

As the insider threat space constantly evolves, the Office of the Director of National Intelligence has a new framework designed to withstand the ever-changing...
Seven years after the Obama administration directed all agencies to establish fully functional insider threat programs, the Office of the Director of National Intelligence said it’s finally seeing some progress on some particularly stubborn challenges.
But the insider threat landscape has changed so much since the 2011 executive order that ODNI’s National Insider Threat Program has created a new framework to help agencies navigate a particularly dynamic environment.
“The threat landscape is continually evolving, technology is rapidly shifting and organizations are changing in response to various pressures,” the task force wrote. “Our collective efforts to address the insider threat require constant evaluation, fresh perspectives and updated approaches to address current and future risk.”
As with many unfunded mandates, agencies have approached the directive with mixed results and many were slow to stand up and formalize insider threat programs.
Just a handful of agencies met ODNI’s December 2016 deadline to achieve final operating capability on an insider threat program. The Obama administration in quarterly updates on Performance.gov had cited a combination of “organizational culture, legal questions and resource identification” as obstacles that prevented agencies from meeting the original goal.
But while ODNI acknowledged many of those same challenges still exist, more agencies see the benefits of having an insider threat program, Dean Boyd, spokesman for ODNI’s National Counterintelligence and Security Center, wrote in an email to Federal News Network.
“The federal government as a whole has made significant progress in the past year,” Boyd said. “These challenges are increasingly being addressed as formal training of insider threat personnel becomes more prevalent.”
Leaders are also finding ways to devote resources to what’s mostly been an unfunded mandate, he added.
ODNI couldn’t comment on how many agencies today have achieved initial or final operating capability. The information isn’t considered public.
Though ODNI cited agency progress in finding leadership and getting buy-in for insider threat programs, the new framework is designed to help agencies advance past the basic building blocks.
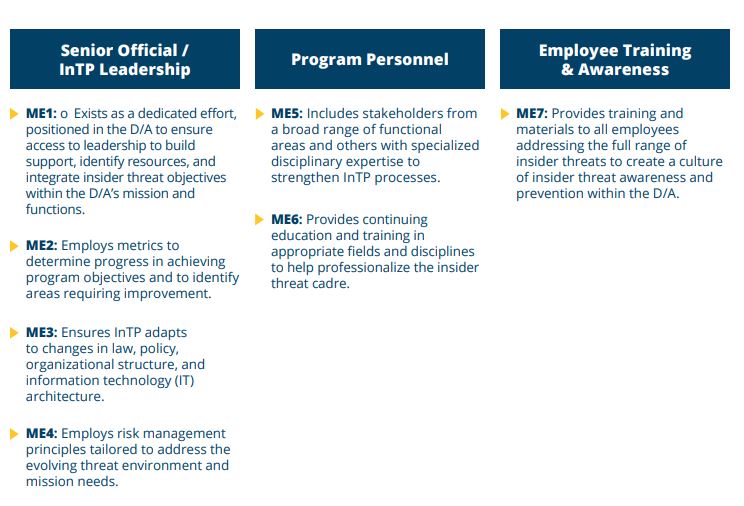
The first seven elements of the task force’s new framework broadly address personnel. The framework instructs agencies to elevate insider threat as a dedicated effort with specific leadership. The entire workforce should receive insider threat training, and employees who don’t work directly with their agency’s program should learn to foster a culture of threat awareness, the task force said.
“The workforce can act as a human sensor, alerting [insider threat personnel] to anomalous activity long before it may be detected by other means,” the framework reads.
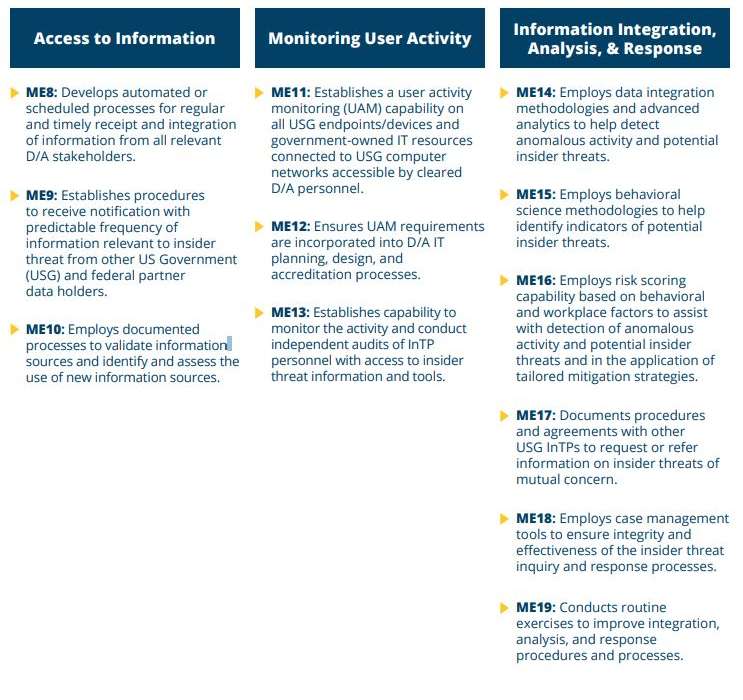
The remaining 11 steps guide agencies in accessing necessary information they need to systematically gather, monitor and analyze in order to track employee activity and behavior.
Agencies, “especially those with a large or geographically-dispersed workforce and diverse sources of insider threat relevant information, can increase [insider threat program] effectiveness through the use of data aggregation and normalization utilities and advanced analytic tools,” the framework reads. “These utilities can help manage large data volume as a first step in establishing a baseline from which to identify anomalous behavior.”
Though the intelligence community has more mature insider threat programs, most agencies are still grappling with the task of installing and advancing user monitoring systems, David Wilcox, vice president of federal business development for Dtex, said in an interview. Dtex provides insider threat technology to some federal agencies.
“It’s the unclassified networks that don’t have much in the way of insider threat activity or monitoring or capability deployed on them,” Wilcox said. “The intelligence community is more mature, but some of their capabilities are due to be replaced. They need to find innovative solutions [and] more cost effective solutions.”
Though the National Insider Threat Task Force sees its new framework as a tool that will likely evolve as the threat landscape changes, it does lay the foundation and gives agencies a specific sequence to follow as they stand up and mature insider threat programs.
The framework perhaps focuses more intently on the human elements of insider threat over best, innovative IT practices agencies might consider to gather, monitor and analyze large swaths of personnel data.
It doesn’t detail how agencies might leverage emerging technologies, such as advanced data techniques, data tagging, artificial intelligence and robotics processing, to advance insider threat monitoring programs, Wilcox said.
“That’s something that might be missing from the framework,” he said. “It doesn’t call specifically for an innovation and a technology maturity plan.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Nicole Ogrysko is a reporter for Federal News Network focusing on the federal workforce and federal pay and benefits.
Follow @nogryskoWFED


