
Tougher security, more taxpayer transparency a ‘delicate balance’ at IRS
IRS Commissioner John Koskinen said his agency is working to both strengthen the security around taxpayer information, while also allowing taxpayers access to their...
The Internal Revenue Service must do more to improve the security of taxpayer information from cyber threats, a series of federal audits says, but agency officials say they need congressional help to do it.
With Tax Day one week away, a panel of IRS and federal oversight officials appeared April 12 before the Senate Finance Committee to tell Congress what the IRS has done and needs to do to stay ahead of cyber threats while supporting taxpayers.
IRS Commissioner John Koskinen said his agency is working to maintain “a delicate balance.”
“We need to keep the criminals out while letting the legitimate taxpayers in,” Koskinen said. “Our goal is to have the strongest possible authentication processes for our online services while maintaining the ability of taxpayers to access their data and use IRS services online.”
One way Congress can help, Koskinen said, is by renewing a special hiring authority called “streamlined critical pay authority.”
Koskinen said the agency currently has only 13 or 14 employees in 40 positions that were made available under the authority.
“Ten are senior IT people working on cybersecurity online services. By this time next year they’ll be gone,” Koskinen said. “Replacing them is very challenging for us.”
While the IRS has challenges that might appeal to a cybersecurity professional, those professionals are getting recruited elsewhere, or being recruited while waiting for the IRS to go through a three to six month application approval period, Koskinen said.
“Without the authority which we haven’t had since 2013, it’s made it almost impossible to recruit and retain at the level we need to,” Koskinen said.
Asked by Sen. Maria Cantwell (D-Ind.) whether that affects cybersecurity, Koskinen said his agency’s head of cybersecurity left rather than waiting out his term.
“I think this is an issue for all of our government … to continue to make sure we have the best technology people, which is challenging for a whole lot of reasons,” Cantwell said. “I think this authority to help you streamline that hiring and pay is something we need to do as quickly as possible.”
Beefing up the IRS
Gene Dodaro, comptroller general of the U.S., said another authority the IRS needs is one that allows it to regulate paid tax return preparers, echoing a report the Government Accountability Office published in 2014.
“They need to set minimum standards, they should go through due process procedures just as you would with any regulatory approach, and set the standards and enforce those standards,” Dodaro said. “This is a particular problem because of the IRS’ resource levels. If we’re going to rely on paid tax preparers to largely carry out a very important function on behalf of the government, then we need to make sure they are properly carrying out their responsibilities. And they could greatly leverage their activities as opposed to a need to continually beef up the IRS.”
But Dodaro also brought another GAO report to the April 12 hearing.
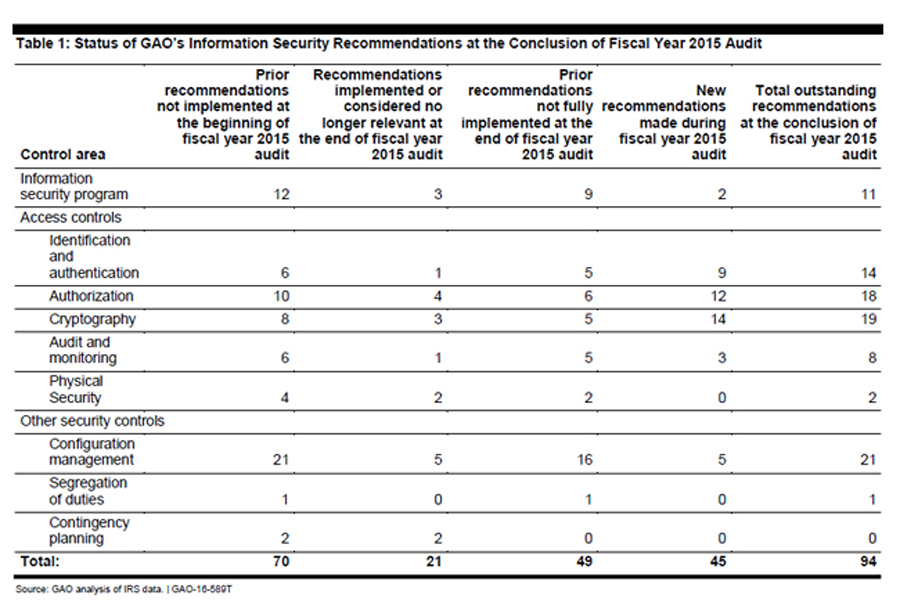
In it, GAO adds 45 new recommendations for the IRS, bringing the total number of outstanding recommendations to 94 for the tax agency, that will help “improve its information security controls and the implementation of its agency-wide information security programs,” as well helping the IRS fight identity theft refund fraud.
 According to numbers provided by the IRS, the agency paid out about $3.1 billion in fraudulent tax refunds.
According to numbers provided by the IRS, the agency paid out about $3.1 billion in fraudulent tax refunds.
Dodaro said the GAO’s most recent audit found that while the IRS has worked to put more controls over its financial and tax processing systems, “numerous weaknesses we identified were due to inconsistent application of their information security program across the IRS.”
Among these weaknesses were easily guessable passwords that in some cases gave access to taxpayer accounts, and the IRS granting privileges beyond what an employee needed to do their job. GAO also found that key systems were not always encrypted when they should be, nor were software patches, Dodaro said.
“One area we were concerned about with this most recent audit is in 28 instances IRS asserted that it had implemented our recommendations … but in our subsequent testing, we found that in nine of those 28 instances indeed the problem had not been fixed,” Dodaro said. “So we’re very concerned about that.”
Sen. Ron Wyden (D-Ore.) also defended the use of critical pay authority and regulation of tax preparers, saying it was unacceptable that social media and email accounts in the private sector could be more secure from hacking than the “troves of taxpayer data.”
“While many tax preparers are honest practitioners, we know that there are always some bad apples in the barrel,” Wyden said. “It’s still my view that people handling sensitive taxpayer information should have to me what are minimum standards and that the committee should vote to require it. It’s open season for hackers to steal money and data from hardworking Americans, and congressional action should not make this situation worse.”
Weaknesses and risk acceptance
Senate Finance Committee Chairman Orrin Hatch (R-Utah) said he was disappointed that the IRS had not implemented recommendations from the Treasury Inspector General for Tax Administration (TIGTA), and referenced the attack on IRS e-filing PIN numbers earlier this year.
Inspector General J. Russell George said while there could be no guarantee a breach would not have occurred, had those recommendations been implemented “it would have been much more difficult for that to have happened.”
Since fiscal 2011 when TIGTA set IRS security as a top priority, it has provided audits and recommendations for the IRS. George said in his testimony that 23 recommendations from 14 TIGTA audits are still yet to be implemented. They address “weaknesses related to connections with external parties, continuous efforts to monitor information security, implementation of the Homeland Security Presidential Directive 12 initiative [involving federal security credentials] and information technology asset management.”
Michael McKenney, TIGTA deputy inspector general for audit, said the IRS needs to address changing its authentication process to a multi-factor one, and he also added that one of the agency’s biggest concerns was the IRS’ willingness to accept risk within the cyber realm.
“The agency itself when it decides to accept risk — it’s unavoidable — but should be kept to a minimum,” McKenney said. “And when they do accept risk they should thoroughly document … rationale and what they will eventually be able to do to overcome those risks.”
Copyright © 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.




