

More than three years after NASA became the first agency to deploy robotic process automation, the rest of the government has come a long way standardizing the...
Best listening experience is on Chrome, Firefox or Safari. Subscribe to Federal Drive’s daily audio interviews on Apple Podcasts or PodcastOne.
More than three years after NASA became the first agency to deploy robotic process automation, the rest of the government has come a long way standardizing the rollout of additional bots, giving federal employees more time to focus on higher-value work.
Instances of automation more than doubled between fiscal 2019 and 2020, according to a report from the Federal RPA Community of Practice that reviewed the work of 23 agency program offices.
Most agencies, however, have yet to standardize security and credentialing bots in a way that would maximize their efficiency or give rise to the proliferation of unattended bots.
“RPA programs are meeting security requirements, but these requirements continue to limit program capabilities and impact,” the report states.
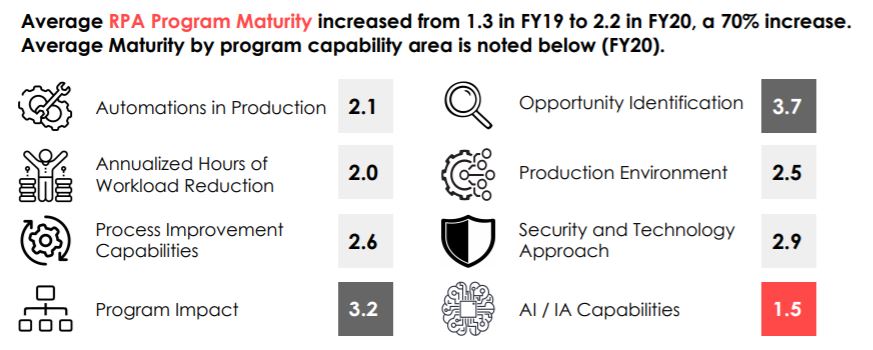
The community of practice found RPA program maturity “increased significantly” last year. On a five-point scale, the average RPA program in 2020 earned a 2.2 score – a 70% increase from the previous year.
The scorecard shows agencies made the most improvement in identifying new opportunities to apply automation and field RPA bots through a centralized process.
Some agencies have taken a big step and fielded unattended bots that work around the clock. NASA’s Shared Services Center (NSSC) started work on an RPA security plan last year to set unattended bots in motion, and the Patent and Trademark Office is looking at moving bots off employees’ laptops and onto a centralized platform.
The Department of Veterans Affairs, meanwhile, is standing up an enterprise-wide platform to standardize how the agency vets and reviews bots.
“We’ve actually started to integrate security and privacy into the bot development lifecycle, to ensure that as the bot is developed and deployed, we’ve already met the requirements that you need to actually get that thing deployed and implemented into the internal environment,” Dirk Barrineau, a VA IT specialist, said Tuesday during a webinar hosted by the Advanced Technology Academic Research Center (ATARC).
Jim Walker, the chief technology officer at UiPath and a former NSSC executive who oversaw its RPA strategy, said the agency has come a long way in standardizing the way it credentials bots and grants them access to agency networks and data.
NSSC’s first bot, George Washington, received login credentials just like any employee would, and handled routine financial management tasks. But when the agency saw more opportunities to automate, it chose to field a second bot, John Adams, rather than give Washington multiple credentials.
“For us at the time, it was just smarter to have two separate bots, two licenses, so that one did accounts receivable and one did accounts payable,” Walker said.
While agency RPA programs have demonstrated greater maturity in the past year, Jon Walden, CTO for the Americas at Blue Prism, said government – specifically on the credentialing – still has some catching up to do with industry.
“Corporate has recognized that a digital worker, just by its nature, is probably going to gradually get more and more rights. Most organizations start off very secure – they have access to this one system. But then, when you add something else for the digital worker to do .. their rights have to be expanded,” Walden said.
The RPA community of practice found most agency RPA programs have created strategies for approving individual bots, but the report found that this step was a “significant hurdle for early RPA adopters.”
Its report found that more agencies have adopted a Center of Excellence (CoE) approach to fielding bots, in which a single hub manages customers across the entire organization.
Chief information officers vet new software before it’s added to an agency’s network, but Walker said the task of identifying work processes to automate should happen at the CoE level.
“I would not want you to think that a process being automated has to go to your CIO for change management. I believe they’re at your CoE, where the software has already been approved to work. So what you’re testing is this function that we did manually performing the way we expected it to perform in an automated fashion,” Walker said.
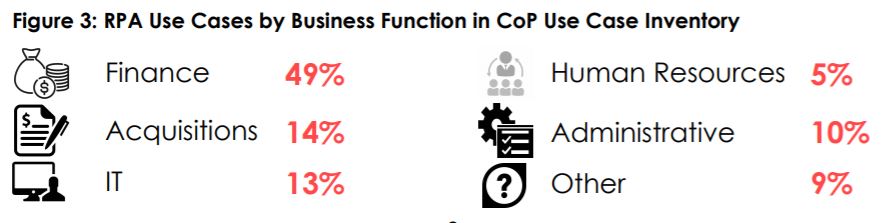
Nearly half of all RPA deployments tracked by the community of practice are used for financial management, while only 13% of automation use cases are geared toward IT.
Former Department of Homeland Security Chief Information Security Officer Paul Beckman, now the CISO at Consolidated Nuclear Security, said RPA could prove to be a “doubled-edge sword” in terms of cybersecurity and insider threats.
Increased automation, he said, gives insider threat analysts a better picture of incoming threats, but on the other hand, bots could increase the scope of sensitive information a malicious insider could pull from an agency’s networks.
“The amount of data one can collect and exfiltrate is probably limited because it’s a human doing it, but when you enable an RPA to go collect and exfiltrate information at machine speed, it’s something that worries me,” Beckman said.
Expanding the scope of what bots can access may raise red flags from agency CISOs, but Walker said agencies should ensure that bots – much like employees – only receive the network access they need to do their jobs.
“Think of them as teleworkers, and how does a teleworker traverse boundaries? They traverse boundaries with good, auditable credentials. They have single sign-on, they use VPN, they have roles-based access. Your automation – attended or unattended bot – needs to have that at its very core.” he said. “These aren’t anything special, they’re emulating existing processes.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jory Heckman is a reporter at Federal News Network covering U.S. Postal Service, IRS, big data and technology issues.
Follow @jheckmanWFED


