

Leaders within the federal and private cybersecurity sectors explained why micro-segmentation is as important as other pillars and how to begin doing...
Micro-segmentation is a pillar of zero trust, but is often put off when agencies work on upgrading their cybersecurity.
Leaders within the federal and private cybersecurity sectors explained why micro-segmentation is as important as other pillars and how to begin doing micro-segmentation — including roadmapping data — during an event sponsored by GovExec on Aug. 15.
While the Cybersecurity and Infrastructure Security Agency’s Zero Trust Maturity Model lays out five pillars to implement the transition to zero trust, it does not provide a set starting point.
Pushing off micro-segmentation is a mistake malicious people can take advantage of, said Gerry Cason, the chief information officer for the Department of Health and Human Services’ Office of the Inspector General
Micro-segmentation breaks down an enterprise into smaller manageable security enclaves in order to contain breaches.
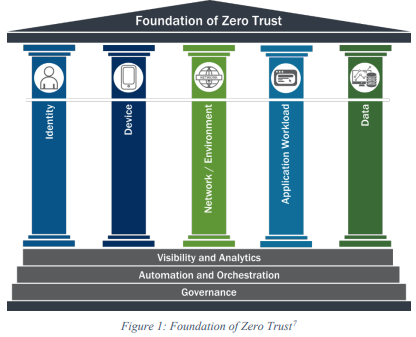
It’s a component of the network and environment pillar of version 1 of the Zero Trust Maturity Model, which CISA developed in June 2021.
Caron said implementing micro-segmentation is often overlooked because people migrate toward implementing the identity aspects of zero trust, which is more familiar.
“So often an adversary breaches a network, but they don’t reach the system they’re targeting. They find whatever niche in the armor that they can find, and then they start working their way through the network,” Gary Barlet, chief technology officer at Illumio and former CIO of the Postal Service Office of Inspector General, said during the discussion. “With micro-segmentation, you can really lock that down.”
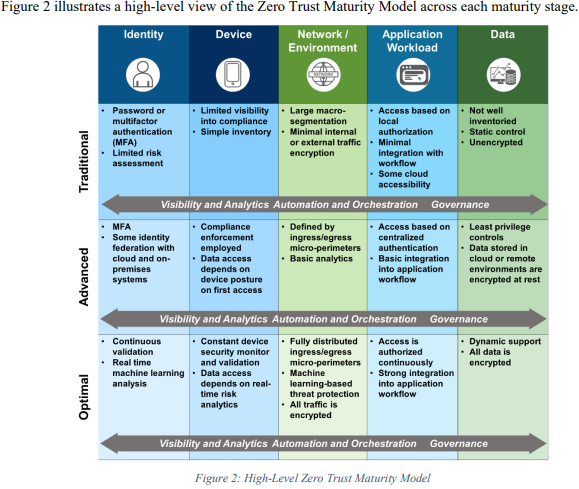
Agency’s zero trust policies are tracked through three stages for completion of each pillar: traditional, advanced and optimal. In order for the framework to be considered advanced or optimal, an agency’s network must include micro-segmentation to contain breaches.
Barlet said micro-segmentation’s goal is not to build an impenetrable wall from hackers, but instead to defend internally, one box or application at a time after someone has breached the outer defenses.
“It definitely is a game changer. I think it needs to have a little more emphasis, and I think [it] is an utterly important part in zero trust architecture,” Caron said.
Steve Haselhorst, the zero trust program manager at the Federal Deposit Insurance Corporation (FDIC), said implementation of micro-segmentation begins with understanding your assets and protecting the most important ones.
He suggested the top down method: Start with things that matter the most and work your way down. Focus on your “crown jewels” or “critical assets.”
In order to identify those critical assets, Haselhorst and Caron emphasized the importance of data-mapping and understanding the assets you have to help decide what to micro-segment first.
Data-mapping includes understanding where data is coming from and going so excess crossover between applications can be turned off and segmented to contain breaches. That understanding also helps you determine, which is the most important and where to begin.
Caron said when data-mapping, ask “what does normal look like.”
“If you don’t know what normal looks like, how are you gonna be able to implement these policies for when abnormal happens,” Caron said.
At HHS, Caron started with the data as the agency implements zero trust.
“What facilitates access to the data is an application; an application sits on a device; it needs to be hosted somehow and then in network you need connectivity somehow,” Caron said. “And then it’s [the] right data, the right users at the right time and you want to make sure that data has integrity, so being able to understand what that data is, is very important as you work back.”
“Understand your crown jewels, focus on your crown jewels, but don’t make your first implementation on your crown jewels,” Haselhorst said.
While you want to protect those critical assets first, Haselhorst said to learn and make your mistakes on something that’s not necessarily as important so you get it right and get good at it.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Abigail Russ is an intern with Federal News Network.



