
NIST’s final version of agency cybersecurity guidance builds trust, encourages IoT conversation
The National Institute of Standards and Technology released its final version of Special Publication 800-160. Federal cyber officials say they want the guide to not...
A national dialogue, a flight plan, an inflection point and a welcome.
The National Institute of Standards and Technology on Nov. 15 released the final version of Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems — NIST Special Publication 800-160 — a flexible guide for stakeholders to apply to their cybersecurity systems.
The primary objective with 800-160, said NIST Fellow Dr. Ron Ross, is to bring the computer security world into the system engineering world and get the same level of trustworthiness that you would “when you cross a bridge or fly on an airplane.”
“You have confidence that that airplane is going to land and the bridge is going to sustain you from one side to the other,” Ross said, during the Splunk GovSummit held in Washington, D.C. “That trustworthiness doesn’t happen by accident. You have to engineer that into the system and the things that we really value. And up to this point we’ve all heard the slogan ‘build it in, bake it in, don’t bolt it on at the end.’ And those are just slogans, but in order for you to do that, we have to treat security just like we treat safety. It’s an emerging property of a system, and we have to do certain things to build the trustworthiness into those components that we’ll assemble into our system.”
Industry is building new capabilities and the technological revolution is ongoing, Ross said, and while that’s exciting, “as good as the technology is, and as much as we use it, I think all of us, no matter if you’re in the public sector or private sector, you want to have some level of assurance that what we’re using is safe enough to use.”
“That may not make a big difference if you’re just talking about your smartphone going down or your tablet going down,” Ross said. “What if these computers are going into weapons systems or nuclear power plants or medical devices? Those are big issues where we have peoples’ lives at stake. I think that conversation will begin in earnest now.”
The final publication came on the same day the Homeland Security Department released its “Strategic Principles for Securing the Internet of Things Version 1.0.”
DHS Assistant Secretary for Cyber Policy Robert Silvers said the principles are a first step in securing the front end of IoT.
“These principles will initiate longer-term collaboration between government and industry,” Silvers said in a statement. “Together we will work to develop solutions to address the resilience of the Internet of Things so that we can continue to benefit from the remarkable innovation that is driving our increasingly-connected world.”
The strategic principles instruct stakeholders to:
- Incorporate security at the design phase
- Advance security updates and vulnerability management
- Build on proven security practices
- Prioritize security measures according to potential impact
- Promote transparency across the IoT
- Connect carefully and deliberately
Taking a different look
Retired Brig. Gen. Greg Touhill, the federal chief information security officer, called NIST’s publication “an inflection point for all of us.”
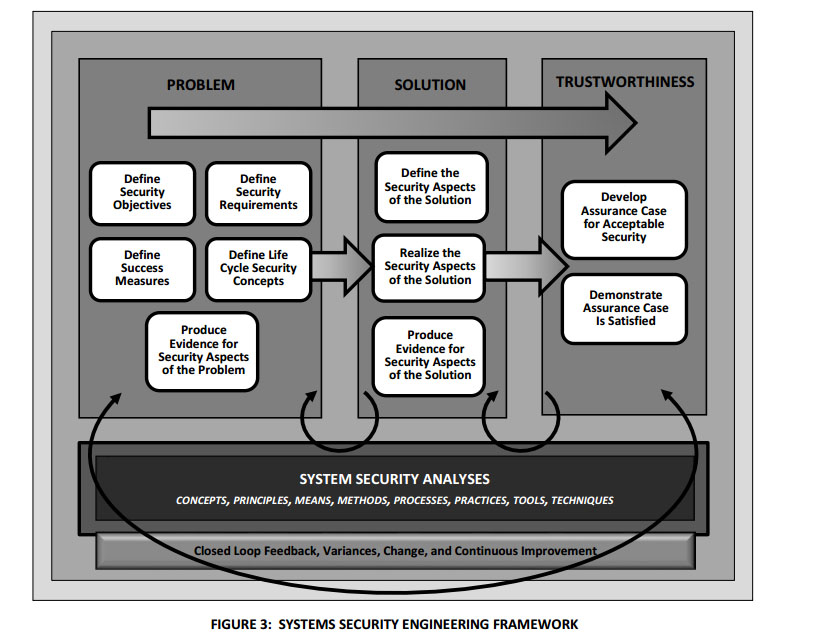
The final version of 800-160 isn’t too far from the last two drafts issued earlier this year. It’s based on an IEEE and ISO joint standard. NIST released the draft version in May 2014 and the second draft a year later.
The way security controls are applied today is through a categorization under the Federal Information Processing Standard. Data and the security system are determined to be low, moderate or high impact, and then a set of controls out of NIST’s SP 800-53 are selected and implemented.
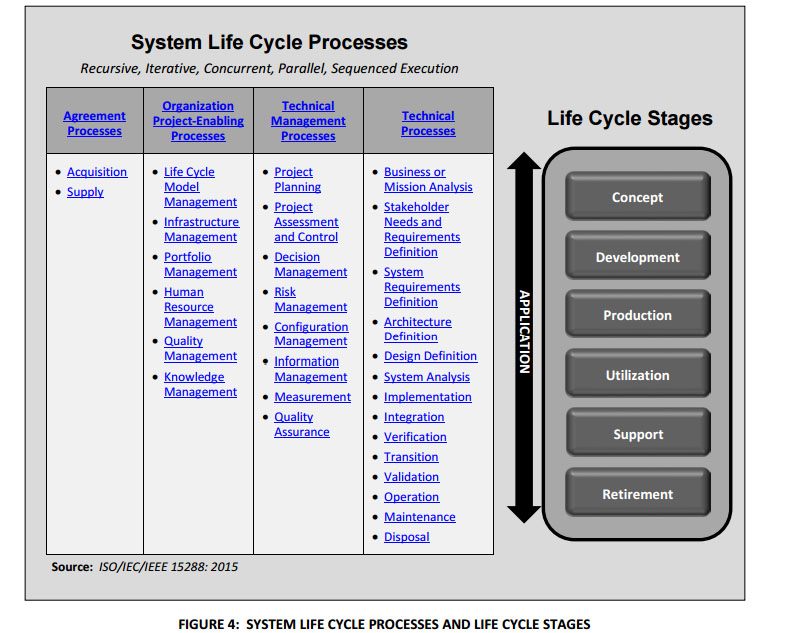
SP 800-160, however, looks at 30 different processes in a Systems Engineering Life Cycle.
The processes are broken down into four categories: Agreement, organization project-enabling, technical management and technical.
Each of those processes is further divided into purpose, outcome, activities and tasks.
For a process such as project planning, the purpose of project planning is to “produce and coordinate effective and workable plans.”
The outcome of this process is having defined security objectives and security aspects, as well as formally requested and committed resources.
Activities and tasks include defining the project’s security aspects, planning technical management and activating security aspects of the project.
Ross said the goal was not to make the guidance mandatory but “as welcoming as possible.”
“This is the start of a national dialogue,” Ross said. “We want to work with industry and academia and our government agencies. We want to provide them information to the best of our ability on how to incorporate security into the life cycle process, but everybody’s going to do that at a different pace.”
Internet connectivity
At least one area where that dialogue is going on is in Congress. The House Subcommittee on Communications and Technology and the House Subcommittee on Commerce, Manufacturing, and Trade are scheduled to hold a joint hearing Nov. 16 on “Understanding the Role of Connected Devices in Recent Cyber Attacks.”
In a statement from Reps. Michael Burgess (R-Texas) and Greg Walden (R-Ore.), the congressmen said the goal of the hearing is to learn more about recent cyber attacks and what can be done to mitigate future risks.
“Internet connectivity remains a vital part of our economic well-being and our national security,” the lawmakers said. “Americans should not have to worry that the convenience and connectivity of the Internet of Things comes at the expense of the resiliency and reliability of the larger internet.”
With 800-160 published, Ross said the next steps for NIST included major updates to SP 800-37 and SP 800-53.
“The cyber problems today are every bit as serious as the Cold War but in a cyberspace context, because these problems sometimes are hidden in vulnerabilities deep in the systems that we can’t even see,” Ross said. “The 800-160 is not a silver bullet, I’m hoping it’s the start of a national dialogue.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.




