and like every other project, TTS should have come in every quarter for a deep dive on its progress to show progress,” said the first source. “Every investment has to provide updates, but TTS had a shorter timeline on it and more guardrails for oversight. It’s unclear if the board ended up keeping TTS on a short leash.”
While the TMF Board hasn’t decided how it will turn up the scrutiny on Login.gov, sources say they should demand more transparency and demonstrate what the funding is going toward.
“If I were on the board, I would want appropriate levels of detail and not a sales pitch. The board is responsible for investment oversight and to ensure the project is spending its money wisely, addressing risks, and meeting its milestones,” said the first source.
Hashmi will get to explain in much more detail in stop two of the apology tour. He will be among one of three featured witnesses at the House subcommittee hearing on Wednesday.

Hashmi is scheduled to be joined by GSA Inspector General Carol Ochoa and Jim St. Pierre, the acting director of NIST’s Information Technology Laboratory.
The subcommittee will focus on determining why GSA leaders did not exercise adequate oversight of TTS and the services it provides, and examine whether Login.gov should remain a central component of the Biden administration’s anti-fraud efforts until it complied with all required standards.
“GSA exists so that agencies can focus on their mission-critical [responsibilities] and not have to worry about services like Login.gov falling short of their promised goal. This wasn’t just a mistake on their part, it was a longstanding misrepresentation, so this hits on the trust front in multiple ways,” said a spokesperson for the committee in an email to Federal News Network.
The Senate Homeland Security and Governmental Affairs Committee also is paying attention to Login’s problems.
An aide for Sen. Gary Peters (D-Mich.), chairman of the committee, said Peters recently spoke with GSA Administrator Robin Carnahan about what the agency is doing to resolve the issues with Login.gov.
“Chairman Peters will continue conducting oversight and work to identify potential reforms to improve accountability and transparency of Login.gov, as well as build trust in this important program,” the aide said.
Another step to rebuild that trust is coming through the acquisition process.
TTS just released a new request for information for Login.gov’s next-generation identity proofing solutions. The goal of the RFI is to get feedback from industry and other experts for how Login can provide secure, simple and equitable identity proofing services. This includes more than 100 mandatory requirements across nine functional categories.
GSA plans to create a multiple award blanket purchase agreement that runs on top of the schedules contract.
Responses to the RFI are due April 7.
The concept of Login hasn’t been popular among vendors since it began in 2017, with many seeing it as direct and, to some, unfair competition with the private sector.
Blake Hall, the CEO of ID.me, one of the most vocal critics of Login.gov, said competition and choice is an important aspect of the identity and access management effort across government.
“ID.me has long been committed to a future where consumers, not data brokers or government agencies, have control of their own data online. We are confident our pass rates and equity metrics significantly exceed rates provided by data brokers operating at a similar level of security. Government agencies need transparency around performance metrics to evaluate solutions through the lens of security and accessibility,” Hall wrote in an email to Federal News Network. “At the same time, all cloud service providers should be independently audited and certified against NIST assurance levels. This is already the case for private sector developed solutions. Public-sector solutions should adhere to oversight as well to ensure a level playing field.”
ID.me isn’t without its own challenges. The IRS pulled back on its use of the commercial service after evidence emerged that ID.me’s facial recognition identity proofing service wasn’t at a high enough quality.
This shows the challenges faced by Login.gov in doing advanced identity proofing aren’t confined to the government. But it’s also why the false assertions left so many frustrated, because it was a well-known problem across government and industry that the NIST standards were difficult to meet.
This is why, as another industry executive, who requested anonymity, said, it doesn’t make sense for GSA to keep pushing Login.gov as a government-off-the-shelf platform.
The executive said GSA’s underlying technology can’t be as agile as industry, no matter how much money they get from TMF or Congress.
“Login just can’t evolve fast enough and scale quickly enough to handle the needs of the agencies,” the executive said. “Industry is incentivized to do the right thing because there are replacements out there if a customer doesn’t like the services we are providing. But if Login doesn’t do right thing, what’s the incentive to change or fix?”
The executive added the consistent feedback they received from government about Login has been that it’s too expensive and the customer service is lacking.
Federal executives agree that the price and services from Login has been a tough pill to swallow for some time. However, almost every executive talked to for this article agreed that there is a need for a Login.gov-type of platform. One that provides basic identity account management through username, passwords and multi-factor authentication.
“Login has gotten a lot better over the years. What they are doing now is quite good. It’s nice to have a single point from customer experience perspective too,” said another federal technology executive. “I think it should stop short of going beyond what it is today, however. It shouldn’t go into identity proofing space. It should strike a balance with private sector, possibly using them for Level 2 and Level 3 proofing, as industry will solve the identity problem faster than the government will. GSA already solved the account problem.”
Several other CIOs and federal technology executives said they were happy with the service they were getting at the basic levels from Login.
“I’m a strong supporter of a single governmentwide identity management solution instead of having every agency making citizens go through multiple vendors or systems,” said one agency CIO. “We have been happy with Login and are happy to outsource these type of services rather than build our own.”
Another CIO offered similar comments, but said they knew Login oversold their capabilities, especially around identity proofing.
Though some reports have said the White House is considering through an executive order on managing digital identities, federal executives cautioned against mandating the use of Login .
“Managing the identity piece makes more sense for agencies to own and implement. That way they can do threat hunting and other security pieces over top of it, and we are better set up for those efforts,” said a federal technology executive. “But where you have federal agencies who do not have the necessary technical capabilities to manage identities, maybe give them the option in future to use an offering from GSA and Login, but they need to stop short of a mandate.”
Mandate or not from the White House, it’s clear that federal executives will not turn away from Login anytime soon. But GSA’s bigger challenge is can they reel in TTS and fix its reputation? Or is the third IG report in six years the final nail in the organization’s reputational coffin?
Several former and current federal executives said if GSA is serious about changing TTS, it has to start at the top, with Carnahan taking the lead. The concern, of course, is she comes from that culture, having run 18F’s state and local group previously.
The executives give high marks to Hashmi and expressed sympathy for him inheriting the mess.
“What got me was systematic breakdown across GSA among several offices — FAS, CIO, TTS. That to me led the question of who is actually managing GSA these days, and if they knew what this program office, which was never revenue-neutral, was doing and what are they hoping to accomplish?” said one federal technology executive. “GSA or others have to ask why is [the] TTS head a political appointee? I’m not sure anyone knows why that is the case. If you are trying to run this as a governmentwide service, do you really want politicals in the middle of this? Or would it better to be seen as a good government program and insulated from political pressures?”
Another federal executive said the Office of Management and Budget should consider pulling Login out of TTS and GSA altogether. Maybe even make it part of OMB or its own standalone program.
“That is not the model usually done, but the amount of trust agencies will hand off to Login, you don’t want 14 levels of leadership between you and accountability of the program like it is now,” the executive said. “You are talking about a tool leveraged by the vast majority of American people, so I think the administration needs to create such scrutiny and accountability around it that they will ensure they deliver on their promise.”
A promise that is well supported, but a trust that has been broken.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED



