
DHS to deliver 2nd piece of cyber puzzle to make moving the cloud easier
CISA's Jeanette Manfra said her office has talked with 50 agencies, cloud and network vendors and others to create guidance to help agencies more easily meet the...
The new Trusted Internet Connections (TIC) policy that the Office of Management and Budget released in September was step one to reducing the burden of using cloud services.
The Department of Homeland Security is getting ready to give agencies the second step in this process.
Jeanette Manfra, the assistant director of cybersecurity at Cybersecurity and Infrastructure Security Agency DHS, said as part of this evolution for how agencies can secure their internet connections, her agency will soon release a TIC document catalog.

“This will help agencies understand what is being protected, where the protections take place and how they will be implemented. If you remove that specific everybody goes through a physical TIC access point, and we place our sensors there and then you broaden that, we needed to broaden the way we talk to agencies about that policy,” Manfra said on Ask the CIO. “We had a bunch of interagency working groups. We’ve talked to over 50 agencies. We’ve talked with the Enterprise Infrastructure Solution (EIS) vendors. We’ve talked with the cloud service providers. We’ve done some pilots, both successful ones and others that we are continuing to work through. We really realized that unlike the previous iterations of TIC, we can’t have three use cases that will work for everyone. There’s a lot of unique ways and unique approaches that each agency will need to take.”
The document catalog will have some use cases now and others will be added later. Additionally, DHS will include other guidance for agencies based on feedback from cloud service providers and other vendors for how best to implement TIC 3.0 requirements.
Manfra said one important part of the entire new TIC 3.0 policy is maintaining the network visibility DHS and agencies gained through the EINSTEIN intrusion detection and intrusion prevention tools that agencies and vendors incorporated into the TIC software.
“We’ve seen a lot of usefulness with EINSTEIN in preventing and blocking malicious emails or DNS traffic. What the shift in evolution is, as we think about EINSTEIN, is really tied to thinking about TIC and cloud,” Manfra said.
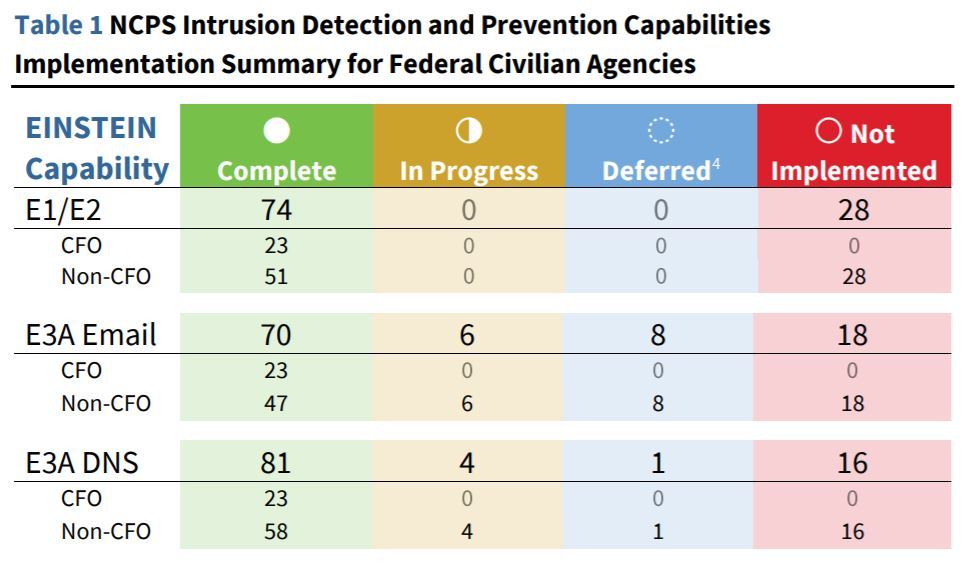
OMB reported in its annual Federal Information Security Management Act (FISMA) report to Congress that as of September 2018, DHS reports that, of 102 federal civilian agencies, 70, including all 23 CFO Act agencies, reported implementing all three National Cybersecurity Protection System (NCPS) capabilities, which includes the EINSTEIN tools.
The implementation of TIC is one of several initiatives DHS is spearheading across the government.
DHS tasked Manfra’s office to help the agency’s chief information officer’s office develop a vulnerability disclosure program from third party in response to the Secure Technology Act.
“We are working closely with them to make sure that at the DHS level they are able to have a system and policies in place where they can have third party reports identified with DHS systems,” she said. “At the national level, we are starting with that program we’ve already had in place, and we want to continue to expand and resource that as we have frankly more researchers and turn to the community to identify some of these hardware and software vulnerabilities to make sure that they are able to be coordinated and released responsibly.”
And while the Secure Technology Act is just aimed for DHS, Manfra said the concepts are something every agency should consider. To that end, DHS is working on guidance for how agencies can create vulnerability disclosure policies at the program level. She said it’s something DHS and OMB will be talking about more in the coming months.
“There’s a couple of agencies that have been legislatively required to establish either some sort of bug bounty program or vulnerability disclosure program more broadly, and having a strong VDP for vulnerabilities identified on your systems is really important,” Manfra said. “We want to make sure it’s consistent across the agencies. It’s something over the next 30-60 days we and OMB will be talking more about.”
Another BOD is coming
DHS is developing a new Binding Operational Directive on vulnerability disclosure and will soon release it for public comment before finalizing it. The updated vulnerability disclosure policy will help formalize the process for researchers and ethical hackers, enlisted through agency bug-bounty programs, to give agencies a heads-up about previously unknown cyber weaknesses without alerting malicious actors.
Agencies already have access to the National Vulnerability Data that CISA and the National Institute of Standards and Technology run to share broad-based threats.
Related Stories
CISA to kick off ‘year of vulnerability management’ with updated threat disclosure policy
DHS also has been working with agencies such as the Food and Drug Administration on vulnerabilities in medical devices, the National Technical Information Service at the Commerce Department and the Defense Department.
The vulnerability disclosure work is another piece of the broader governmentwide cyber effort that includes the continuous diagnostics and mitigation (CDM) program, which now will feature a new and expanded agency-specific and governmentwide dashboard, and cyber shared services.
Under the CDM program, Manfra said 53 agencies are reporting data to the governmentwide dashboard, giving DHS a more comprehensive view of the threats and vulnerabilities across government. The new CDM dashboard is on the horizon as well and will feature artificial intelligence and machine learning tools to improve data analytics.
Manfra said DHS also is rolling out the AWARE scoring system to better understand what agency risk exposure looks like. She said exposure is different than a critical vulnerability. Exposure focuses on how many devices an organization has that may have a particular set of vulnerabilities or how does an organization understand their risk across high-value assets.
Latest Technology News
Shared services strategy under development
Another major initiative coming in 2020 from Manfra’s office is around shared services. OMB pre-designated CISA a Quality Service Management Organization (QSMO) for cybersecurity shared services.
Manfra said CISA is developing the QSMO strategy, starting to set up the office and looking at couple of services and defining what those standards are and how they will be delivered. She said security operations-as-a-service will be one of those shared services, and vulnerability disclosure and possible some others are under consideration.
“For the next 6-to-9 months, the focus is on building the strategy, defining the services to be delivered and doing some pilots with agencies,” she said. “We will take some lessons learned from the pilots and build them into the program to mature the QSMO more fully.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED








