Federal CISO DeRusha: FISMA report details a key part of cyber roadmap
Chris DeRusha, the federal chief information security officer, said the annual Federal Information Security Management Act (FISMA) report to Congress further...
Agencies faced 30,819 cyber incidents in fiscal 2020, an 8% increase over the previous year.
Email phishing and website authentication continue to be among the biggest attack vectors hackers are using to get to agency networks and data.
But despite this escalation and ever-growing challenge, the annual Federal Information Security Management Act (FISMA) report to Congress, highlights real progress, particularly in how agencies are managing cyber risk.
Chris DeRusha, the federal chief information security officer, said the increase is significant after seeing decreases over the last few years. But he said agencies and industry shouldn’t get too excited over the increase either as agencies are getting better at detecting cyber incidents too.
“As we have observed over the past few months, the scope and severity and scale of some of these attacks was quite dramatically up. That is really driving this sense of urgency and focus that we have to address that,” DeRusha said on Ask the CIO. “When you look at the overall number of incidents in the federal report, though, it is also important to point out that something like 97% are really in that low category of either hadn’t been substantiated or considered to be inconsequential events, maybe non-events, or just any low level of severity. There’s really more around that 3% range of instances that really needs to be investigated and looked into and may have had some level of impact in that scale from a major all the way up to a major incident or something far less severe.”
The report shows incidents suffered by non CFO Act agencies dropped by about 50% in 2020 as compared to 2019, while CFO Act agencies saw almost 3,000 more attacks.
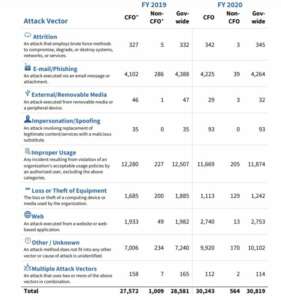
“Improper Usage remains the most common vector with 11,874 incidents (nearly 39%). The prevalence of this vector indicates that agencies have processes or capabilities that detect when a security policy is being violated, but lack automated enforcement or prevention mechanisms,” the report states. “The ‘other/unknown’ vector was the second most common vector with 10,102 incidents (about 33%). The prevalence of this attack vector suggests additional steps should be taken to ensure agencies appropriately categorize the vector of incidents during reporting. The Office of Management and Budget and the Cybersecurity and Infrastructure Security Agency will continue to work with agencies to improve the quality of incident reporting data to ensure the vectors of incidents are appropriately categorized.”
Agencies also reported six major incidents in 2020, including the Justice Department’s Justice Security Operations Center (JSOC), which detected an intrusion of the Detention Services Network (DSNet) system. Justice said names, addresses, birth dates, social security numbers, FBI numbers and “alien numbers” of current and former prisoners were successfully electronically exfiltrated through an SQL injection attack.
The Justice example along with those from the Defense Department and three at FEMA demonstrate why the administration is pushing agencies toward zero trust and other advanced cyber approaches.
President Joe Biden signed the cybersecurity executive order in early May laying out dozens of new steps and deadlines for how agencies should shore up their networks and data, ranging from creating a plan in 60 days to move to a zero trust architecture, to encrypting data at rest and data in transit within the next six months.
DeRusha, who became federal CISO in January, said the FISMA report to Congress further highlights why the administration is focusing on some key areas to improve.
“We’re also taking a higher order picture and looking at what do we need to do to ensure that agencies have awareness about cyber incidents that are affecting their mission by ensuring we’re changing contract requirements, making sure we are developing options to implement endpoint detection response tools for agencies to discover threats and ensuring that we’re focused on developing secure software and that agencies are sharing secure software,” he said. “We also are developing incident response and recovery and development playbooks and best practices. We are standing up for the first time an incident review board so that we can take the best lessons learned from these events and ensure that everyone understands. It’s all about managing the holistic risk picture.”
Full modern security stack needed
He said the last six months particularly, which are not included in the FISMA report to Congress, agencies and industry have learned just how sophisticated attackers have become and the lack of widespread modern security practices is making defending networks and data more difficult.
“We need to have layered defenses and start developing zero trust architecture in a faster way across federal government to ensure that we’re having the full modern security stack in place and really not trusting on the edges and just ensuring that we are continuing to assess the devices and then the humans accessing data, so that we are really protecting from the techniques, tactics and procedures that we’re starting to see,” DeRusha said.
While DeRusha acknowledges that zero trust has become a bit of a buzzword in the industry, he said it’s also a good way to organize concepts as part of the IT modernization journey.
“Security modernization and zero trust go hand in glove. It’s a paradigm shift in how we think about securing our infrastructure networks in our data, and it’s getting to be more about more data-centric approaches,” he said. “It’s really ensuring that we’re not just focused on perimeter security, that we’re making every device and every person we authenticate into whatever you’re trying to access and to potentially monitor that and ensure that it is the appropriate device holder or person that is accessing the resource.”
DeRusha said the broader point of the administration’s focus on zero trust is as much about culture change as it’s about the tools or capabilities.
“The broader point of the cultural journey is changing how we work in IT cones and in security cones, and then how we interact with the rest of employees and organizations,” he said. “It’s starting to pervade out of IT cones, and really get into the business side and mission side of agencies in understanding that cybersecurity is really about managing risk in the digital age. That’s a journey we’re on. That’s an educational process that we’re on with agency executives, which is why it’s so crucial for OMB to have cybersecurity baked into the President’s Management Agenda, cross agency priority goals and other mechanisms. We have to drive and measure risk management across federal agencies.”
He said the CISO Council continues to focus on applying better risk management metrics and sharing best practices across the community.
“The FISMA report does a really good job of showing where the government’s focused. It can tell you a lot about the priorities that we’ve got. It often signals a direction strategically for where we’re trying to head and really gives you a sense of where agencies are doing well, and then where they may still have some gap areas and could use some support or will need continued investment,” DeRusha said. “We also try to put the data on incidents and other things in a way that is digestible, and can help understand the trends. The security trends and attack trends that we’re seeing on federal networks is another useful take away from it. I think you can anticipate to see even more of our policy direction framed out in next year’s FISMA report as well.”
DeRusha said for 2021 his top priorities first and foremost include implementing the requirements under the cyber EO. Along with the dozens of initiatives from the order, he said using the Technology Modernization Fund to help drive security upgrades is another key focus area.
“This is about evolving our management model from TMF 1.0 to a 2.0. To get the billion dollars changes a lot about what we need to do with program management and how the board reviews and ensures that we’re getting high quality projects through and our focus there is also heavily on security. It’s also about modernizing high priority systems, public facing services, scalable cross government services, the theme that really resonates throughout is ensuring that we’re getting security outcomes from these investments as well as the TMF,” he said.
The other big item issue for DeRusha is working with Congress to modernize the FISMA law. The last time lawmakers tackled the underlying legislation for federal cybersecurity was 2014. During a March hearing, Sen. Rob Portman (R-Ohio), ranking member of the Homeland Security and Governmental Affairs Committee, said he plans on looking at how best to reform FISMA and other laws, specifically adding more accountability for cybersecurity.
“We see a lot of value in it. We’re looking forward to that opportunity to really think through how we’re assessing performance of agencies, and how we can potentially do some things differently to drive progress based on the threats and the sense of urgency that we’re feeling based on the moment,” DeRusha said.
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED








