Another cyber executive order deadline looming for agencies
The Office of Management and Budget issued a new memo outlining four maturity levels for cyber event logging.
Best listening experience is on Chrome, Firefox or Safari. Subscribe to Federal Drive’s daily audio interviews on Apple Podcasts or PodcastOne.
The Office of Management and Budget is giving agencies 60 days to assess how well they log cybersecurity incident data against a new maturity model released today.
As part of that review, agencies must also identify gaps, develop plans to mitigate those problems and submit cost estimates to OMB’s Resource Management Office (RMO) and Office of the Federal Chief Information Officer (OFCIO).
“Recent events, including the SolarWinds incident, underscore the importance of increased government visibility before, during, and after a cybersecurity incident. Information from logs on federal information systems (for both on-premises systems and connections hosted by third parties, such as cloud services providers (CSPs) is invaluable in the detection, investigation, and remediation of cyber threats,” wrote OMB’s acting director Shalanda Young in a new memo to federal leaders.
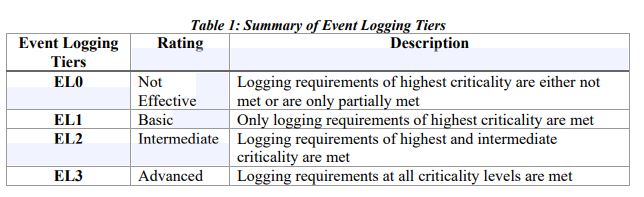
OMB outlined four maturity levels starting with event logging 0 (EL0) as least mature to EL3 as having a mature program that agencies should assess themselves against.
After the 60-day review, agencies then have 18 months to reach EL2 and 24 months to reach EL3.
“These tiers will help agencies prioritize their efforts and resources so that, over time, they will achieve full compliance with requirements for implementation, log categories, and centralized access. Agencies should also prioritize their compliance activities by focusing first on high-impact systems and high value assets (HVAs),” the memo stated.
The maturity model and implementation requirements are part of the mandates from President Joe Biden’s May executive order on cybersecurity.
The EO called on agencies to improve their investigative and remediation capabilities, particularly around “logging, log retention and log management, with a focus on ensuring centralized access and visibility for the highest-level enterprise security operations center (SOC) of each agency.”
This is the second memo in August detailing how agencies should meet EO requirements. The Aug. 10 memo gave agencies 60 days to identify critical on-premise software and then another 12 months to secure those applications.
Among the other cyber EO deadlines coming up include the requirement for the secretary of Defense, secretary of Homeland Security and the OMB director to establish procedures for the Defense Department and DHS to immediately share DoD Incident Response Orders or DHS Emergency Directives and Binding Operational Directives, including cross-adoption, and for all agencies to update their memoranda of agreement with the Cybersecurity and Infrastructure Security Agency (CISA) in DHS for the continuous diagnostics and mitigation (CDM) program.
“OMB has a number of tasks to write policy to ensure that agencies have clear guidance on all the various sections of the EO, and that we can establish those over a multi-year cycle and match with the budget side the appropriate funding to implement,” said Chris DeRusha, the federal chief information security officer during a Aug. 4 event sponsored by the Center for Cybersecurity Policy and Law and NIST.
By improving the way agencies log cyber events, the administration hopes to enhance the ability of CISA and agencies to detect intrusions, mitigate those in progress and determine the extent of an incident after the fact.
CISA will be at the center of this effort.
OMB says in the memo that CISA will be:
- Deploying teams to advise agencies in their assessment of logging capabilities.
- Developing and publishing tools, in coordination with the FBI, to help agencies facilitate their assessment of logging maturity across the organization.
OMB also is establishing time frames for how long agencies should keep the log data. For the majority of the logs, agencies should store them for 12 months in “active storage” and 18 months in “cold storage,” which minimizes costs while still allowing some level of access and use.
CISA also is piloting improved logging capabilities in the cloud. It will use some of the $650 million it received under the American Rescue Plan Act to stand up a secure, threat hardened cloud environment that will include improved logging tools.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Jason Miller is executive editor of Federal News Network and directs news coverage on the people, policy and programs of the federal government.
Follow @jmillerWFED





