
Fake solicitation highlights growing attacks against federal officials
Miller said she was unaware of any data about the success rate of these types of attacks, but there is plenty of anecdotal evidence of companies losing tens of...
Nagesh Rao was sitting in New York visiting his family when someone on his team at the Bureau of Industry and Security at the Commerce Department headquarters called him about a large box that just arrived.
The BIS chief information officer wasn’t expecting a delivery so, needless to say, he was a bit surprised.
As his team opened it, they found about $10,000 worth of Lenovo laptops and Microsoft Surface tablets.
At that moment, Rao knew the fraudsters were a little too close for comfort.
“I didn’t know to the extent of the fraud. About 3-to-5 months ago, I got email messages and LinkedIN requests about a solicitation on the street. But I didn’t have one out there so I flagged it to our security team,” Rao said. “Some company thought it was a real solicitation and shipped laptops and charged us for shipping under the fake RFQ.”
Rao is the victim of whaling — a new term all senior executives and political appointees need to add to their lexicon.
Think of a phishing attack, but much larger. Think of the casinos and big spenders, who are commonly called “whales.”
A scammer put out a request for quotation on BIS letterhead in Rao’s name and sent it to smaller businesses.
The fraudster called the small business, trying to get them send the equipment to an address in Atlanta. The owners of the company decided something wasn’t right so sent the equipment to Washington, D.C.
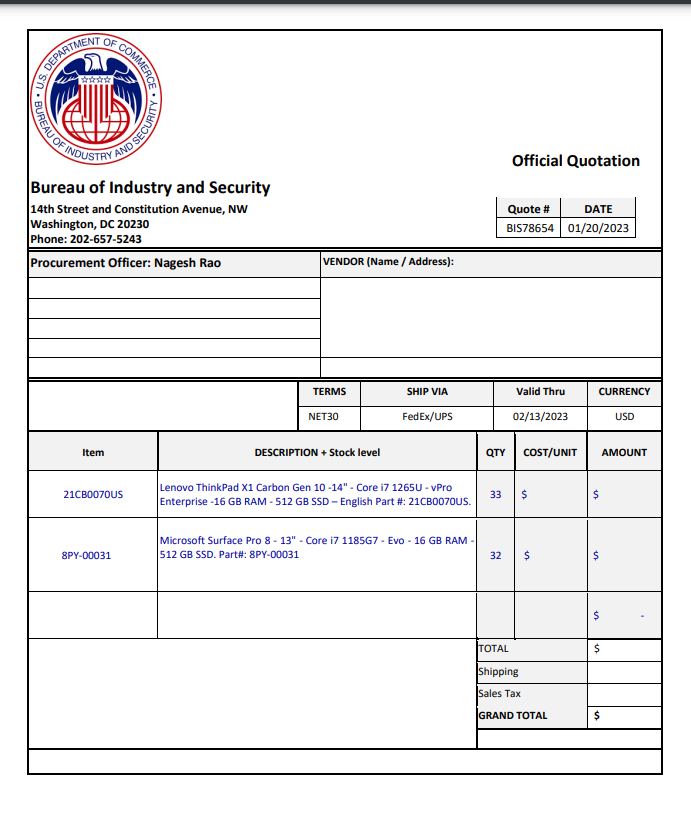
“I have now had about a half a dozen vendors reach out to me about it over the last three or four months, including an unfortunate small business owner who sent equipment to Commerce HQ, instead of to the address in Atlanta, because they were like, well, we’re not sure about the address that they thought was suspicious but there I will send it to Nagesh,” Rao said at the recent ACT-IAC Emerging Technology and Innovation conference. “We had to ship it back and say ‘no this is not right.’ But it’s stuff like that that is happening and so I have to be able to jump on pretty quickly.”
This was the fourth or fifth time Rao has been targeted by these or similar scammers, issuing fake RFQs. He said it’s not just him but several Commerce executives have been the subject of these fraudsters.
Rao said he’s been trying to get the word out over the last months to make sure vendors know this is a scam.
