

Lawmakers say they fear cybersecurity mitigation efforts are taking a backseat to the mounting pile of IT modernization initiatives ongoing at the Department of...
When it comes to its annual cybersecurity exam, the Department of Veterans Affairs has a less than stellar history.
VA’s inspector general still considers cybersecurity — despite efforts from an array of prior chief information officers — as a material weakness, according to the most recent Federal Information Security Management Act (FISMA) audit.
This is a common challenge for agencies across government, and VA was one of 18 organizations to earn this distinction in 2018.
Even so, VA holds a unique distinction among other agencies, the Government Accountability Office said.
“When it comes to looking at the length of time that it has consistently reported a material weakness in the security controls over its financial systems for financial reporting purposes, it’s been going on 17 years in a row,” Greg Wilshusen, director of IT and cybersecurity at GAO, told the House Veterans Affairs Technology Modernization Subcommittee at a hearing Thursday on VA cybersecurity challenges. “Few agencies meet that longevity of that particular weakness.”
VA’s inspector general made 28 recommendations to improve IT security controls in its most recent FISMA audit. Most recommendations are repeats from the previous years, said Nick Dahl, deputy assistant inspector general for audits and evaluations.
Lawmakers see these patterns as particularly alarming, especially as cyber attacks have become more prevalent at major private sector health systems.
This all comes as the department juggles several IT modernization initiatives, and members of the House Veterans Affairs Technology Modernization Subcommittee said they feared VA’s cybersecurity posture was taking a backseat to those higher-profile projects.
“My concern is that assessing risk and developing mitigation strategies does not have enough attention,” Rep. Susie Lee (D-Nev.), the subcommittee chairman, said. “Many OIG and GAO reports on security incidents cite management failures or lack of internal oversight as the reason behind the incidents. Too often strong leadership on risk management and information security becomes an afterthought or a paperwork exercise done once a year for the FISMA audit.”
Still, the members, VA’s Office of Inspector General and the Government Accountability Office said there is some slow progress in the right direction.
For one thing, VA has reported fewer cyber incidents in recent years.
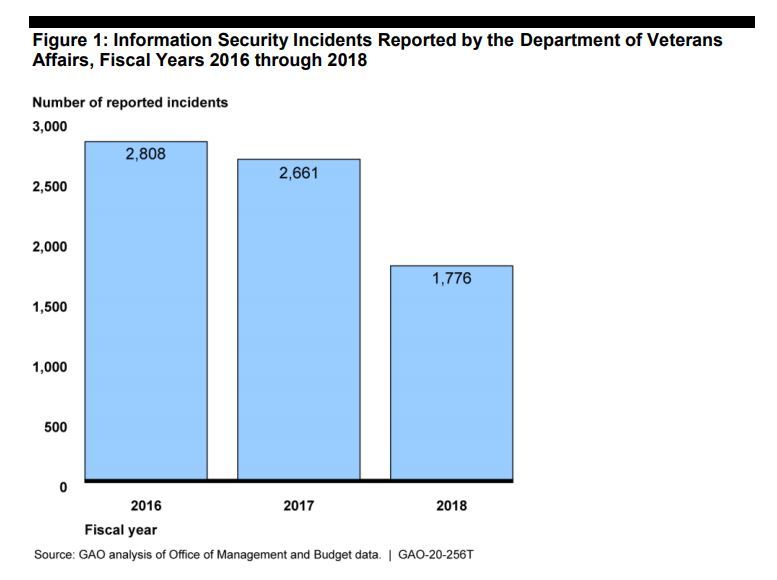
And VA has, the OIG said, made progress in staying on top of cyber-related policies. For example, the department updated its enterprise cybersecurity and privacy strategy this year to align with industry and National Institute of Standards and Technology best practices.
Paul Cunningham, VA’s chief information security officer, came to the agency in January after several years at the Energy Department and Immigration and Customs Enforcement.
He said he noticed several cybersecurity challenges that largely stemmed from VA’s legacy systems. But he did recall some bright spots with VA’s cybersecurity posture.
“We had an incredibly talented pool of people, especially in regards to how we monitor the network traffic and our ability to respond,” Cunningham said. “I also saw a very strong relationship with DHS, which is a very positive thing.”
He said VA’s centralized approach to cybersecurity was a welcome change, citing a newly established, departmentwide Office of Quality, Process and Risk as example.
“They established a risk officer, which is an incredible feat because a lot of organizations have difficulty in getting [one] set up and staffed,” Cunningham said. “It’s a great ally for cybersecurity as a whole to be able to have somebody who is an equal pairing and has [an] unbiased feeding to the CIO and the secretary information regarding cybersecurity risk.”
Cunningham noted some “siloing” in VA’s IT organization but said the department’s technical operations employees had a strong working relationship with its cybersecurity employees. That kind of relationship, he said, doesn’t exist at all agencies.
“It sounds like you’re making some progress, especially at the management level at VA,” Lee said.
In addition, VA said it achieved a major milestone in its ongoing efforts to implement the continuous diagnostics and mitigation program two weeks ago.
The department implemented the tools needed for hardware asset discovery, Cunningham said in his written testimony. The project was four-year effort in partnership with DHS and will give VA visibility to the assets connected to the network, he said.
VA is also in the middle of a 30-month “request for service” effort with DHS, an initiative that Cunningham said will allow the department to improve its identity and access management tools, better manage users on its network and grant special access to select systems.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Nicole Ogrysko is a reporter for Federal News Network focusing on the federal workforce and federal pay and benefits.
Follow @nogryskoWFED


