
DHS putting the pedal to the metal for one of its major cyber programs
Kevin Cox, the program manager for the continuous diagnostics and mitigation program, said ongoing assessments and mobile security are among the top priorities for...
Best listening experience is on Chrome, Firefox or Safari. Subscribe to Federal Drive’s daily audio interviews on Apple Podcasts or PodcastOne.
The Homeland Security Department is about to add another spinning plate to the already busy Continuous Diagnostics and Mitigation program.
Along with finishing up phase 1 and continuing to push toward phase 2 of CDM, DHS is preparing to work on mobile security, cloud pilots and network management initiatives under phase 3.
Kevin Cox, the program manager for the CDM program, said the new acquisition approach for CDM is letting them add more cyber capabilities faster.
“With phase 3 of CDM we are looking at a big number of capabilities that we want to eventually support the agencies in getting the capabilities in place,” Cox said after speaking at the recent Justice Department cyber summit. “With the DEFEND task order we are able to schedule the work over the six years of the task order. We will focus on four main things starting out for all the agencies.”
The General Services Administration, which acts as the procurement arm for CDM, made two awards under DEFEND so far—a $621 million deal to Booz Allen Hamilton for the seven agencies under Group B in February and a $407 million deal to CACI for DHS headquarters under Group A in May.
“We expect to have for the remaining three CFO Act groups to make awards no later than the July timeframe,” Cox said. “At that point, we will have the five awards in place getting these longer term task orders and enabling the work for phase 3 and phase 4.”
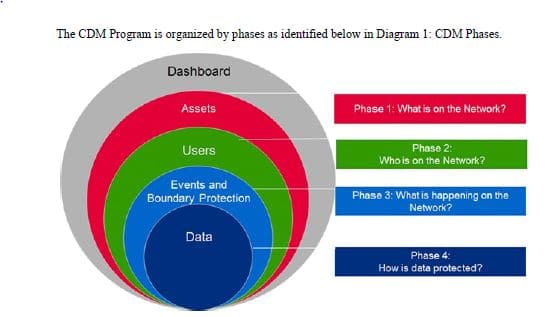
The four initial focus areas under phase 3 are:
Ongoing assessments — Agencies would use automated tools installed under phase 1 of CDM to consistently review the cyber posture of systems.
“This is the first step of the larger goal of implementing ongoing authorizations where we automate as many controls as possible and we monitor the system over time to make sure it stays within acceptable ranges. If anything changes, you can reassess certain controls or the whole system,” he said.
Mobile security — Cox said the capabilities would give agencies visibility from their mobility device management systems by sending data to their agencywide dashboard so they have greater understanding of their mobile devices.
“Initially we want to focus on the visibility of the devices themselves. We want to use what they are already are using,” he said. “If there’s a vulnerability of an Android or iPhone device, they will be able to see what their susceptibility of that is. In the longer run, a couple of years down the run, we want to help agencies with mobile application management, ensuring for the whole mobile environment they have the proper protections in place to protect the data.”
Network access control — Cox said some agencies are more ready than others to begin adding those capabilities of real time visibility of the network. He said as an employee connects their laptop or device to the network, the tools will run an automated check to make sure the hardware is properly configured. And if not, the tools can quarantine off the device until reaches the agency’s standard.
Certificate management— The goal here is for agencies to have one view of all their website certificates. Cox said there are hundreds or thousands of certificates that are tied to web or cloud services so these tools would help agencies centralize that visibility so they will know before a web service certificate expires.
“This will allow you to track certificates and get in front of those renewals and understand how certificates are used to get access to your environment,” he said. “The other key here from a cloud security standpoint is certificates are key to cloud security so being able to understand what certificates are being used to get which cloud service provider and what they are used for.”
At the same time, Cox said CDM will work with cloud service providers to get visibility into their security controls as they provide continuous monitoring and better understand where additional tools may be needed in front of the cloud providers. DHS continues to work with agencies to improve the Trusted Internet Connections (TIC) process through a series of pilots with the Census Bureau and Small Business Administration.
Cox said 20 agencies are sending data to the governmentwide CDM dashboard from their internal dashboards.
He said the target is to have all 23 agencies reporting to the governmentwide dashboard by July. Cox said there are a few technical issues that still need to be worked out.
“With our shared service for the non-CFO Act agencies, we are looking to establish the information exchange for that dashboard around the July timeframe. Then we will start to bring in the visibility from the small and micro agencies as well,” he said. “By mid-to-late summer we’ll start to get visibility across the various agency dashboards. It’s being summarized but it starts to give the federal leadership a good understanding of what the federal landscape looks like.”
Cox said DHS is working the small and micro agencies that already have capabilities in place to feed data to the governmentwide dashboard. For those that weren’t already using data analytic and collection tools, DHS is working with agencies in waves, starting with four of them to get data fed to a multi-tenant cloud.
“Throughout the summer and into the fall, we will be bringing in about 48 agencies that have signed memorandums of agreement,” he said. “At the end of the day, we want to get out to all of the small and micro agencies so we will probably go in to fiscal 2019. We are looking at a population of 75 to 80.”
For phase 4, DHS already is starting to work with agencies to develop requirements for tools and capabilities around data protection, data rights management and data loss management.
“We are developing a data model around phase 4 that we will build into the architecture,” he said. “We will get it to agencies for their review by mid-summer, and then we can identify what the right technologies are to protect that data.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED
Related Stories

Rep. Hurd says CDM is a software implementation problem, he’s only partly correct





