 Exclusive
Exclusive Exclusive
DeRusha says new 2023 cyber metrics reflect agility needed in today’s environment
Chris DeRusha, the federal chief information security officer, said new FISMA metrics will ask agencies for more granular data on how they are meeting administr...
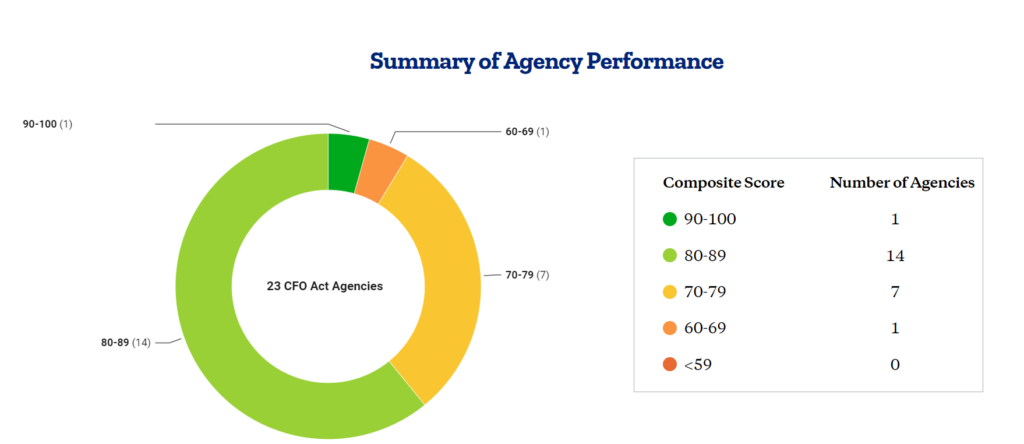
The Office of Management and Budget offered the first details of agency progress against new cybersecurity metrics on Dec. 14.
The administration graded agencies against each of the five areas — identify, protect, detect, respond and recover — of the cybersecurity framework from the National Institute of Standards and Technology. Each agency received a composite score out of 15 for all but the protect category, which OMB based the score out of 40.
Chris DeRusha, the federal chief information security officer, said the goal for the fiscal 2022 Federal Information Security Management Act (FISMA) metrics was two-fold.
“It was important to align to what the inspectors general are using for their assessments. It just standardized around that,” DeRusha said in an exclusive interview with Federal News Network. “Second, all of the FISMA metrics that we put in 2022 are things that we want to be driving as a priority. Either things that agencies have been working on for a while or performance or institutional capabilities or things that came from [the cyber executive order from May 2021]. We’re looking to really capture them and drive them because maybe they need more work, or there’s opportunity for improvement in those areas or challenges that we want to address.”
OMB released the new metrics and scores ahead of the release of the 15th Federal IT Acquisition Reform Act (FITARA) scorecard. OMB’s decision to change the cyber metrics last fiscal year caused much consternation among the Government Accountability Office and the House Oversight and Reform Committee.
DeRusha said agencies have made good steady progress over the last four years around things like hardware and software asset management or mobile device management so it was time to focus on areas such as logging of cyber data and encryption.
To that end, OMB and the Cybersecurity and Infrastructure Security Agency will release the FISMA 2023 metrics later this week.
DeRusha said the new metrics will not deviate too much from the previous metrics based on the administration’s priorities.
“We learned this from engaging the CIOs and CISOs that we need more granularity in what those barriers and challenges are, where they’re having successes, how they’re prioritizing implementation. You’ll see a lot of build out of certain metrics that are that are staying the same,” he said. “Then we’re asking more detailed questions around them to get key insights. That’s a big shift in the theme that you’ll see in 2023. We’ve also put some stuff in there because we learned that, for example, we set very aggressive targets on logging in 2022 and there’s a lot of work in that first maturity cone. We want to be able to measure progress along that curve to get into the first tranche because it’s harder than we’d initially anticipated.”

DeRusha added the 2023 metrics demonstrate that OMB and CISA need to be agile in how they measure cyber progress as well as accurately reflecting efforts to reach a target state.
The need to accurately measure progress toward a target state also is part of the reason why OMB and CISA worked with the IG community.
For decades, the OMB and the auditors have tried to find common ground around cyber metrics and how to measure progress. For example in 2017, the Council on IG Integrity and Efficiency Subcommittee on IT worked with OMB, CISA and others to bring more parts of the NIST framework into the maturity model IGs rated agencies against.
DeRusha said as OMB updated its FISMA metrics for 2022 and now 2023, the IGs played a big role in that discussion.
“We have worked closely on the IG on metrics that they develop and use. The reason that we do that is to ensure that there is alignment. I think that there’s a lot of agreement naturally between the IG community and us based on that they’re out there assessing agencies and see the same things that we do, where there are gaps, where we can make different types of decisions,” he said.
The end result of that collaboration is a two-step approach to assessing agencies.
New guidance, metrics and more
DeRusha said there now is a core set of metrics that the IGs will focus on annually and a second set of process metrics that they will review every two years — half one year and the other half the next year.
“There are three sets now. They’ve broken up all the controls that they need to review so every other year they will do half. Then in the meantime, the IGs also have a core set that gets assessed every year. Those core metrics really do align with a lot of the administration focus areas as well,” he said. “I think it’s just because we see that there’s a set of capabilities that stop bad actors in their tracks. If you look at multi-factor authentication (MFA), encryption and a lot of stuff we’ve prioritized around identity and access management, it’s all the things that we know we need to make faster progress on, and are really going to have the biggest impact. So they’ve decided to relieve the pressure a little bit, and assess a lot of the process controls, which are very important, on the annual basis to make sure agencies have enough time to address the gaps that are being discovered on those core metrics.”
OMB also recently issued its annual FISMA guidance to agencies, where it focused on automation and the expanded use of the continuous diagnostics and mitigation (CDM) program.
Within those core metrics that OMB and CISA laid out for 2022 are things like encryption, MFA and smart patching, which is focused on the most critical vulnerabilities first.
DeRusha said OMB and CISA also wanted to see agency progress with building out their vulnerability disclosure programs and building out red team capabilities to really assess their cyber posture.
“These are the emerging best practices for understanding your actual risk posture and can be really good proxies to assess whether an agency is moving in that right modern direction and modernizing their security program,” he said. “I think there are only around 10 metrics or so sitting behind what we’ve put out publicly. They are pretty representative, when you break them down, of whether there’s a robust program in place at the agency, and whether they’re also pushing on the areas that are the emergent areas. That’s what we’ll keep adjusting and grow to as we get more data in 2023. We’re really excited about some of the metrics we’ll be collecting on and we’ve got some good plans to add those to the public facing dashboard.”
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED
Related Stories






