
How agencies can stop playing ‘Russian Roulette’ with their email security
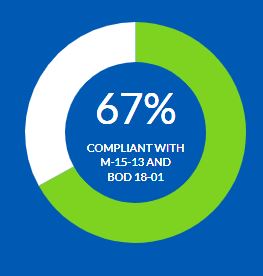
With less than two months before the Homeland Security Department’s Oct. 16 deadline, the number of agency domains still not using the DMARC protocol is more than...
The number of agencies playing “Russian Roulette” with their email remains amazingly high.
With less than two months before the Homeland Security Department’s Oct. 16 deadline, the number of agency domains still not meeting the requirements under Binding Operational Directive 18-01 is more than 200.
The main focus of the BOD from last October is for agencies to move to full use of the Domain-based Message Authentication, Reporting and Conformance (DMARC) protocol, which is an email-validation system designed to detect and prevent email spoofing. They also must implement Hyper Text Transfer Protocol Secure (HTTPS), HTTP Strict Transport Security (HSTS) and disable weaker cryptography standards.
“If you don’t know where an email comes from, that is creating a risk from the number one communications platform,” said Alexander Garcia-Tobar, CEO of VailMail, a cybersecurity company focused on implementing DMARC and other email safeguarding standards, at the recent cyber summit sponsored by 1105 Government Information Group in Washington. “The risk is still growing as email is completely unsecure. Criminals, state actors and others are taking advantage of the fact that email isn’t authenticated. You wouldn’t accept a credit card without swiping it, but it seems to be okay in accepting email on its face value.”
The Office of Management and Budget’s website tracking agency progress against BOD 18-01 and other related requirements shows some surprising agencies that have made little to no progress in complying. The Federal Election Commission is at 28 percent complete. The Consumer Financial Protection Bureau is at 33 percent complete. And the Treasury Department is at 55 percent complete.
These are just three agencies that deal with the public and hackers could easily spoof their email accounts to trick citizens into revealing personal information. Add to that: OMB found in the 2017 Federal Information Security Management Act report to Congress that the number of attacks via email or phishing doubled in 2017 to more than 7,300.
Patrick Peterson, the founder and executive chairman of Agari, another cyber company protecting emails, said 81 percent of the civilian agencies have adopted phase one of DMARC, meaning they can authenticate their email address to other users.
He said 52 percent of the agencies have implemented the second part of DMARC, which focuses on protecting, rejecting and enforcing the domain name security protocols.
“Over the next two-to-three months to get to 100 percent across government will not be easy,” Peterson said. “In order to get to phase 2, agencies have to track down all third party senders, so that means all sub-agencies that use subdomain to send email. That does take work. But hopefully by the October deadlines agencies will be much closer to 75-to-80 percent. That would be a pretty good one-year turnaround.”
HHS case study using DMARC
Peterson pointed to a case study Agari likes to highlight as to why DMARC matters so much. Agari worked with the Department of Health and Human Services to protect the HealthCare.gov website.
After implementing DMARC in 2016, HHS saw no phishing campaigns against the popular health care website.
“Their chief information security officer sent us a note saying there was no phishing going on and he thought there was something wrong with system. We doubled checked it, and found everything was fine,” Peterson said. “The emails went to reject and didn’t get delivered. The bad guys had gone off to attack other agencies because emailing citizens with fake notices wasn’t working well.”
An example such as this one should be enough to convince every agency and private sector organization to move quickly to DMARC.
Peterson said there are 217 domains subject to directive not yet compliant with phase 1, but a majority of the consumer facing ones, including IRS.gov, HealthCare.gov and others are in good shape for phase 1 if not also for phase 2.
But that’s not the case, most surprisingly, at the intelligence community, including the CIA, the Office of the Director of National Intelligence and the Terrorist Screening Center, which OMB’s website shows are 0 percent complete. Now to be clear, the IC doesn’t have to comply with the BOD because national security systems are exempt, but it’s nonetheless surprising.
John Sherman, the assistant director of National Intelligence and Intelligence Community chief information officer, said in an email to Federal News Radio that the IC has a range of activities to implement cybersecurity best practices.
“Cybersecurity is a key priority of mine, and IC CIO is currently in the process of coordinating with the Intelligence Community a cybersecurity implementation plan that will identify the foundational tasks needed to improve our safeguarding posture and drive some really important conversations on risk,” he said.
DoD to implement email security by Dec. 31
At the same time, lawmakers want DoD to implement DMARC. In the 2019 Defense Authorization bill, Congress included a provision requiring the Pentagon to implement the email security protocol.
Additionally, lawmakers also are requiring DoD to implement future BODs by having the DoD CIO “notify the congressional defense committees within 180 days of the issuance by the Secretary of Homeland Security after the date of the enactment of this act of any Binding Operational Directive for cybersecurity whether the Department of Defense will comply with the directive or how the Department of Defense plans to meet or exceed the security objectives of the directive.”
Latest Technology News
At the same time, DoD CIO Dana Deasy told Sen. Ron Wyden (D-Ore.) in July that the Joint Force Headquarters DoD-Information Networks (JTF-DoDIN) will issue a tasking order by mid-August to implement the BOD’s requirements with a completion date for most requirements by Dec. 31.
But even if you take out the IC and Defense community, the number of domains that still have a long way to go with less than 60 days left is disconcerting for many reasons.
Rob Holmes, vice president of email security at Proofpoint, said the biggest challenges for agencies include identifying legitimate senders, finding internal owners of email programs/mail flows and working with authorized third parties to align their sending practices with the constraints of the DMARC standard.
“While there are no technical reasons why certain agencies may not be able to deploy DMARC, there are technical reasons why it may be more difficult and risky for some agencies to deploy DMARC,” Holmes said. “For example, if an agency has a particularly large and/or complex email ecosystem that uses a number of different email service providers across different locations with different change control processes. Some agencies might feel that the BOD 18-01 was sprung on them and therefore might not have the necessary DMARC deployment funds and resources in addition to an already established budgeting cycle.”
Marcus Christian, a cybersecurity and data privacy attorney with Mayer Brown and a former executive assistant U.S. attorney for the Southern District of Florida, said DMARC implementation is a good news story for agencies. He said this is a good example of federal employees getting ahead of the private sector and changing the perception that the government can’t be ahead of the private sector when it comes to technology.
“There is no reason why all of these domains couldn’t be secured by DMARC,” Agari’s Peterson said. “Even those that aren’t used all that often are actually easier it is to apply DMARC to. We don’t see any rhyme or reason why agencies can’t meet the Oct. 16 deadline. It’s just a matter of agencies having their act in gear.”
Read more of the Reporter’s Notebook
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED
Related Stories





