Discussing federal compliance with mandated standards isn’t a thrilling prospect for most businesses. But since the Defense Department relies on over 300,000 ...
The new standard is rolling out, with many government contractors wondering how they can achieve compliance.
Discussing federal compliance with mandated standards isn’t a thrilling prospect for most businesses. But since the Defense Department relies on over 300,000 companies and subcontractors to maintain operations, it’s of massive import.
While the companies that support DoD often see compliance standards as cumbersome and confusing, from the government’s perspective, maintaining high standards and best practices is a matter of national security necessary to combat online threats from foreign actors.
By now, you’ve likely heard that a new framework is coming out that will apply to all contractors working with the DoD. The Cybersecurity Maturity Model Certification (CMMC) is expected to roll out during the first half of 2021. Think of it as something that combines and replaces the existing compliance standards like NIST SP 800-171, 48 CFR 52.204-21, DFARS clause 252.204-7012 — and others — while expanding their security and reporting standards.
But what does that really mean for contractors? We can boil it down to two core concepts:
Starting in the spring of 2021, DoD will begin a staggered rollout, requiring CMMC compliance for RFIs and RFPs. By 2026, bidding on any DoD contract will require CMMC compliance.
You’re no longer allowed to self-report. To be certified as compliant, you have to pass an audit by a certified third-party assessment organization (C3PAO). As of yet, there are no qualified assessors; the CMMC-AB website states that in September 2020, training for the initial group had begun.
To put it plainly, if you’re a DoD contractor, you need to start implementing the CMMC now, and then find a C3PAO to verify that you meet its standards as soon as qualified assessors are trained.
Analyzing the standards
Many contractors are looking at the new guidance and wondering where to even start. Like most government compliance standards, CMMC is exhaustive and detailed. The good news is, however, that although you should understand what’s required of you, you don’t need to memorize every facet of the certification model. Because you’re going to have to pass a third-party assessment, it’s a good idea to have a security partner help you implement the new standards. It’s their job to comprehensively understand the framework and help you implement it, whereas your business has other pressing concerns.
CMMC Maturity Levels
The CMMC lays out best practices into 17 groups, which they call domains. Within each domain, there are 43 distinct capabilities. Most companies working with the DoD don’t need to demonstrate all of these capabilities, but the more you meet, the higher the maturity level you will meet.
The domains and capabilities help assess which level of security a contractor meets. There are five distinct categories, which they call maturity levels. To reach the higher levels, you need to first adhere to all of the requirements of each previous level.
Level 1: Basic Cyber Hygiene — Limited or inconsistent processes; any cybersecurity practices are performed as needed. Details 17 practices to protect federal contract information (FCI) corresponding to the requirements specified in 48 CFR 52.24-21 and NIST SP 800-171.
Level 2: Intermediate Cyber Hygiene — Cybersecurity practices are documented. This includes 55 additional cyber hygiene practices from NIST SP 800-171 as well as others and references the protection of controlled unclassified information.
Level 3: Good Cyber Hygiene — Cybersecurity processes are maintained and followed. An additional 58 cyber hygiene practices from NIST SP 800-171 and others for a total of 130. Paramount in the practices is the adoption of multi-factor authentication (MFA).
Level 4: Proactive — Cybersecurity processes are reviewed and improved throughout the company and have adequate resources. Twenty-six additional cyber hygiene practices from Draft NIST SP 800-171B, for a total of 156 hygiene practices.
Level 5: Advanced/Progressive — In addition to level 4 best practices, cybersecurity processes undergo continuous improvement throughout the company. The highest level includes 15 more practices from Draft NIST SP 800-171B and other standards, bringing the total number of cyber hygiene practices to 171.
Where does your company fit in?
Of course, if you’re a DoD contractor, the above begs the question, “which level do I need?” Because the government hasn’t come out and explicitly stated which contractors will require a certain maturity level, it’s a bit of a guessing game, but they’ve left clues. What we do know for certain is that in order to level up, you have to meet all of the requirements of each previous standard.
Levels one and two appear fairly easy to achieve (although they still require C3PAO). You’ll need to perform (ML1) and document (ML2) the basic cyber hygiene requirements described. Meeting these requirements should be relatively straightforward, but may significantly limit the types of contracts for which you can bid, as you’re only allowed to respond to RFPs at or under the level you have demonstrated.
On the upper end, levels four and five will deal with the most sensitive information, and therefore contain the most rigorous standards. To achieve these levels of certification, you need to demonstrate that you can effectively mitigate advanced persistent threats via the adoption of tactics, techniques, and procedures. If your business previously relied on contracts with the DoD that required you to handle highly sensitive data, you’ll likely need to get certified in one of these higher maturity levels.
It’s likely that many contractors will opt for level three. Its security requirements are significantly enhanced from the first two levels, but nowhere near levels four and five. If you were previously required to comply with NIST SP 800-171 Rev 1, you’ll want to aim for maturity level three or above. Level three requires the implementation of MFA and identity security for your company and its subcontractors. While achieving this requires some investment, it shouldn’t be a deterrent. Even without the pressure from government compliance standards, most companies in the private sector are already implementing MFA solutions because they’re essential in protecting company information and systems.
How you can get started
Figuring out exactly what maturity you want to achieve is the first step. DoD’s website explaining the model can be found here. Like many government websites, however, it isn’t the easiest to navigate and discern.
The CMMC Accreditation Body has a website containing a trove of information for everyone within the contractor ecosystem, and is laid out in a manner which is easier to understand.
Once you’ve decided on the maturity level you’ll need to achieve, you need to set out to implement the requirements. Because you need to strictly adhere to these standards and pass a third-party audit, it’s a good idea to find a security partner to ensure that you’ve correctly implemented your security regimen. Being CMMC compliant is going to be required to respond to RFPs in the near future. The maturity level that you’re trying to reach will dictate what type of outside resource you need to help get your systems and procedures in place.
In general, you should look for a security partner who has a history of working with government contractors to pass previous audits, particularly with regards to NIST SP 800-171 Rev 1. They should have case studies or documentation highlighting their work in this area.
Because multi-factor authentication is a large part of maturity level three, if you’re aiming for that threshold, you’ll want to find an experienced MFA partner who can roll out a solution without a major disruption to your day-to-day activities. It’s likely that you can find a company who is well-versed in NIST SP 800-171 audits and can implement MFA throughout your organization. Because everyone — including you subcontractors — needs to be utilizing MFA, you may want to look for a company that can offer varied levels of access or privilege with your credentials.
You’ll also want to find a vendor who offers a scalable solution. The framework, your technologies, and the maturity level you wish to achieve are all items that could change in the future, as are the outside threats that make the CMMC necessary. You should be comfortable with the company you hire, because it’s likely you’ll need some form of ongoing support.
A new certification model, with new requirements, can be daunting. There’s so much information to take in. Deadlines are fast approaching—and if your company depends on working with the DoD—correct understanding and implementation are essential to the future of your business. But you shouldn’t feel overwhelmed. By reviewing the standards now, assessing your needs, and looking for outside assistance in ensuring compliance, you’ll be well on your way to a painless transition and passing your audit by a C3PAO. Taking care of all of this now will put you in a great position in the marketplace, as you’ll be able to bid on RFPs that companies who drag their feet can’t.
Jerome Becquart is the chief operating officer of Axiad, an identity and access management solutions company.
Ready for CMMC? Here’s how you can get there
Discussing federal compliance with mandated standards isn’t a thrilling prospect for most businesses. But since the Defense Department relies on over 300,000 ...
The new standard is rolling out, with many government contractors wondering how they can achieve compliance.
Discussing federal compliance with mandated standards isn’t a thrilling prospect for most businesses. But since the Defense Department relies on over 300,000 companies and subcontractors to maintain operations, it’s of massive import.
While the companies that support DoD often see compliance standards as cumbersome and confusing, from the government’s perspective, maintaining high standards and best practices is a matter of national security necessary to combat online threats from foreign actors.
By now, you’ve likely heard that a new framework is coming out that will apply to all contractors working with the DoD. The Cybersecurity Maturity Model Certification (CMMC) is expected to roll out during the first half of 2021. Think of it as something that combines and replaces the existing compliance standards like NIST SP 800-171, 48 CFR 52.204-21, DFARS clause 252.204-7012 — and others — while expanding their security and reporting standards.
Learn how federal agencies are preparing to help agencies gear up for AI in our latest Executive Briefing, sponsored by ThunderCat Technology.
But what does that really mean for contractors? We can boil it down to two core concepts:
To put it plainly, if you’re a DoD contractor, you need to start implementing the CMMC now, and then find a C3PAO to verify that you meet its standards as soon as qualified assessors are trained.
Analyzing the standards
Many contractors are looking at the new guidance and wondering where to even start. Like most government compliance standards, CMMC is exhaustive and detailed. The good news is, however, that although you should understand what’s required of you, you don’t need to memorize every facet of the certification model. Because you’re going to have to pass a third-party assessment, it’s a good idea to have a security partner help you implement the new standards. It’s their job to comprehensively understand the framework and help you implement it, whereas your business has other pressing concerns.
CMMC Maturity Levels
The CMMC lays out best practices into 17 groups, which they call domains. Within each domain, there are 43 distinct capabilities. Most companies working with the DoD don’t need to demonstrate all of these capabilities, but the more you meet, the higher the maturity level you will meet.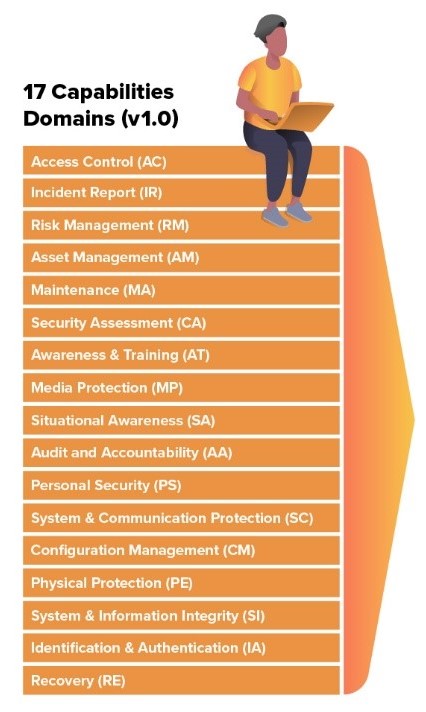
The domains and capabilities help assess which level of security a contractor meets. There are five distinct categories, which they call maturity levels. To reach the higher levels, you need to first adhere to all of the requirements of each previous level.
Of course, if you’re a DoD contractor, the above begs the question, “which level do I need?” Because the government hasn’t come out and explicitly stated which contractors will require a certain maturity level, it’s a bit of a guessing game, but they’ve left clues. What we do know for certain is that in order to level up, you have to meet all of the requirements of each previous standard.
Read more: Commentary
Levels one and two appear fairly easy to achieve (although they still require C3PAO). You’ll need to perform (ML1) and document (ML2) the basic cyber hygiene requirements described. Meeting these requirements should be relatively straightforward, but may significantly limit the types of contracts for which you can bid, as you’re only allowed to respond to RFPs at or under the level you have demonstrated.
On the upper end, levels four and five will deal with the most sensitive information, and therefore contain the most rigorous standards. To achieve these levels of certification, you need to demonstrate that you can effectively mitigate advanced persistent threats via the adoption of tactics, techniques, and procedures. If your business previously relied on contracts with the DoD that required you to handle highly sensitive data, you’ll likely need to get certified in one of these higher maturity levels.
It’s likely that many contractors will opt for level three. Its security requirements are significantly enhanced from the first two levels, but nowhere near levels four and five. If you were previously required to comply with NIST SP 800-171 Rev 1, you’ll want to aim for maturity level three or above. Level three requires the implementation of MFA and identity security for your company and its subcontractors. While achieving this requires some investment, it shouldn’t be a deterrent. Even without the pressure from government compliance standards, most companies in the private sector are already implementing MFA solutions because they’re essential in protecting company information and systems.
How you can get started
Figuring out exactly what maturity you want to achieve is the first step. DoD’s website explaining the model can be found here. Like many government websites, however, it isn’t the easiest to navigate and discern.
The CMMC Accreditation Body has a website containing a trove of information for everyone within the contractor ecosystem, and is laid out in a manner which is easier to understand.
Once you’ve decided on the maturity level you’ll need to achieve, you need to set out to implement the requirements. Because you need to strictly adhere to these standards and pass a third-party audit, it’s a good idea to find a security partner to ensure that you’ve correctly implemented your security regimen. Being CMMC compliant is going to be required to respond to RFPs in the near future. The maturity level that you’re trying to reach will dictate what type of outside resource you need to help get your systems and procedures in place.
In general, you should look for a security partner who has a history of working with government contractors to pass previous audits, particularly with regards to NIST SP 800-171 Rev 1. They should have case studies or documentation highlighting their work in this area.
Want to stay up to date with the latest federal news and information from all your devices? Download the revamped Federal News Network app
Because multi-factor authentication is a large part of maturity level three, if you’re aiming for that threshold, you’ll want to find an experienced MFA partner who can roll out a solution without a major disruption to your day-to-day activities. It’s likely that you can find a company who is well-versed in NIST SP 800-171 audits and can implement MFA throughout your organization. Because everyone — including you subcontractors — needs to be utilizing MFA, you may want to look for a company that can offer varied levels of access or privilege with your credentials.
You’ll also want to find a vendor who offers a scalable solution. The framework, your technologies, and the maturity level you wish to achieve are all items that could change in the future, as are the outside threats that make the CMMC necessary. You should be comfortable with the company you hire, because it’s likely you’ll need some form of ongoing support.
A new certification model, with new requirements, can be daunting. There’s so much information to take in. Deadlines are fast approaching—and if your company depends on working with the DoD—correct understanding and implementation are essential to the future of your business. But you shouldn’t feel overwhelmed. By reviewing the standards now, assessing your needs, and looking for outside assistance in ensuring compliance, you’ll be well on your way to a painless transition and passing your audit by a C3PAO. Taking care of all of this now will put you in a great position in the marketplace, as you’ll be able to bid on RFPs that companies who drag their feet can’t.
Jerome Becquart is the chief operating officer of Axiad, an identity and access management solutions company.
Copyright © 2024 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.
Related Stories
Defense companies asking for leeway with CMMC compliance
Pentagon reveals first contracts to serve as pathfinders for CMMC
Contractors waiting to see CMMC effect