Energy Dept joins industry partners in space for quantum technology
…
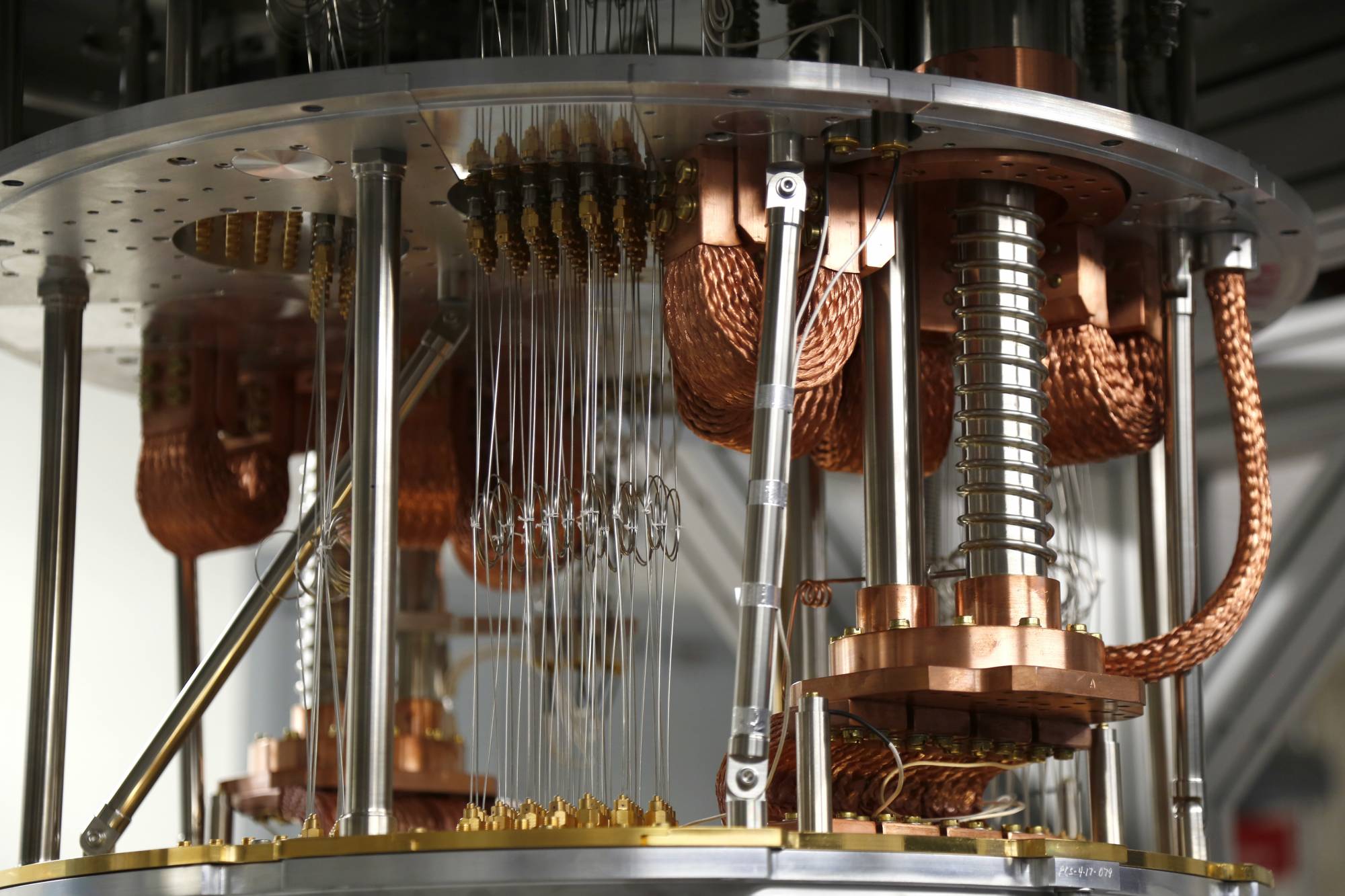

Agencies need to act now to protect their data from the coming threat of quantum computing
Also in today’s Federal Newscast, the Biden administration takes action to make sure public research results are available to the public. And the Air Force…
The theory is quantum will be so powerful it will easily crack encryption algorithms conventional computers would take thousands of years to crack.