
GSA, DHS make $102M cyber award to kick off busy 2017
The General Services Administration and the Homeland Security Department awarded CGI Federal a task order for the Credentials and Authentication Management (CRED)...
One of the biggest holes in cybersecurity has been understanding the who — as in, who is on the network and what data and information are they allowed to see, change and share.
This is commonly referred to identity and access management, and it’s one of the most important pieces to any cyber system trying to stop the ever-growing threats and attack surface.
That is why the General Services Administration and the Homeland Security Department’s award to CGI Federal for the Credentials and Authentication Management (CRED) task order under phase 2 of the Continuous Diagnostics and Mitigation (CDM) program is so important.
First, let’s talk about the basics of CRED. GSA, which acts as the procurement arm for the DHS program, awarded CGI a $102 million contract on Nov. 1.
“Under this agreement, CGI will provide the participating agencies with tools, sensors, and services to implement certain aspects of credential management, a key activity of the CDM Phase 2 Program that will strengthen policies and practices for all authorized users at participating agencies,” said a CGI spokeswoman. “CGI will also help federal agencies working to comply with the White House’s Cybersecurity Strategy and Implementation Plan (CSIP), which requires strong authentication for network accounts of unprivileged users. We are proud to provide this vital support to the Department of Homeland Security and provide our identity management solutions for all federal agencies involved in the task order.”
To add a finer point to what CGI will do under the task order, DHS wrote in a webinar presentation earlier this year that “CRED binds a type of credential or authentication mechanism to an identity established in TRUST with a level of assurance and is used to grant access (physical and logical).”
DHS offered further discussion in a recent presentation to CDM prime contract holders, saying CRED “addresses regular users, and ensures that they have the appropriate suitability, clearance, security training to access only the information they need to accomplish their duties and no more.”
CRED is one of four task orders under phase 2. GSA/DHS awarded ManTech an $85.4 million contract in July for privilege access management services and tools to ensure “all employees and contractors that function with elevated privileges and responsibilities for accessing and administering federal IT system, are using appropriately secure methods.”
ManTech currently is verifying readiness of about 64 agencies to accept the services and tools for privilege management.
GSA and DHS also will award two more task orders under phase 2 for access control management and security-related behavior management.
The CRED award is an important piece to the CDM puzzle.
A March 2016 white paper from the Chertoff Group sums up why CRED is important: “Agencies should seek one solution that can sync credentials across applications according to government policy. This capability also helps reduce account lockouts and password resets. Automated provisioning…is key to securing and automatically altering privileges throughout employee lifecycles.”
The Chertoff Group says with the growing number of devices agencies are depending on, manual provisioning of access is no longer viable. The White Paper also says having an “access-only” provisioning approach also doesn’t work as recent breaches have shown hackers got on the network using real credentials.
“Successful provisioning solutions use automation to streamline and secure federal agency identities. As users join, move within, or leave an agency, automation reduces the burden of manually provisioning those users, and provides the ability to embed preventive policy controls that help implement functions like separation-of-duty. This automation capability is particularly useful in the management of contractor credentials, as contractors’ transience within the federal government can make their credentials particularly difficult to monitor,” the white paper stated. “A provisioning solution that responds automatically with access to the appropriate resources when an employee or contractor joins a federal agency is much more effective for policy compliance and business productivity. When a user leaves an agency or a contractor’s period of work ends, those same automated processes can be used to de-provision the user immediately, helping to ensure the security of sensitive information by eliminating phantom accounts. Without lifecycle automation and embedded policy controls, an agency may be blind to the types of ongoing lifecycle changes that directly lead to abuse of privilege and privileged account escalation attacks.”
Now DHS has two of four contracts for phase 2 in place, many agency chief information officers and other security executives are waiting with baited breadth to get all of these tools.
The Office of Management and Budget seems to understand the need to quicken the pace of CDM.
OMB conducted a CyberStat from May to June 2016, and presented the results to the President’s Management Council in August, according to a recent DHS presentation, which Federal News Radio obtained.
“In August/September, the Federal CIO met with CIOs/CISOs from each task order group to reiterate importance of program and agree on tracking milestones,” the presentation stated. “Agencies requested additional training and governance.”
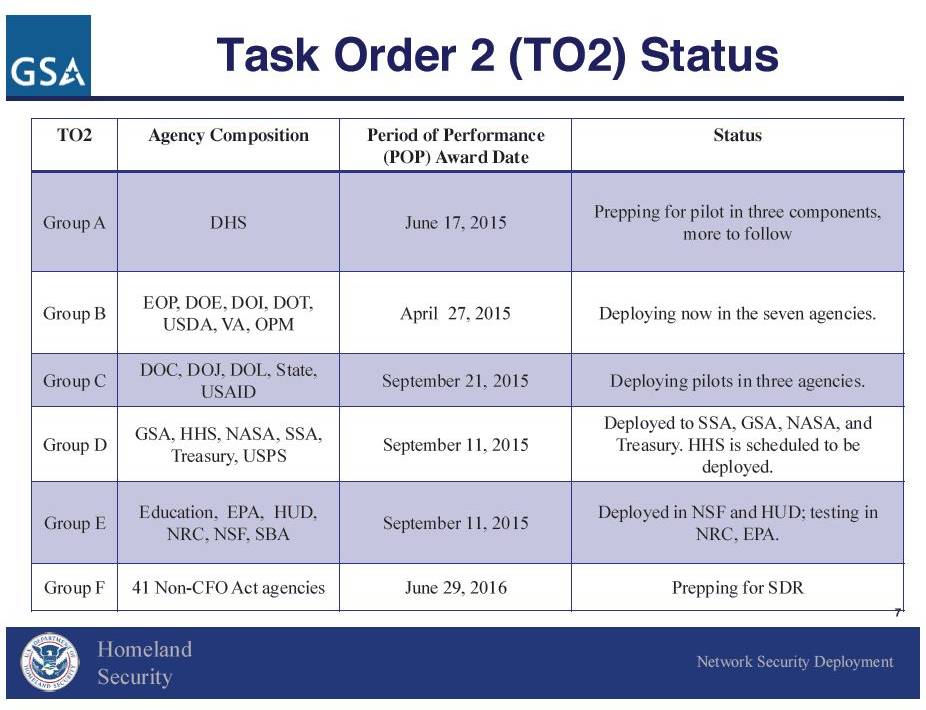
Several other interesting updates in the presentation as well:
- DHS/GSA picked up the third option year of the contract, and the initial contract ends in August 2018.
- GSA/DHS has provided 108 designations of procurement authorities across 44 specific agencies and three states.
- Phase 3 of CDM will try to answer “what’s on the network?” Industry sources say there is no clear acquisition plan for phase 3. The presentation says phase 3 will include packet and content filtering, key management and cryptographic controls and integration with physical access control systems.
- Phase 4 of CDM will include expanded data protection capabilities, including data rights management, data masking and enhanced data loss prevention tools and services, mobile device management and micro-segmentation.
- DHS will work with OMB, National Security Council and other agencies to define the requirements and scope for CDM in FY17 and beyond.
- CDM dashboard update—agencies will receive them based on phase 2 schedules with first initial feeds going to the federal CDM dashboard by the third quarter of 2017.
Return to the Reporter’s Notebook
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED
Related Stories