He’s also working with the Commerce inspector general on an investigation.
“This is it gets a little too insane when you actually get the equipment shipped to you,” Rao said.
Rao also posted details, including the fake RFQ, on LinkedIn as a way to spread the word further to the community.
While scammers have often used the federal government as a cover, think of the fake calls from the IRS or Social Security Administration, this is one of the first, or at least most public, attempts where fraudsters posed as a senior executive.
Barriers to perpetrate fraud lower
Linda Miller, founder and CEO of the Audient Group and a fraud expert, said unfortunately whaling is happening all too often.
“Fraud actors are targeting senior officials for obvious reasons. These are people who have more influence over the organization especially the budget, access to money and other things of value. They are high value targets for threat actors,” said Miller, a former deputy executive director of the Pandemic Response Accountability Committee (PRAC) and an assistant director at the Government Accountability Office focusing on fraud risks and program integrity issues. “If you are senior person in an organization, the more presence you probably have online, whether you have spoken at conferences or video or done audio interviews, and that makes it easier for fraudsters to spoof through deep fakes or even to emulate your writing or speaking style. The targeting of senior officials, whether in the public or private sector, is very common right now.”
As agencies saw during the pandemic, the rate of fraud suffered by federal programs increased incredibly. Part of the reason is the shortcomings of the programs to protect against bad actors, but more directly, the low barrier to entry to perpetrate these attacks.
Miller said anyone can go on the dark web or open deep web and get tools, manuals and help.
“Someone who needed skills once, now doesn’t. There is fraud as a service, and you can even use ChatGPT to, say, draft a RFQ in the same language as this one and give them a sample. It will be so similar, have the hallmarks of the organization so to the responding vendors, it looks legitimate. It’s a lot easier to create fake documents, RFPs, emails, invoices, whatever.”
Miller said she was unaware of any data about the success rate of these types of attacks, but there is plenty of anecdotal evidence of companies losing tens of thousands or hundreds of thousands of dollars to these scam artists.
“This Commerce example worries me. This is the type of thing I’ve been talking about for years. The sophistication is growing and is a real problem,” she said. “I’m worried that agencies are not prepared for a more coordinated and sophisticated type of fraud schemes, like in the case of the RFQ. These are the kinds of schemes that I don’t think fraud risk assessments are thinking about. If I suggested this people would think I’m crazy and say it’s not going to happen so why design scenarios and controls around this. But it’s happening.”
To Miller’s point about federal executives being targeted, Rao said when he was at the Small Business Administration a few years ago, scammers pretended to be the agency’s chief of staff asking the CFO to send hundreds of thousands of dollars to a specific account. To his credit, the CFO called the chief of staff before transferring money, knowing something didn’t smell right. The scammers weren’t successful, but this is just another example of the lengths these bad actors are going to.
This is more of a classic example of a whaling attack.
How can feds protect themselves?
Miller said senior executives and agencies can do a few things to better protect themselves.
First, executives can be more aware of their online presence, whether video or audio or written communications.
Second, they should work closely with their cyber teams and using cyber threat reconnaissance tools.
“If this scheme originated from a forum on the dark web, there are cyber companies looking for chatter related to your agency or name. They could say, ‘we picked up interesting thread of discussion of some sort of scheme that may be planned or implemented around this person or organization,’” Miller said. “You can monitor what these guys are doing and where they are talking about it. That is the beauty of open source as there is no honor among thieves.”
Miller said should an executive find themselves a target of fraud, she recommended calling the FBI first and your agency’s inspector general shortly afterwards.
As for the small business, Rao’s team called the small business owner and confirmed they were duped into sending the laptops, but luckily without any harm.
“The small business owner was shocked and grateful we were going to return the equipment,” Rao said. “We told them we weren’t going to reimburse them for the shipping, but we would make sure the laptops get back to them.”
They and Rao were both lucky this time, but Miller said it’s clear federal executives need to protect themselves from becoming harpooned by scammers.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED





